Microsoft addresses 48 CVEs including two zero-day vulnerabilities, one that has been exploited in the wild (CVE-2022-44698) and one that was publicly disclosed prior to a patch being available (CVE-2022-44710).
- 7Critical
- 40Important
- 1Moderate
- 0Low
Microsoft patched 48 CVE in its December 2022 Patch Tuesday release, with seven rated as critical and 40 rated as important and 1 rated as moderate. Microsoft also released a Defense in Depth update (ADV220005) for Driver Certificate Deprecation.

This month’s update includes patches for:
- .NET Framework
- Azure
- Client Server Run-time Subsystem (CSRSS)
- Microsoft Bluetooth Driver
- Microsoft Dynamics
- Microsoft Edge (Chromium-based)
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office OneNote
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Windows Codecs Library
- Role: Windows Hyper-V
- SysInternals
- Windows Certificates
- Windows Contacts
- Windows DirectX
- Windows Error Reporting
- Windows Fax Compose Form
- Windows HTTP Print Provider
- Windows Kernel
- Windows PowerShell
- Windows Print Spooler Components
- Windows Projected File System
- Windows Secure Socket Tunneling Protocol (SSTP)
- Windows SmartScreen
- Windows Subsystem for Linux
- Windows Terminal
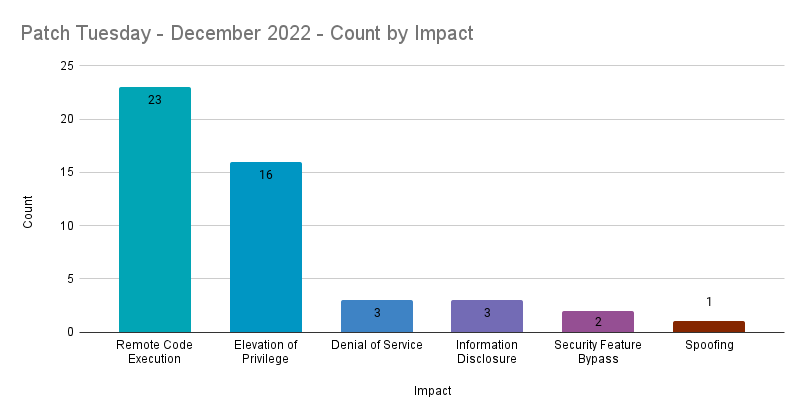
Remote code execution (RCE) vulnerabilities accounted for 47.9% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 33.3%.
CVE-2022-44698 | Windows SmartScreen security feature bypass vulnerability
CVE-2022-44698 is a security feature bypass vulnerability in the Windows operating system. This is a mark of the web (MoTW) vulnerability similar to those patched in the November 2022 Patch Tuesday release. All of these MoTW vulnerabilities prevent specially crafted downloads from being marked as being from the web, which affects the integrity and availability of security features that utilize MoTW tagging. This vulnerability was disclosed by Will Dormann.
Where this vulnerability differs, is that it affects the SmartScreen feature of Windows operating systems, rather than the Protected View feature in Office. Successful exploitation prevents SmartScreen from performing a reputation check on the downloaded file. This could lead to a known malicious executable not alerting users that the file may be malicious. According to Microsoft's Exploitability Index, exploitation of this vulnerability has been detected in the wild.
CVE-2022-44690 and CVE-2022-44693 | Microsoft SharePoint Server remote code execution vulnerabilities
CVE-2022-44690 and CVE-2022-44693 are RCE vulnerabilities in Microsoft SharePoint Server that both received a CVSSv3 score of 8.8. An authenticated attacker with permission to use Manage Lists in SharePoint could exploit these vulnerabilities to execute code remotely. Both vulnerabilities are rated as “Exploitation Less Likely.”
CVE-2022-41089 |.NET Framework remote code execution vulnerability
CVE-2022-41089 is an unauthenticated RCE vulnerability in Microsoft.NET framework with a CVSSv3 score of 8.8 and low attack complexity. However, successful exploitation requires user interaction, making exploitation less likely. Discovery is credited to Nick Landers with NetSPI and Eleftherios Panos with Nettitude.
CVE-2022-41076 | PowerShell remote code execution vulnerability
CVE-2022-41076 is a RCE vulnerability in Windows Powershell that received a CVSSv3 score of 8.5 and was rated as "Exploitation more likely" according to Microsoft's Exploitability Index. Exploitation of this flaw requires that an authenticated attacker first prepare the target. While the advisory does not detail what actions must be taken, it does note that any authenticated attacker can exploit this vulnerability and no elevated privileges are required. Successful exploitation would allow an attacker to run arbitrary commands on an affected system.
CVE-2022-44678 and CVE-2022-44681 | Windows Print Spooler components elevation of privilege vulnerability
CVE-2022-44678 and CVE-2022-44681 are EoP vulnerabilities in Windows Print Spooler components. As with their many predecessors, these vulnerabilities received a CVSSv3 score of 7.8. However, despite the similarities, Microsoft rated these as “Exploitation Less Likely” and “Exploitation Unlikely” respectively. Discovery is credited to researchers at the Qi'anxin Group.
