As 2022 ends, we highlight important data points that shine a light on the trends, challenges and best practices that matter to cybersecurity leaders eager to boost their exposure management and reduce their organizations’ cyber risk.
Dive into six illuminating cybersecurity research findings of 2022.
1 – Log4J’s Log4Shell: Emblematic of VM complexities
Little over a year after the Log4j crisis, few data points illustrate the challenges of vulnerability management as well as Tenable’s finding that, as of October, 72% of global organizations remained exposed to Log4Shell, despite its unprecedented severity, pervasiveness and notoriety.
Another illuminating takeaway from Tenable’s telemetry study, which was based on data collected from over 500 million tests: 29% of vulnerable assets had recurrences of Log4Shell after full remediation was achieved.
In a nutshell, the difficulties stemming from the Log4 crisis serve as a reminder of the importance of approaching vulnerability management in the right way.
“Vulnerability management, and Log4j in particular, is not a one-and-done search and destroy mission for security teams. It has to be a hygiene process like brushing your teeth and repeated, day in and day out to be effective,” wrote Tenable CEO and Chairman Amit Yoran in his LinkedIn article titled “One Year Later, Log4Shell Game Drags On.”
For more thoughts, insights and recommendations about Log4j and vulnerability management in general:
- “Are You Ready for the Next Log4Shell? Tenable’s CSO and CIO Offer Their Advice” (Tenable)
- Tenable’s Log4j resource page
- U.S. government advisory on APT exploit of Log4Shell to breach agency (U.S. Cybersecurity and Infrastructure Security Agency - CISA)
- Log4j guidance from CISA
- CISA’s Cyber Safety Review Board Log4j event review
2 – Widespread identity-related attacks threaten most organizations
One stat left no doubt about the pandemic-level incidence of devastating identity breaches: 84% of U.S. organizations experienced an identity-related breach in the 12 months ending in mid-2022.
That finding came from the Identity Defined Security Alliance’s “2022 Trends in Securing Digital Identities” report, based on an online survey of 500-plus identity and security professionals. Among the organizations impacted, 78% said the breach had a direct impact on the business, including recovery costs and brand damage.
Other findings from the report, conducted by Dimensional Research, include:
- The number and types of identities are growing fast in most organizations (98%) due to factors like cloud adoption, trusted third parties like contractors and machine identities.
- Breaches of credentials are up and most respondents (96%) agree the attacks are preventable.
- Risky user behavior drops when executives in the organization stress the importance of identity security.
For more information, you can request a copy of the report and check out a summary, blog and infographic about it.
To dive deeper into this topic:
- “What is identity and access management? Guide to IAM” (TechTarget)
- “Identity and access management explained” (CSO Magazine)
- “8 best practices to harden identity and access management permissions” (Security Magazine)
- “Eliminating Attack Paths in Active Directory” (Tenable)
- “Identity and Access Management Report 2022” (Identity Management Institute)
3 – For better cloud security, up your CSPM dosage
Securing your cloud environments and assets can be a challenge due to the number and variety of risks and to the fast-changing, always-evolving cloud technologies. As a result, cybersecurity pros tasked with cloud security are always on the lookout for new skills, best practices and tools that can help them reduce the risk of cloud breaches.
One very specific insight stood out for us in the SANS Institute’s “SANS 2022 DevSecOps Survey,” based on a survey of 431 security leaders and practitioners worldwide and sponsored by Tenable: Cloud security posture management (CSPM) products are underutilized.
Specifically, the study found that although most respondents said they’re using a CSPM tool, only a small minority uses it for 75% or more of their Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP) accounts.
