Dive into the history of Patch Tuesday and learn how it continues to influence the ways security teams manage patches.
Background on MS Patch Tuesday
In 2022, rumors of Patch Tuesday’s death circulated widely, but ultimately such talk was greatly exaggerated. Yet, these rumors led to soul searching among many IT, security and DevOps teams. Patch Tuesday (PT) has long been a staple, for better or worse, of the monthly cybersecurity and IT administrator lifecycle of vulnerability management. While there’s no indication that PT is going away anytime soon, the end of the year offers an opportunity to examine how PT has evolved and what it’s accomplished during its two-decade history.
Let’s start with a quick look at what Patch Tuesday had in store for teams throughout 2022.
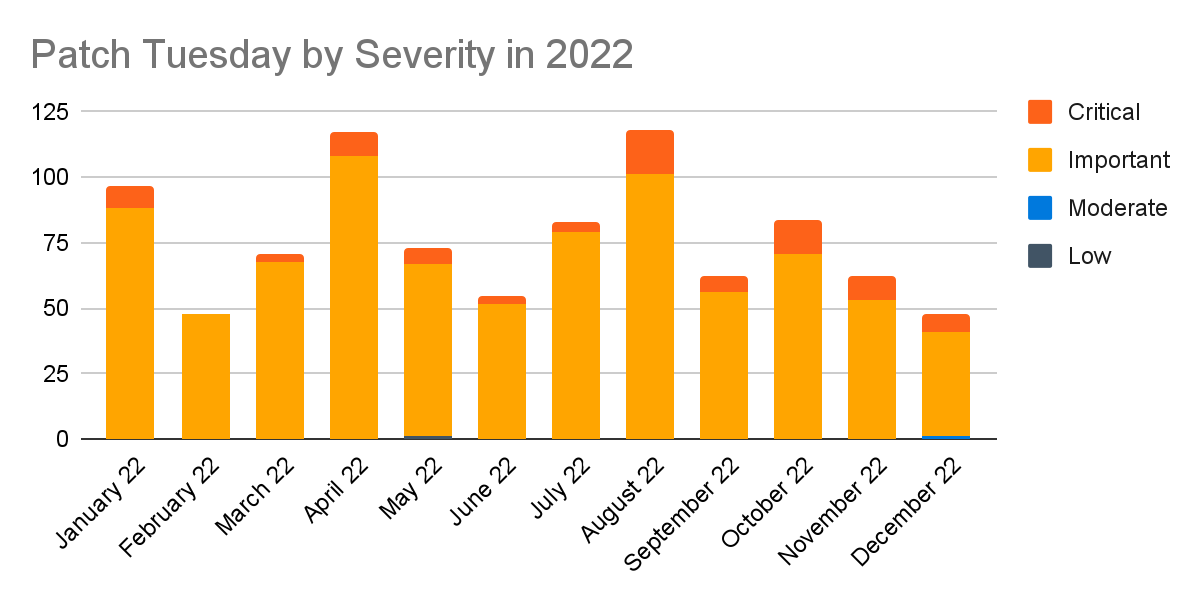
Source: Tenable Research, December 2022
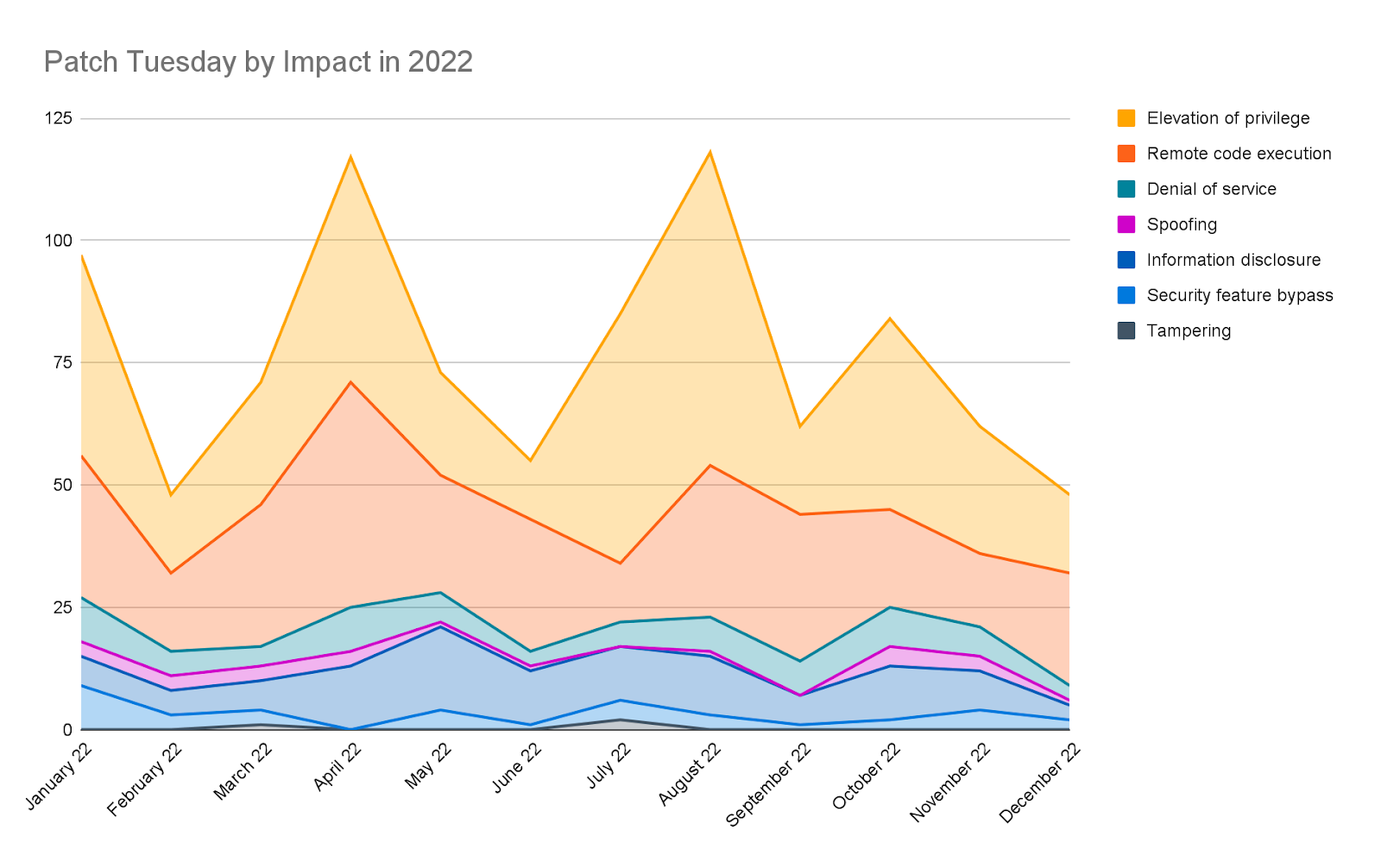
Source: Tenable Research, December 2022
A brief history of Patch Tuesday
In the early 2000s, patching was a haphazard, improvised process that was handled differently by each organization. That changed in late 2003 when Microsoft introduced a standard patch release schedule turning the second Tuesday of the month into Patch Tuesday. Given the footprint Microsoft had and continues to have in enterprises, this approach revolutionized how companies handled patching and made it possible to plan for updates ahead of time. In the years since, other vendors have adopted the Patch Tuesday approach.
Over the last two decades, PT has experienced multiple watershed moments. In 2017, Microsoft modified how it disclosed flaws and released patches. Specifically, Microsoft eliminated security bulletins and replaced them with the Security Update Guide, changing how analysts and researchers received content. With this move, the data Microsoft provided about releases became less intuitive to read and required more time to comb through and process. Rather than grouping sets of vulnerabilities according to affected products, the Update Guides are provided for each vulnerability individually.
Next, in September 2020, Microsoft announced a “new and improved Security Updated Guide.” What the company failed to mention in that announcement was that one “improvement” was the removal of executive summaries — detailed, more narrative explanations of the vulnerabilities beyond just CVSS metrics — from the Security Update guide.
Particularly given the lack of advanced notice, this change rankled the security community. Tenable CSO Bob Huber in November 2020 commented, “Microsoft’s decision to remove CVE description information from its Patch Tuesday release is a bad move, plain and simple. By relying on CVSSv3 ratings alone, Microsoft is eliminating a ton of valuable vulnerability data that can help inform organizations of the business risk a particular flaw poses to them.” He argued that the decision not only made it nearly impossible for security professionals to understand how urgent a patch may be, it effectively favored threat actors.
