Microsoft addresses 67 CVEs in its December 2021 Patch Tuesday release, including a zero-day vulnerability that has been exploited in the wild.
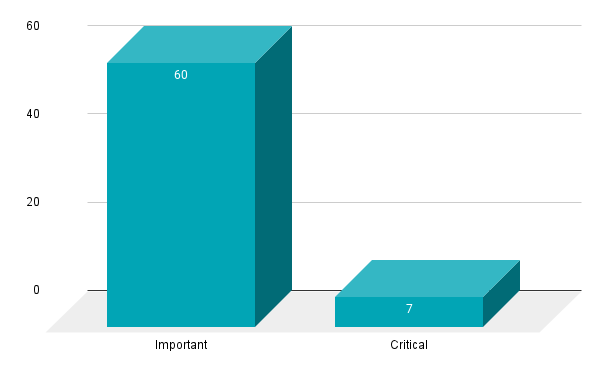
- 7Critical
- 60Important
- 0Moderate
- 0Low
Microsoft patched 67 CVEs in the December 2021 Patch Tuesday release, including seven rated as critical, and 60 rated as important.
This month’s update includes patches for:
- Apps
- ASP.NET Core & Visual Studio
- Azure Bot Framework SDK
- BizTalk ESB Toolkit
- Internet Storage Name Service
- Microsoft Defender for IoT
- Microsoft Devices
- Microsoft Edge (Chromium-based)
- Microsoft Local Security Authority Server (lsasrv)
- Microsoft Message Queuing
- Microsoft Office
- Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft PowerShell
- Microsoft Windows Codecs Library
- Office Developer Platform
- Remote Desktop Client
- Role: Windows Fax Service
- Role: Windows Hyper-V
- Visual Studio Code
- Visual Studio Code - WSL Extension
- Windows Common Log File System Driver
- Windows Digital TV Tuner
- Windows DirectX
- Windows Encrypting File System (EFS)
- Windows Event Tracing
- Windows Installer
- Windows Kernel
- Windows Media
- Windows Mobile Device Management
- Windows NTFS
- Windows Print Spooler Components
- Windows Remote Access Connection Manager
- Windows Storage
- Windows Storage Spaces Controller
- Windows SymCrypt
- Windows TCP/IP
- Windows Update Stack

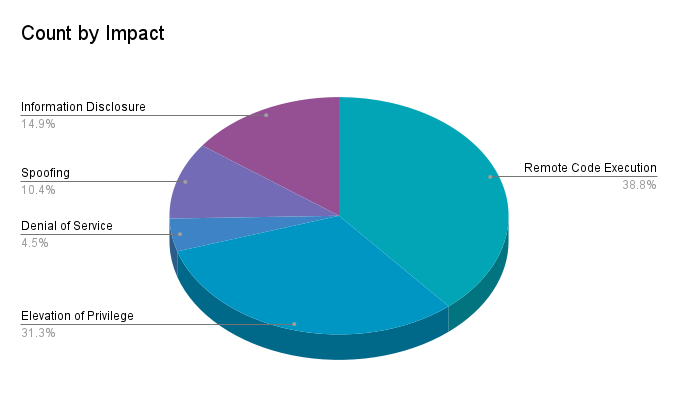
Remote code execution (RCE) vulnerabilities accounted for 38.3% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 31.3%.
CVE-2021-43890 | Windows AppX Installer Spoofing Vulnerability
CVE-2021-43890 is a spoofing vulnerability in the Windows AppX Installer, which is used to install AppX apps on Windows 10 systems. According to reports, this vulnerability has been exploited in the wild. It has been linked to attacks associated with the Emotet/TrickBot/Bazaloader family. To exploit this vulnerability, an attacker would need to convince a user to open a malicious attachment, which would likely be conducted through a phishing attack. Once exploited, the vulnerability would grant an attacker elevated privileges, particularly when the victim’s account has administrative privileges on the system. If patching isn’t an option, Microsoft has provided some workarounds to protect against the exploitation of this vulnerability.
