Microsoft addresses 62 CVEs including four zero-day vulnerabilities that were exploited in the wild.
- 9Critical
- 53Important
- 0Moderate
- 0Low
Microsoft patched 62 CVEs in its November 2022 Patch Tuesday release, with nine rated as critical, and 53 rated as important. As part of its Patch Tuesday release, Microsoft also released a Defense in Depth Update (ADV220003) for Microsoft Office and advisories attributed to AMD [1] and GitHub [1, 2]. We did not include these advisories in our overall Patch Tuesday counts.

This month’s update includes patches for:
- .NET Framework
- AMD CPU Branch
- Azure
- Azure Real Time Operating System
- Linux Kernel
- Microsoft Dynamics
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft Office Word
- Network Policy Server (NPS)
- Open Source Software
- Role: Windows Hyper-V
- SysInternals
- Visual Studio
- Windows Advanced Local Procedure Call
- Windows ALPC
- Windows Bind Filter Driver
- Windows BitLocker
- Windows CNG Key Isolation Service
- Windows Devices Human Interface
- Windows Digital Media
- Windows DWM Core Library
- Windows Extensible File Allocation
- Windows Group Policy Preference Client
- Windows HTTP.sys
- Windows Kerberos
- Windows Mark of the Web (MOTW)
- Windows Netlogon
- Windows Network Address Translation (NAT)
- Windows ODBC Driver
- Windows Overlay Filter
- Windows Point-to-Point Tunneling Protocol
- Windows Print Spooler Components
- Windows Resilient File System (ReFS)
- Windows Scripting
- Windows Win32K
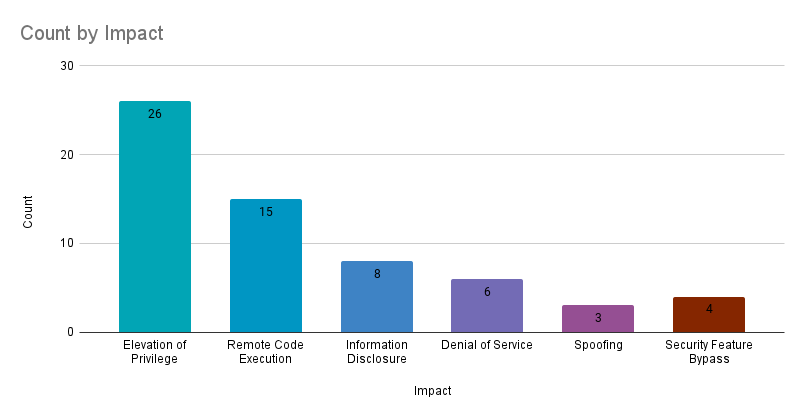
Elevation of privilege (EoP) vulnerabilities accounted for 41.9% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 24.2%.
While they are not considered new advisories as part of the November Patch Tuesday release, Microsoft updated the advisory pages for CVE-2022-41040 and CVE-2022-41082 (ProxyNotShell) indicating that patches are now available along with this month’s Security Updates.
CVE-2022-41049 and CVE-2022-41091 | Windows Mark of the Web Security Feature Bypass Vulnerability
CVE-2022-41049 and CVE-2022-41091 are security feature bypass vulnerabilities affecting Windows Mark of the Web (MoTW). MoTW is a security feature used to tag files downloaded from the internet and prevent them from performing certain actions. Files flagged with MoTW would be opened in Protected View in Microsoft Office — prompting users with a security warning banner asking them to confirm the document is trusted by selecting Enable content. A malicious actor could craft a file that could bypass MoTW “resulting in a limited loss of integrity and availability of security features such as Protected View.”
CVE-2022-41091 has been exploited in the wild and for which exploit code is publicly available. Though it was not credited to any researcher in particular, researchers at HP observed the Magniber ransomware group exploiting this vulnerability in the wild.
