
We urge organizations to patch Proxylogon (CVE-2021-26855) and related vulnerabilities (CVE-2021-26857, CVE-2021-26858, CVE-2021-27065) in Microsoft Exchange Server and investigate for potential compromise within their networks. Here's how Tenable products can help.
Background
Following Microsoft’s out-of-band advisory for four zero-day vulnerabilities in Microsoft Exchange Server that were exploited in the wild by a nation-state threat actor known as HAFNIUM, multiple reports have emerged that over 30,000 organizations may have been compromised as a result of these flaws. Jake Sullivan, the White House national security advisor, tweeted that the administration is aware of “potential compromises” at U.S. think tanks and defense industrial base entities.
We are closely tracking Microsoft’s emergency patch for previously unknown vulnerabilities in Exchange Server software and reports of potential compromises of U.S. think tanks and defense industrial base entities. We encourage network owners to patch ASAP: https://t.co/Q2K4DYWQud
— Jake Sullivan (@JakeSullivan46) March 5, 2021
The impact of these vulnerabilities is not limited to U.S.-based organizations, as there are reports of compromised entities in the Czech Republic and Norway. We expect more compromised organizations will be identified in the coming days and weeks.
As Chris Krebs, former director of the Cybersecurity and Infrastructure Security Agency (CISA) has said, organizations that exposed Exchange Server to the internet should assume compromise and begin hunting for known indicators.
This is the real deal. If your organization runs an OWA server exposed to the internet, assume compromise between 02/26-03/03. Check for 8 character aspx files in C:\\inetpub\wwwroot\aspnet_client\system_web\. If you get a hit on that search, you’re now in incident response mode. https://t.co/865Q8cc1Rm
— Chris Krebs (@C_C_Krebs) March 5, 2021
How Tenable Can Help
Tenable released version check plugins for Exchange Server 2010, 2013, 2016 and 2019, which can be used to determine which Exchange Server systems are vulnerable in your environment. However, we’ve also produced additional checks that can be used to directly identify vulnerable systems, as well as flagging potential web shells on hosts that may be compromised.
Direct check plugin
Unlike version checks, which may require the use of a credentialed scan, a direct check plugin is designed to test whether or not your Exchange Server instance is vulnerable to the exploit itself. We have released Plugin ID 147171, which can be used for uncredentialed scans of vulnerable Exchange Server instances. Once the scan is complete, the scan output will produce the following result if vulnerable:

In this instance, the Exchange Server is vulnerable to CVE-2021-26855.
Indicators of Compromise (IOC) check plugin
In addition to the direct check plugin, Tenable Research has produced a plugin (147193) that can be used to identify Microsoft Exchange hosts which may have been compromised based on publicly available IOCs. The plugin may produce the following results:

This screenshot shows the plugin returning results of .aspx files which may indicate that the host has been compromised.
Please note that the IOC plugin may flag benign aspx files as suspicious, so we strongly encourage cross-referencing these against known good lists like this one provided by NCC Group, as well as malware databases like VirusTotal, Hybrid Analysis and PolySwarm.
Using YARA rules to scan for hashes and others IOCs
As we noted in our previous blog, IOCs were initially published by Microsoft and Volexity. Volexity provided a set of three YARA rules to identify web shells.
Tenable products provide the ability to perform YARA scanning by supplying a YARA rule. YARA scanning will scan files on the target to determine if any file matches the user provided YARA rules. This feature uses the Directories and Custom Filescan Directories options to determine which files to scan. A file that is successfully matched against a YARA rule generates a "critical" vulnerability in the scan report and the offending file is attached if it is under 5MB.
