Oracle addresses 266 CVEs in its first quarterly update of 2022 with 497 patches, including 25 critical updates.
Background
On January 18, Oracle released its Critical Patch Update (CPU) for January 2022, the first quarterly update of the year. This CPU contains fixes for 266 CVEs in 497 security updates across 39 Oracle product families. Out of the 497 security updates published this quarter, 6.6% of patches were assigned a critical severity. Medium severity patches accounted for the bulk of security patches at 46.5%, followed by high severity patches at 41.9%.
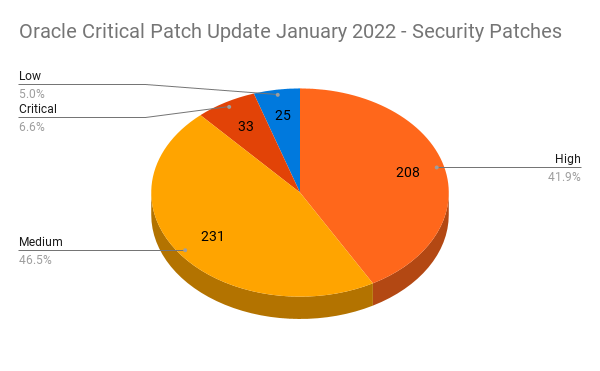
This quarter’s update includes 33 critical patches across 25 CVEs.
| Severity | Issues Patched | CVEs |
|---|---|---|
| Critical | 33 | 25 |
| High | 208 | 63 |
| Medium | 231 | 154 |
| Low | 25 | 24 |
| Total | 497 | 266 |
Analysis
This quarter, the Oracle Communications product family contained the highest number of patches at 84, accounting for 16.9% of the total patches, followed by Oracle MySQL at 78 patches, which accounted for 15.7% of the total patches.
Oracle fixes Log4Shell and associated vulnerabilities across some of its product suites
As part of the January 2022 CPU, Oracle addressed CVE-2021-44228, the Apache Log4Shell vulnerability disclosed in December 2021 as well as associated Log4j vulnerabilities that have been disclosed in the weeks since.
Oracle did not explicitly provide details within this release regarding CVE-2021-44228 and which components were affected. Instead, they broadly highlighted that applying the January 2022 CPU would address CVE-2021-44228 and CVE-2021-45046 across the following products:
- Oracle Communications
- Oracle Construction and Engineering
- Oracle Financial Services Applications
- Oracle Fusion Middleware
- Oracle Retail Applications
- Oracle Siebel CRM
While it’s not clear if Oracle has completed an assessment of all product families to address all occurrences of the recently disclosed Log4j vulnerabilities, we will continue to monitor for further updates. In addition to the broader message, Oracle provided some details around affected products for the other associated Log4j vulnerabilities:
| CVE | Product | Component | Remote Exploit without Auth |
|---|---|---|---|
| CVE-2021-45105 | Oracle Communications WebRTC Session Controller | Signaling Engine, Media Engine (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Communications Services Gatekeeper | API Portal (Apache Log4j) | Yes |
| CVE-2021-45105 | Instantis EnterpriseTrack | Logging (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail Integration Bus | RIB Kernel (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Financial Services Analytical Applications Infrastructure | Others (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail Invoice Matching | Security (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail Service Backbone | RSB Installation (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail Order Broker | System Administration (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle WebCenter Portal | Security Framework (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Managed File Transfer | MFT Runtime Server (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Business Intelligence Enterprise Edition | Analytics Server (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail Order Management System | Upgrade Install (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail Point-of-Service | Administration (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail Predictive Application Server | RPAS Server (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail Price Management | Security (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Communications Service Broker | Integration (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail Returns Management | Security (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Financial Services Model Management and Governance | Installer & Configuration (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail EFTLink | Installation (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail Back Office | Security (Apache Log4j) | Yes |