Tenable Solutions
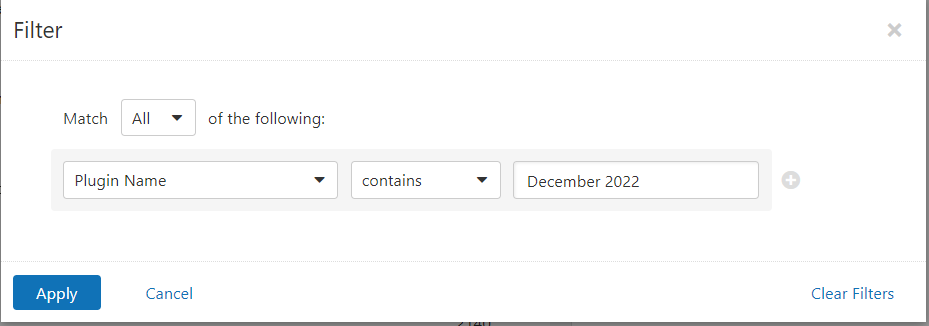
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains December 2022.
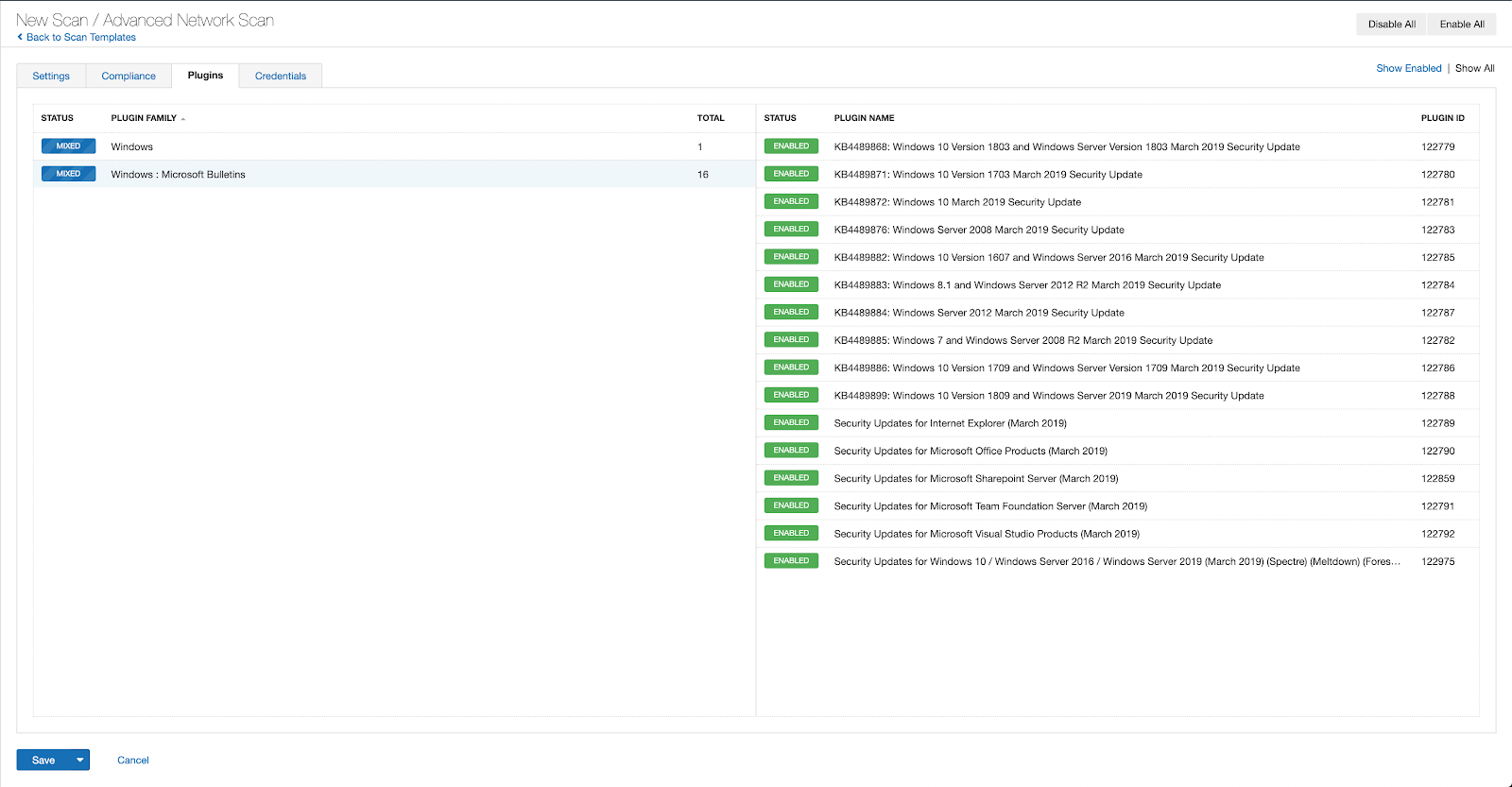
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
A list of all the plugins released for Tenable’s December 2022 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's December 2022 Security Updates
- Tenable plugins for Microsoft December 2022 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