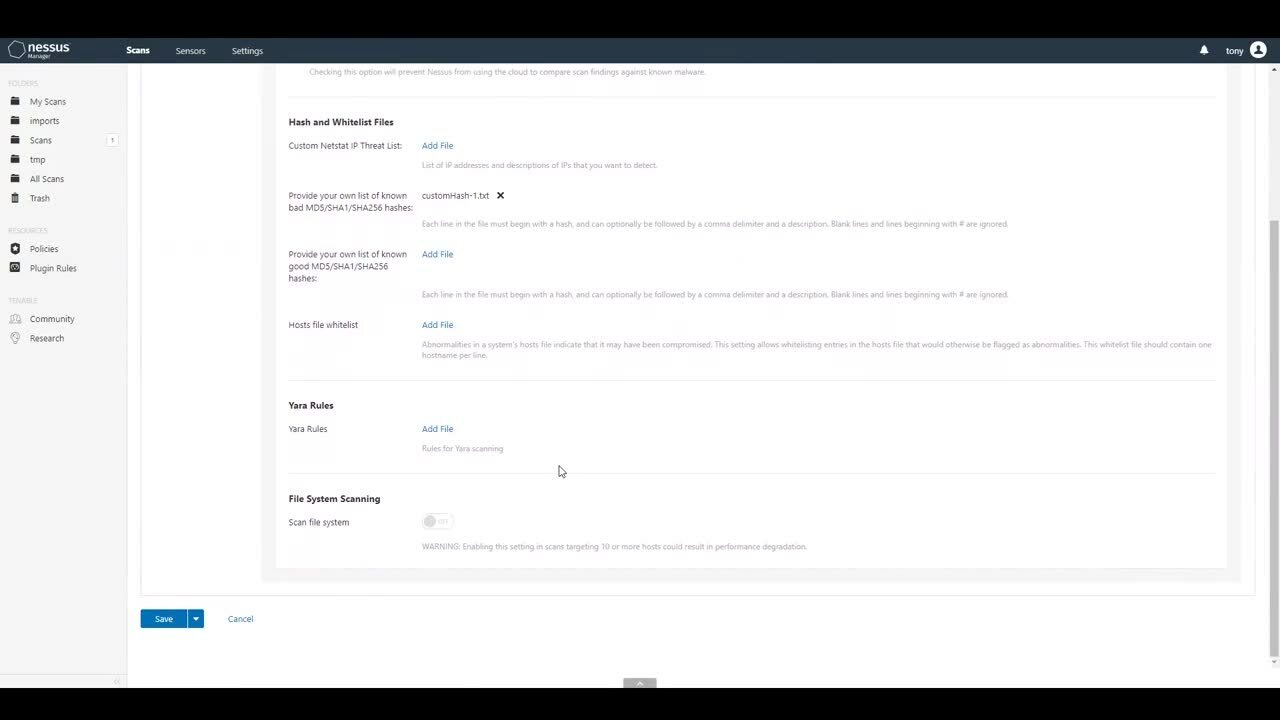
In addition to YARA scanning, customers can also provide a list of known bad hashes (MD5, SHA1 and SHA256) to identify on the target system. Microsoft shared a list of known bad hashes associated with the HAFNIUM campaign.
Prioritize patching and investigate for potential compromise
While we strongly encourage our customers to apply the available patches provided by Microsoft as soon as possible, we also believe it is just as critical to identify the presence of web shells and further compromise within your organization as the attackers may have already established a presence. Applying the available patches plugs the hole, but it doesn’t address the possibility that the attackers are already lurking within your network, which is why hunting for these IOCs is crucial.
Identifying affected systems
The following is a summary of all the checks Tenable Research has produced related to the Exchange Server vulnerabilities.
| Plugin | Plugin Type | Description |
|---|---|---|
| Security Update for Microsoft Exchange Server 2010 SP 3 (March 2021) | Version Check | Identify vulnerable Exchange Server 2010 systems. |
| Security Updates for Microsoft Exchange Server (March 2021) | Version Check | Identify vulnerable Exchange Server 2013, 2016 and 2019 systems. |
| Microsoft Exchange Server Authentication Bypass | Direct Check | Directly identify vulnerable Exchange Server systems uncredentialed. |
| Potential exposure to Hafnium Microsoft Exchange targeting | Local Check | Identify potential web shells in selected directories for further analysis. |
We will update this blog post if we publish any additional plugins related to these events.
Get more information
- Tenable's Blog for Four Zero-Day Vulnerabilities in Microsoft Exchange Server
- Microsoft Blog on HAFNIUM targeting Exchange Servers with 0-day exploits
- Volexity Blog on Operation Exchange Marauder
- CISA Alert (AA21-062A): Mitigate Microsoft Exchange Server Vulnerabilities
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.