| CVE-2021-45105 | Oracle Retail Central Office | Security (Apache Log4j) | Yes |
| CVE-2021-44832 | Oracle Communications Interactive Session Recorder | RSS (Apache Log4j) | No |
| CVE-2021-44832 | Primavera Unifier | Logging (Apache Log4j) | No |
| CVE-2021-44832 | Oracle WebLogic Server | Centralized Thirdparty Jars (Apache Log4j) | No |
| CVE-2021-44832 | Oracle Communications Diameter Signaling Router | Virtual Network Function Manager, API Gateway (Apache Log4j) | No |
| CVE-2021-44832 | Primavera Gateway | Admin (Apache Log4j) | No |
| CVE-2021-44832 | Primavera P6 Enterprise Project Portfolio Management | Web Access (Apache Log4j) | No |
| CVE-2021-44832 | Siebel UI Framework | Enterprise Cache (Apache Log4j) | No |
| CVE-2021-44832 | Oracle Retail Fiscal Management | NF Issuing (Apache Log4j) | No |
| CVE-2021-44832 | Oracle Retail Assortment Planning | Application Core (Apache Log4j) | No |
| CVE-2021-4104 | Oracle Retail Allocation | General (Apache Log4j) | No |
| CVE-2021-4104 | Oracle Utilities Testing Accelerator | Tools (Apache Log4j) | No |
| CVE-2021-4104 | Oracle WebLogic Server | Centralized Thirdparty Jars (Apache Log4j) | No |
Oracle CPU Patch Breakdown
A full breakdown of the patches for this quarter can be seen in the following table, which also includes a count of vulnerabilities that can be exploited over a network without authentication.
| Oracle Product Family | Number of Patches | Remote Exploit without Auth |
|---|---|---|
| Oracle Communications | 84 | 50 |
| Oracle MySQL | 78 | 3 |
| Oracle Financial Services Applications | 48 | 37 |
| Oracle Retail Applications | 43 | 34 |
| Oracle Fusion Middleware | 39 | 35 |
| Oracle Communications Applications | 33 | 22 |
| Oracle Construction and Engineering | 22 | 15 |
| Oracle Java SE | 18 | 18 |
| Oracle PeopleSoft | 13 | 10 |
| Oracle Utilities Applications | 13 | 7 |
| Oracle Systems | 11 | 7 |
| Oracle Supply Chain | 10 | 8 |
| Oracle E-Business Suite | 9 | 5 |
| Oracle Health Sciences Applications | 8 | 8 |
| Oracle Enterprise Manager | 7 | 6 |
| Oracle Insurance Applications | 7 | 6 |
| Oracle Commerce | 6 | 6 |
| Oracle TimesTen In-Memory Database | 5 | 3 |
| Oracle Database Server | 4 | 0 |
| Oracle Essbase | 4 | 3 |
| Oracle HealthCare Applications | 4 | 4 |
| Oracle Support Tools | 4 | 4 |
| Oracle GoldenGate | 3 | 3 |
| Oracle Hospitality Applications | 3 | 3 |
| Oracle Big Data Graph | 2 | 2 |
| Oracle Graph Server and Client | 2 | 2 |
| Oracle REST Data Services | 2 | 1 |
| Oracle Secure Backup | 2 | 2 |
| Oracle Siebel CRM | 2 | 1 |
| Oracle Virtualization | 2 | 0 |
| Oracle Airlines Data Model | 1 | 1 |
| Oracle Communications Data Model | 1 | 1 |
| Oracle NoSQL Database | 1 | 0 |
| Oracle Spatial Studio | 1 | 1 |
| Oracle Food and Beverage Applications | 1 | 1 |
| Oracle Hyperion | 1 | 1 |
| Oracle iLearning | 1 | 1 |
| Oracle JD Edwards | 1 | 0 |
| Oracle Policy Automation | 1 | 1 |
Solution
Customers are advised to apply all relevant patches in this quarter’s CPU. Please refer to the January 2022 advisory for full details.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released.
Get more information
- Oracle Critical Patch Update Advisory - January 2022
- Oracle October 2021 Critical Patch Update Risk Matrices
- Oracle Advisory to CVE Map
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.