The changes to PT over the years have taught us that even minimal disruptions to the process impact the speed at which updates can be applied and should prepare us for the next big change.
The current state of Patch Tuesday
PT has become a constant in a sea of uncertainty. When day-to-day cybersecurity and vulnerability management are so turbulent, the ability to plan at all is a boon. Technology and security decision-makers rely on PT in their overarching strategy. Any potential changes to PT require reevaluation of those strategies and metrics. Miscommunication from Microsoft regarding PT is always disruptive.
In 2022, Microsoft has included 663 vulnerabilities in PT releases, not counting out-of-band patches, which puts it on track to match 2021 and 2019. 2020 was an aggressive year for PT, with over 1,200 vulnerabilities addressed in monthly releases and eight months in which we saw triple-digit bundles. This may be due to altered work patterns and environments in response to the global pandemic.
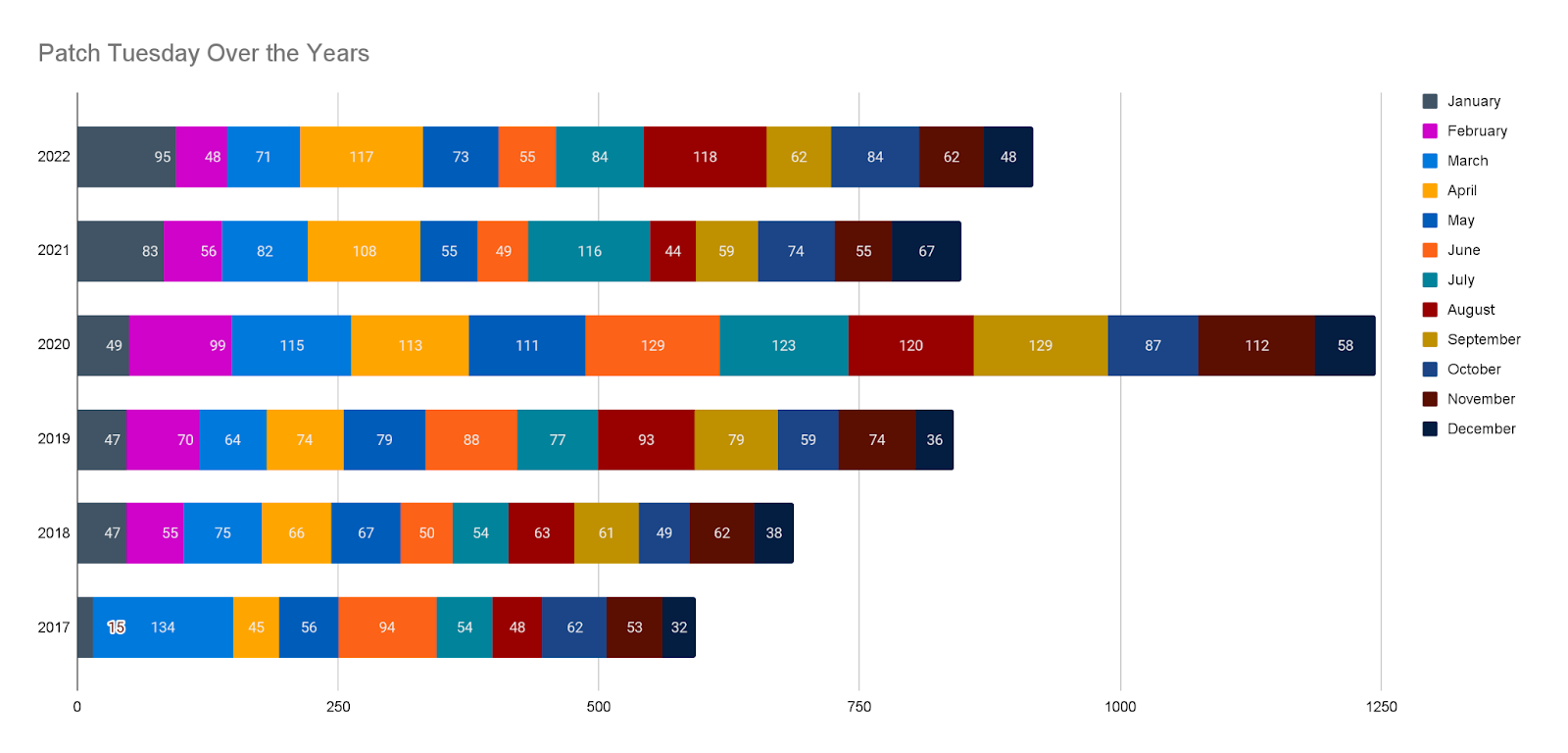
Source: Tenable Research, December 2022
With so many factors at play – varying disclosure timelines from reporting entities; conference seasons clustering disclosures together; and likely myriad internal factors at Microsoft into which we’d have no visibility – it’s hard to draw conclusions from these releases. Organizations must operate primarily off the knowledge that PT will happen and wait until the second Tuesday of the month to figure out what has happened.