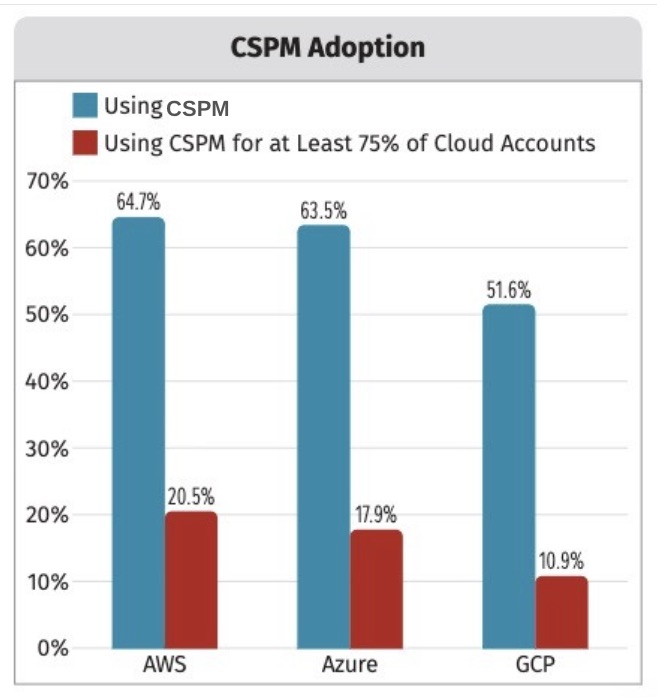
(Source: “SANS 2022 DevSecOps Survey,” SANS Institute, September 2022)
“CSPM software can help DevSecOps teams ensure that the cloud environments that host their applications are properly configured and secured using industry best practices, but only if this software is used consistently across all cloud accounts,” reads the report.
For more information about CSPM and about cloud security topics in general, check out the Tenable resources:
- “Cloud Security: 5 Key Takeaways from the SANS DevSecOps Survey” (blog)
- “Scaling Cloud Adoption without Sacrificing Security Standards” (on-demand webinar)
- “How to Choose a Modern CSPM Tool to Reduce Your Cloud Infrastructure Risk” (blog)
- “To Boost Software Supply Chain Security, Stop the Finger-Pointing” (blog)
- “How CISOs Can Stop Worrying About Cloud Security and Rest Easy” (infographic)
- “The Four Phases of Cloud Security Maturity” (on-demand webinar)
4 – Securing internet-exposed assets gets more challenging
Protecting an organization’s external attack surface is critical to maintain a solid security posture, and the task is getting more complicated, as internet-facing assets multiply and become more geographically dispersed. A Tenable study from October showed the real-world challenges involved in securing these publicly exposed assets.
After examining an inventory of the external attack surface of 22 of the U.K.’s 50 largest organizations, Tenable found that, on average, they had a whopping 76,600 internet-facing assets. One organization had more than half a million. On average, these organizations had assets hosted in or passing through 51 countries.
Illustrating how difficult it is for organizations with a vast array of internet-facing assets to stay current with security technology, the study found that all 22 organizations had web-based assets still supporting TLS 1.0 and half of them had instances of SSL 2.0 – two outdated and vulnerable protocols.
To properly secure these assets, cybersecurity teams need to master the practice of external attack surface management (EASM). For more information about EASM, check out these Tenable resources:
- “Bringing External Attack Surface Management to the Masses with Bit Discovery” (blog)
- “Introducing Nessus Expert, Now Built for the Modern Attack Surface” (blog)
- “Isn't It Time To Stop Guessing and Finally Know the Whole Truth About Your External Attack Surface Risk?” (on-demand webinar)
- “Finally Finding the 'Unknown Unknowns' Across Your Entire Attack Surface” (blog)
- “The Right Way to do Attack Surface Mapping” (blog)
5 – OT threats put critical infrastructure at heightened risk
In 2022, the cybersecurity world intensified its attention on the protection of operational technology (OT) and IT systems used in critical infrastructure facilities. A takeaway from a Microsoft study validates this concern.
In its third “Cyber Signals” report, published in December and based on 43 trillion security signals gathered by Microsoft, the company identified unpatched, high-severity vulnerabilities in 75% of the most common industrial controllers in customer OT networks.
“While the prevalence of IoT and OT vulnerabilities presents a challenge for all organizations, critical infrastructure is at increased risk,” reads the report, titled “The Convergence of IT and Operational Technology: Cyber Risks to Critical Infrastructure on the Rise.”
Further, in its “Digital Defense Report 2022,” published in November, Microsoft found that nation-state actors have significantly dialed up their cyber assaults against critical infrastructure targets, which now account for 40% of nation-state attacks, up from 20% last year. Microsoft highlighted threats from China, Iran, North Korea and Russia – in particular the latter’s use of cyberweapons in its war against Ukraine.
