Tenable’s latest cloud security enhancements unify cloud security posture and vulnerability management with new, 100% API-driven scanning and zero-day detection capabilities.
Tenable has helped thousands of our customers scan and manage vulnerabilities in their cloud infrastructure for years. We accelerated our cloud native application protection (CNAPP) capabilities in 2021 and 2022 with our purchase of Accurics, the launch of Tenable.cs and integration with Tenable.io. We offer a unique approach to cloud security, unifying cloud security posture and vulnerability management into a single solution.
Today, Tenable announced new cloud security features that not only reflect significant technological advances but also offer clients a unified approach to cloud security posture and vulnerability management across cloud and non-cloud assets. With the latest release of Tenable.cs, users can extend to the cloud the same level of visibility and vulnerability management they’re accustomed to from our suite of market-leading solutions. The new features include:
- Tenable.cs Agentless Assessment and Tenable.cs Live Results
- Enhanced policy management and reporting
- Expanded DevOps / GitOps coverage
Tenable.cs Agentless Assessment and Tenable.cs Live Results
Empowering security teams to monitor the sprawling attack surface with continuous, complete cloud visibility is critical for any organization looking to build a unified cloud security program.
Tenable.cs Agentless Assessment and Tenable.cs Live Results enable security teams to quickly and easily discover and assess all their cloud assets. Data is continuously updated via live scans that are automatically triggered by any logged change event. When a new vulnerability is added to the database by our industry-leading Tenable Research team, Tenable.cs Live Results allow security teams to see if a vulnerability exists in their current asset inventory, without needing to execute a new scan.

Source: Tenable, August 2022
This will help organizations assess vulnerabilities on a continuous basis, discover zero-day threats as soon as they are published — without having to re-scan their entire environment — and reduce the potential for exploits to be executed. With coverage for more than 70,000 vulnerabilities, Tenable has the industry’s most extensive database of Common Vulnerabilities and Exposures (CVE). In addition, Tenable’s security configuration data helps customers understand all of their exposures across all of their assets.
Existing Tenable customers can now get early access to Tenable.cs Agentless Assessment for Amazon Web Services (AWS). For more on Agentless Assessment read the blog: Accelerate Vulnerability Detection and Response for AWS with Tenable Cloud Security Agentless Assessment.
In Q4, Tenable expects to release Tenable.cs Agentless Assessment for Microsoft Azure and Google Cloud Platform, along with additional enhancements around container security.
Enhanced policy management and reporting
For years we’ve been hearing about the importance of certain cybersecurity practices in cloud environments, particularly:
- Cloud security to properly protect those environments
- DevSecOps to embed security into software delivery pipelines
- “Shift left” to start security checks as part of local development cycles where they can be immediately fixed
Curious about the challenges involved in adopting these practices in the real world, we polled 388 Tenable webinar attendees in June about their concerns with regard to security in the public cloud. The responses offer us a glimpse into key areas of concern. When asked “What’s your main challenge with regards to the security of your assets in public cloud platforms?” more than 60% of respondents cited poor visibility into their assets and their security posture or concerns about cloud providers’ infrastructure security.
At Tenable, we believe organizations that have made significant investments in putting security and compliance gates into their application and infrastructure deployment lifecycles are now at a loss for the same in their journey to the public cloud.
With enriched policy workflows, new compliance reporting and failing policy groupings, Tenable.cs offers valuable insights to help users improve their cloud governance and cloud security posture management.
Tenable.cs Compliance Reporting: The image below shows how we dynamically update compliance reports and provide groupings for pre-defined benchmarks. Tenable.cs supports over 20 benchmarks, including Service Organization Control 2 (SOC2), Health Insurance Portability and Accountability Act (HIPAA) and General Data Protection Regulation (GDPR).