CVE-2022-41049 on the other hand has not been exploited in the wild, but is rated “Exploitation More Likely” according to Microsoft’s Exploitability Index. Both CVEs were given CVSSv3 scores of 5.4 and require user interaction — an attacker would need to entice a victim into opening the crafted file.
CVE-2022-41073 | Windows Print Spooler Elevation of Privilege Vulnerability
CVE-2022-41073 is an EoP vulnerability affecting the Windows Print Spooler service. The vulnerability carries a CVSSv3 score of 7.8 and discovery was credited to Microsoft Threat Intelligence Center. This flaw has been exploited in the wild, according to Microsoft, and could allow a low privileged user to gain SYSTEM level privileges.
The Windows Print Spooler service continues to gain interest from researchers and attackers alike since PrintNightmare (CVE-2021-34527) was disclosed in July of 2021. Since then a slew of vulnerabilities have been reported including another EoP (CVE-2022-38028) credited to the National Security Agency in last month's Patch Tuesday release.
CVE-2022-41125 | Windows CNG Key Isolation Service Elevation of Privilege Vulnerability
CVE-2022-41125 is an EoP vulnerability in the Windows Cryptography Next Generation (CNG) Key Isolation Service used for Windows cryptographic support and operations. With a CVSSv3 score of 7.8, successful exploitation would allow an attacker to gain SYSTEM privileges. While no additional details were provided in the advisory, this vulnerability has reportedly been exploited in the wild and is one of four CVEs in this month's Patch Tuesday release to have been flagged as “exploitation detected” according to Microsoft.
CVE-2022-41118 and CVE-2022-41128 | Windows Scripting Languages Remote Code Execution Vulnerability
CVE-2022-41118 and CVE-2022-41128 are RCE vulnerabilities affecting the JScript9 and Chakra scripting languages. CVE-2022-41128 has a CVSSv3 score of 8.8 and only impacts the JScript9 scripting language. It has been exploited in the wild and successful exploitation requires a user with an affected version of Windows to visit a malicious, attacker controlled server. CVE-2022-41118 on the other hand, has a CVSSv3 score of 7.5 and has not been observed to be exploited. In the case of CVE-2022-41118, an attacker would need to convince a user to connect to a malicious server hosting a specially crafted website as well as win a race condition. Despite these barriers for exploitation, Microsoft still rated CVE-2022-41118 as “Exploitation More Likely.”
CVE-2022-3602 and CVE-2022-3786 | X.509 certificate verification buffer overrun
This month Microsoft also released patches for a pair of recently disclosed vulnerabilities impacting OpenSSL, a widely used open source library for cryptographic implementation of secure socket layer and transport layer security protocols. These updates are available for the following products:
More information on these two vulnerabilities including Tenable product coverage can be found in our blog post.
Tenable Solutions
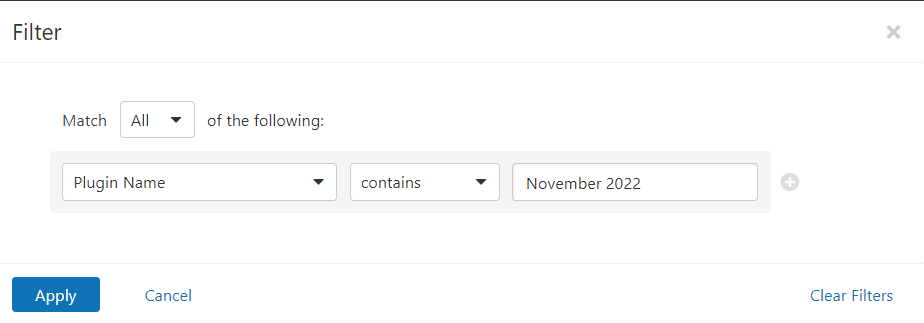
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains November 2022.