July 1, 2022, began the rollout of Autopatch, announced in early April 2022. This announcement was the source of the rumored end of PT, specifically this statement: “For organizations who select this option, the second Tuesday of every month will be 'just another Tuesday'.” By the end of April, Microsoft released an update to this announcement to clarify the continuation of PT. But, as they say, “A lie will go round the world while the truth is pulling its boots on.”
Several articles were published from vendors and news organizations proclaiming the potential end of PT and, while that end isn’t here yet, auditing how your organization might handle disruptive changes to any recurring software updates is always prudent.
Another change, announced in January 2022 and moved to its final phase in August, affected the notification system for Patch Tuesday releases and updates. Compared to other announced changes, this was fairly minor. Microsoft retired the Security Notification Service, through which it usually sent email notifications, in favor of its Security Update Guide (SUG) service. In October, the vendor also announced the launch of a RSS feed for these updates.
In the turbulent landscape of vulnerability management, it is a relief to have routine security releases such as Patch Tuesday from several vendors like Microsoft, and quarterly updates from Oracle, F5 and others.
Not only do they give teams a hub around which to plan patching and remediation operations, but these security releases act as a focal point for program metrics and key performance indicators defining standards for “normal” behavior. When Microsoft releases an out-of-band patch, it immediately indicates a level of urgency.
Organizations should examine how those metrics and updates affect their operations. Here are a few questions your organization needs to answer to make sure you’re prepared for any unexpected changes.
- If the bulk releases are replaced with ad hoc releases, how would your team adapt and balance the workload of a slow trickle that may amount to the same number of vulnerabilities patched?
- If the process moves to automated patching, how will your team maintain visibility on what has been patched on your systems?
- How will you report that information to other stakeholders?
Tenable’s Patch Tuesday workflow
Through the years and many iterations of PT, Tenable has learned and adapted to provide coverage for the diverse releases vendors put out. We focus on combining automation and manual efforts to ensure both speed and accuracy for the coverage we release.
Specifically, Tenable Research has utilized automation to streamline the process for our teammates who handle plugin development. We generate template plugins and work tickets for that team by leveraging the Microsoft Security Bulletins API and Tenable’s own vulnerability database. We have learned that PT can change drastically with little to no notice, so we developed processes that are resilient in the face of those changes, or can be quickly adapted when Microsoft, or any vendor, changes how it releases security updates.
Our goal is to make the process seamless and efficient for our teams. Thanks to recent efforts, less than 15 minutes after advisories are published, security engineers have started developing plugins for our products. As a result, plugins are published much quicker, customers can begin scanning sooner and the attackers’ advantage is significantly reduced.
What’s next for PT
Despite the ongoing uncertainty around Microsoft’s PT, organizations are likely better prepared than they might think for a world without PT. Organizations that adopt Microsoft’s Autopatch should continue to monitor Microsoft’s releases to understand what vulnerabilities have been patched by Microsoft, whether they are under active exploitation and what other mitigations might be available.
As 2023 kicks off, organizations should routinely evaluate their patching strategies, even for routine releases that feel reliable. The sheer volume of releases means organizations must make important decisions on prioritization and take into account factors such as vulnerability severity and exploitability and asset criticality. Just because the active patch deployment happens automatically does not mean that organizations won’t have important actions to take to ensure they are being protected.
Learn more
Stay up-to-date on the latest Tenable Research.
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