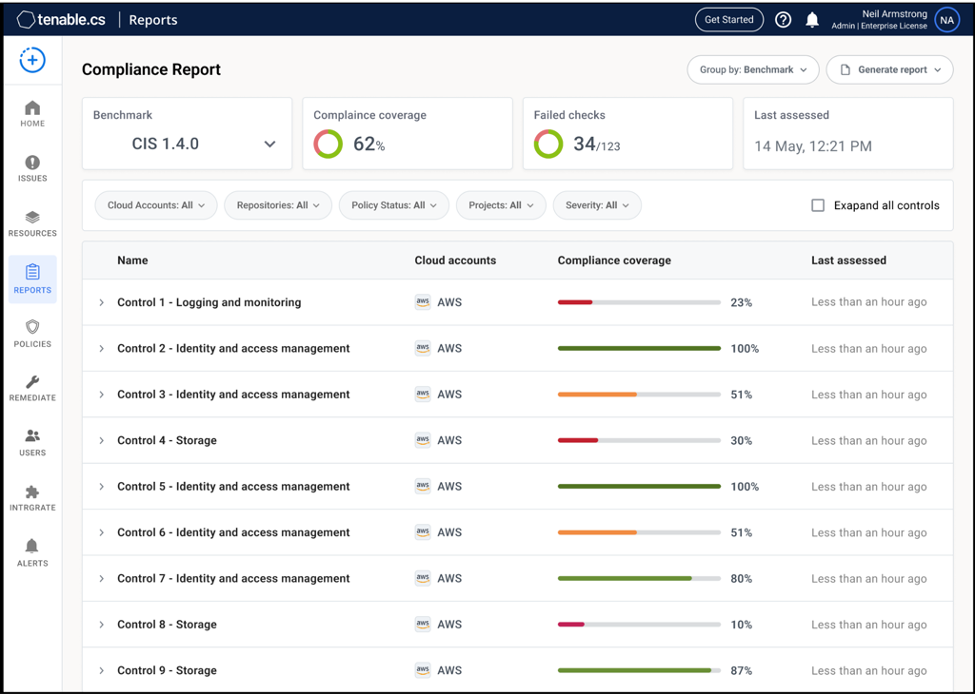
Source: Tenable, August 2022
Tenable.cs Automated Workflows: The image below shows an example of how users can easily create integrated workflows based on a specific policy so they can quickly re-assess any out-of-the-box policy or use it as a template to build a new customized policy specific to their environment.
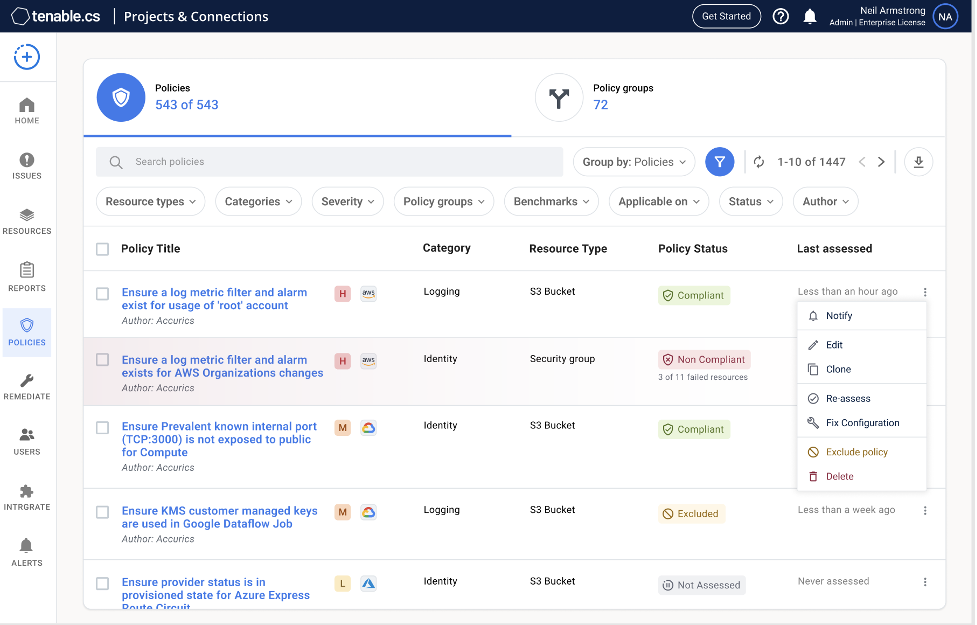
Source: Tenable, August 2022
Expanded Remediation, DevOps and GitOps coverage
In the webinar poll referenced above, we asked clients, “What’s the level of integration and automation of your security checks with your software development and delivery process (aka DevSecOps)?” The response was overwhelmingly one-sided. Nearly 70% of respondents indicated minimal or no automation. This can lead to a high level of exposure and long remediation times
Tenable.cs helps DevSecOps teams reduce the number of security weaknesses found in production by integrating into existing DevOps workflows. Along these lines, we have made several key enhancements to aid DevSecOps teams.
- Automated remediation workflow improvements
- HashiCorp Terraform cloud run task support
- Improved source code management
Automated Remediation Workflows: Out of the box, Tenable.cs provides an integrated view of all the resources failing a security policy that includes individual details along with the remediation recommendations that can be quickly passed to development teams using quick links that start automated workflows. As part of this release, we’ve made a number of improvements to enhance Jira-specific workflows and alert management. See example below.