CVE-2021-43215 | iSNS Server Memory Corruption Vulnerability Can Lead to Remote Code Execution
CVE-2021-43215 is a memory corruption vulnerability in the Internet Storage Name Service (iSNS) protocol. The iSNS protocol is used to facilitate communication between iSNS servers and clients. A remote, unauthenticated attacker could exploit this vulnerability by sending a specially crafted request to a vulnerable iSNS server. Successful exploitation would give an attacker remote code execution on the iSNS server. The vulnerability was assigned a CVSSv3 score of 9.8 out of 10 and is rated “Exploitation More Likely” according to Microsoft’s Exploitability Index. Fortunately, iSNS is not installed on Windows systems by default.
CVE-2021-43883 | Windows Installer Elevation of Privilege Vulnerability
CVE-2021-43883 is an EoP vulnerability in Windows Installer. It appears this may address a patch bypass for CVE-2021-41379, publicly disclosed by Abdelhamid Naceri in November. At that time, Naceri also disclosed a separate zero day that does not appear to have been patched. However, Naceri is not credited with CVE-2021-43883, despite being credited with three other CVEs in this month’s release. CVE-2021-43883 received a CVSSv3 score of 7.8 and was marked “Exploitation More Likely,” indicating it is more severe than the original vulnerability. To exploit this vulnerability, an attacker would need to convince the target to open a specially crafted installer in order to gain elevated privileges.
CVE-2021-43240 | NTFS Set Short Name Elevation of Privilege Vulnerability
CVE-2021-43240 is an EoP vulnerability in the New Technology File System (NTFS) set short name function. It received a CVSSv3 score of 7.8 and was rated “Exploitation Less Likely.” Despite being listed as publicly disclosed, discovery of this vulnerability was not credited to anyone. Earlier this year, another EoP flaw in the NFTS, CVE-2021-31956 was exploited as a zero day.
CVE-2021-43905 | Microsoft Office app Remote Code Execution Vulnerability
CVE-2021-43905 is a RCE vulnerability in the Microsoft Office app. It was assigned a CVSSv3 score of 9.6 and is rated “Exploitation More Likely.” To exploit this vulnerability, an attacker would have to create a malicious Microsoft Office document and convince a user through social engineering to open the document. Microsoft says that the Preview Pane is not an attack vector, which means exploitation requires opening the document, not merely previewing it. Because this vulnerability exists in the Microsoft Office app, the patch for this flaw will be distributed through the Microsoft Store as part of an automatic update.
CVE-2021-43233 | Remote Desktop Client Remote Code Execution Vulnerability
CVE-2021-43233 is a RCE in the Remote Desktop Client that received a CVSSv3 score of 7.5. Given past attacks against Remote Desktop Protocol (RDP), it is no surprise that Microsoft rated this “Exploitation More Likely.” Exploiting this flaw would require a vulnerable target to connect to a malicious RDP server. Successful exploitation would allow an attacker to execute arbitrary code on the machine of the connected client.
CVE-2021-41333 | Windows Print Spooler Elevation of Privilege Vulnerability
CVE-2021-41333 is an EoP vulnerability in Windows Print Spooler that received a CVSSv3 rating of 7.8 and was marked “Exploitation More Likely.” Discovery of this vulnerability is credited to Abdelhamid Naceri with Trend Micro Zero Day Initiative, who is credited with two other vulnerabilities patched this month, and James Forshaw of Google Project Zero. This is just the latest in a series of vulnerabilities disclosed in Windows Print Spooler this year. Given the mass exploitation of prior Print Spooler vulnerabilities, users should apply these patches as soon as possible.
Tenable Solutions
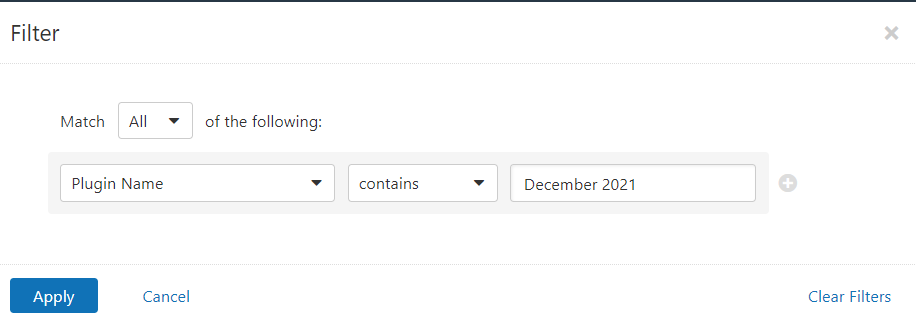
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains December 2021.