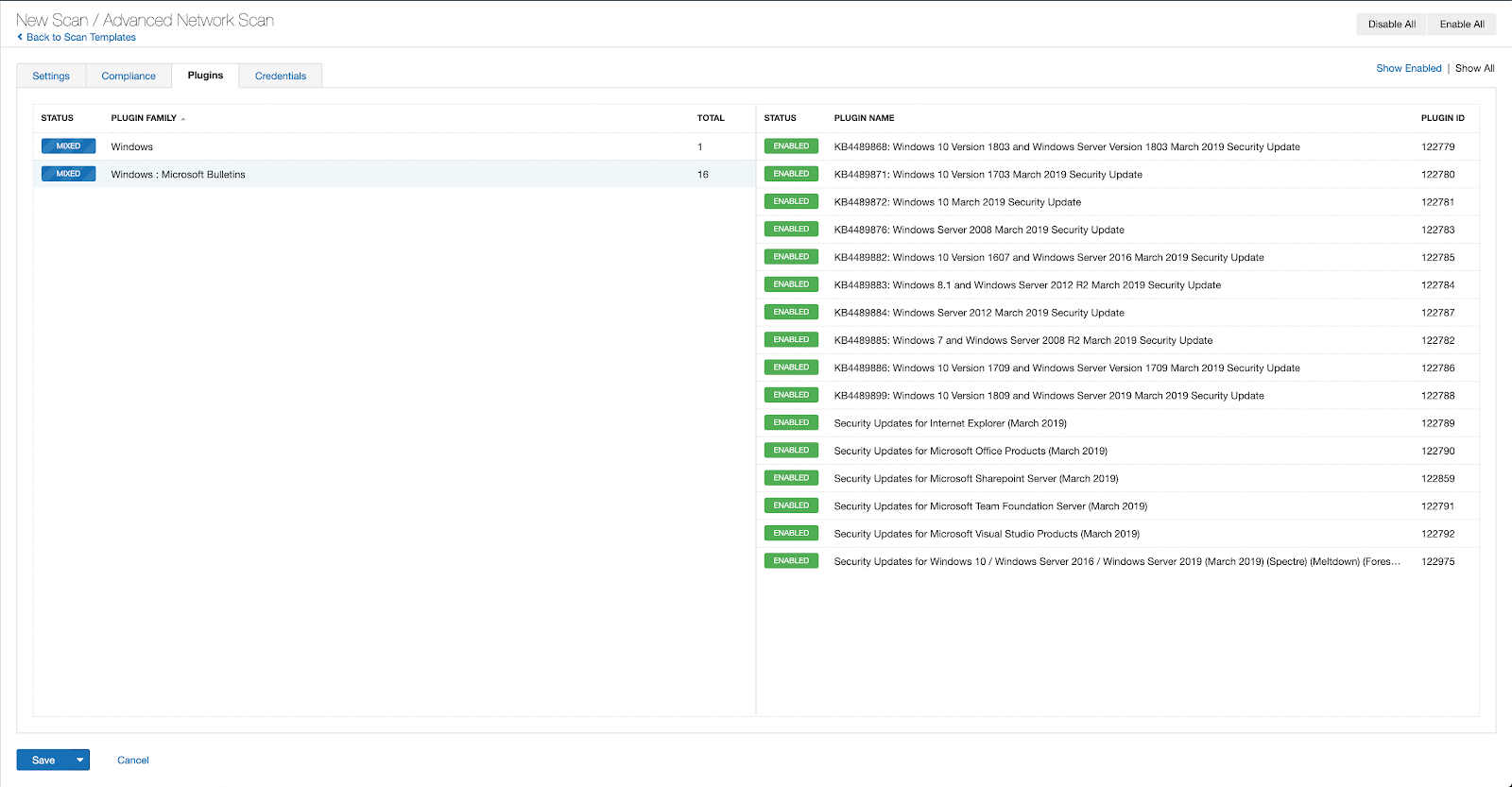
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
A list of all the plugins released for Tenable’s November 2022 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's November 2022 Security Updates
- Tenable plugins for Microsoft November 2022 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.