Source: Tenable, August 2022
HashiCorp Terraform cloud run task integration: This new integration enables Tenable.cs to scan Terraform templates during the Terraform cloud deploy step. This allows Terraform cloud customers to detect any security issues within their Infrastructure as Code (IaC) using Tenable.cs as part of the planning phase of the Terraform execution. By adding this support for Terraform cloud run tasks in Tenable.cs, we’re helping developers detect and fix compliance and security risks in their IaC so they can mitigate issues before cloud infrastructure is provisioned. See example below.
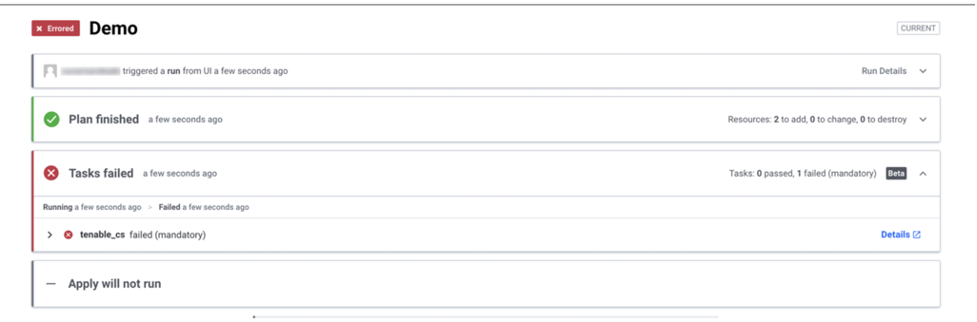
Source: Tenable, August 2022
Users interested in viewing the setup guide on how to connect Tenable.cs with Terraform cloud workspace can find detailed documentation here.
Improved source code management integration and scanning: Tenable.cs provides a “no experience necessary” mechanism of discovering all your repositories and can pull multiple repositories into an integrated view of all the resources failing security policies or compliance benchmarks. Any policy violations can quickly be resolved via auto-generated pull requests that can be submitted and tracked all within the same console. See example below.
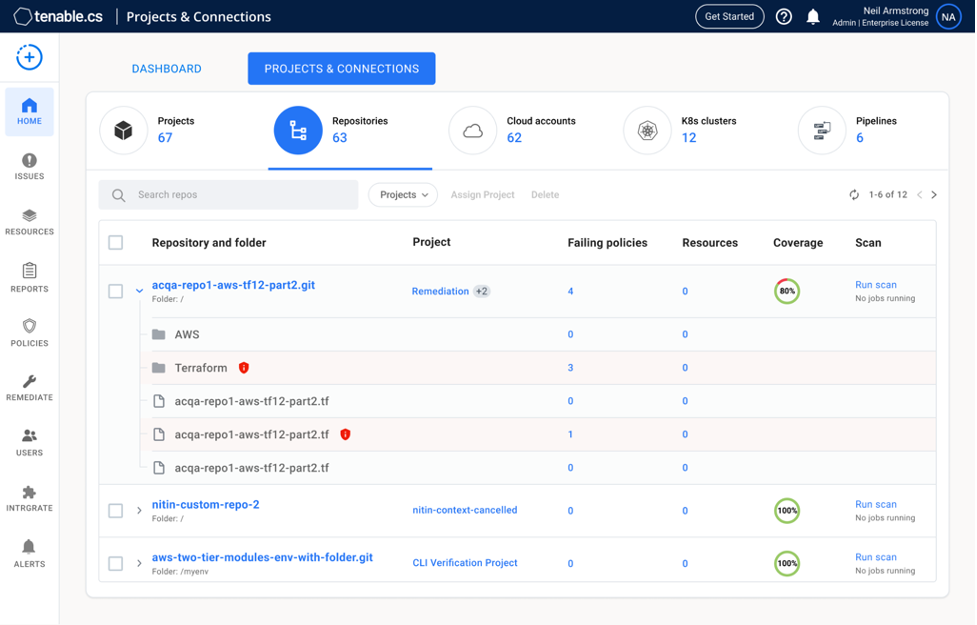
Source: Tenable, August 2022
Learn more
- Attend the webinar: What’s New with Tenable Cloud Security?
- Read the blog: Accelerate Vulnerability Detection and Response for AWS with Tenable Cloud Security Agentless Assessment
- Visit our Tenable.cs product page: https://www.tenable.com/products/tenable-cs