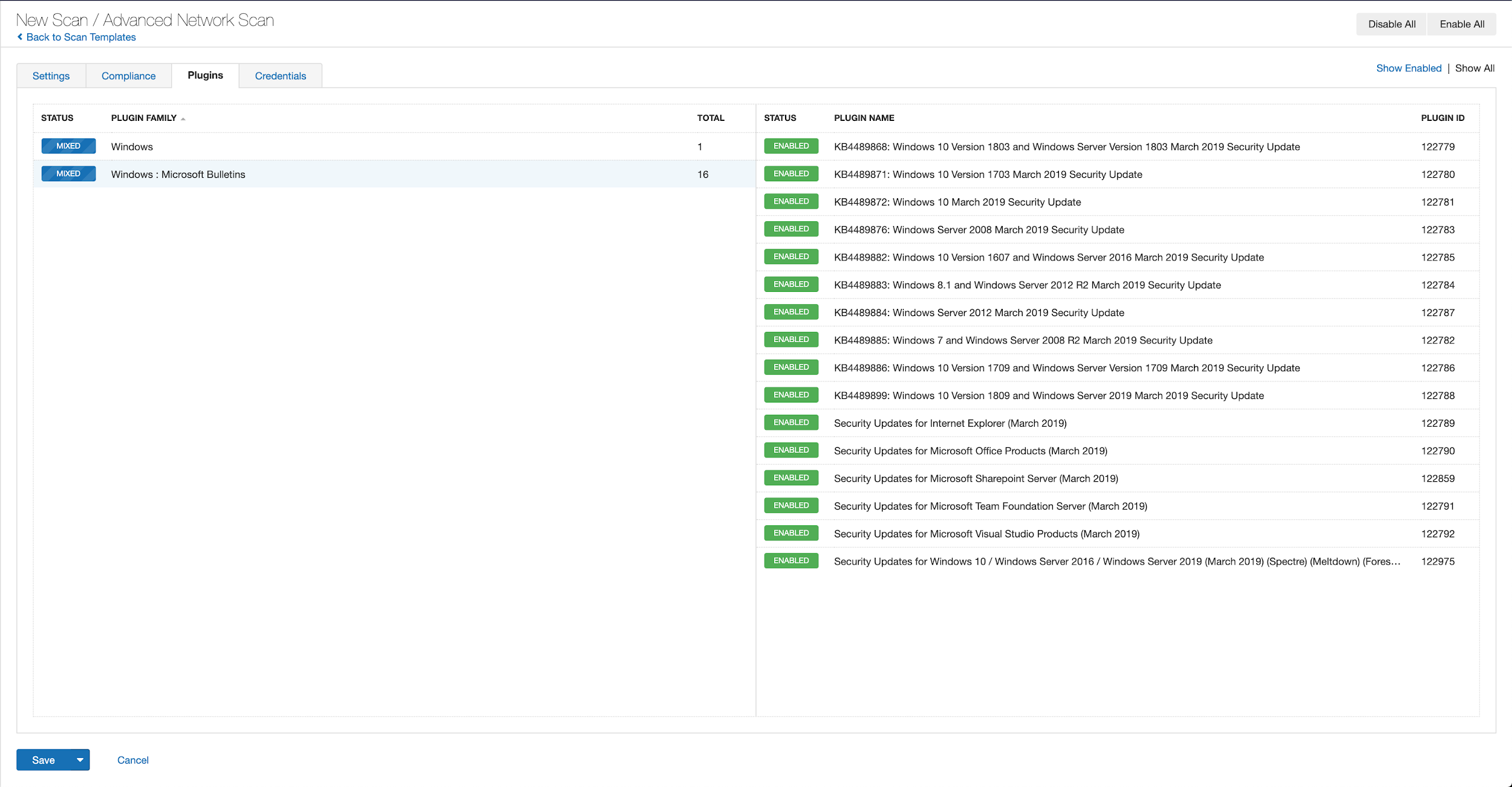
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
A list of all the plugins released for Tenable’s December 2021 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's December 2021 Security Updates
- Tenable plugins for Microsoft December 2021 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.