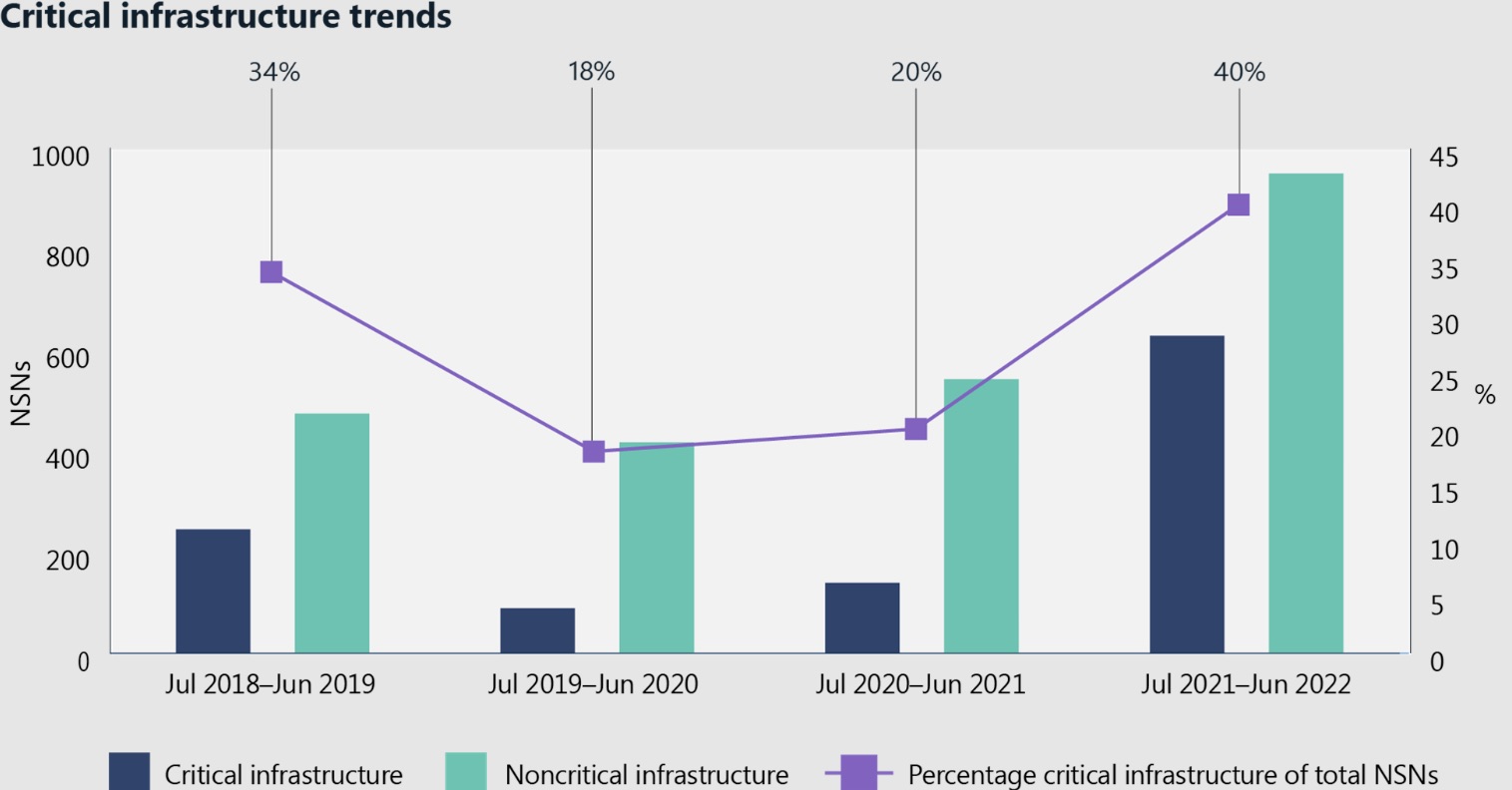
(Source: “Microsoft Digital Defense Report 2022,” Microsoft, November 2022)
For more information about OT security topics, check out these Tenable resources:
- “IT/OT Convergence: Now Is the Time to Act” (blog)
- “The State of OT Security, a Year Since Colonial Pipeline” (podcast)
- “Securing Critical Infrastructure: It's Complicated” (blog)
- “How Can We Strengthen the Cybersecurity of Critical Infrastructure?” (blog)
- “The Time for Prioritizing Your IT/OT Cybersecurity is Now” (on-demand webinar)
6 – Don’t overlook web app security
Securing your web apps is paramount, because they’re easy to access and, if breached, can offer attackers access to a wealth of confidential data and to critical backend systems. Yet, web apps remain extremely prone to attacks. According to the “2022 Verizon Data Breach Incident Report,” web apps ranked by far as the top vector for breaches, accounting for about 70% of the 18,419 incidents analyzed.
Top vectors for incidents / breaches
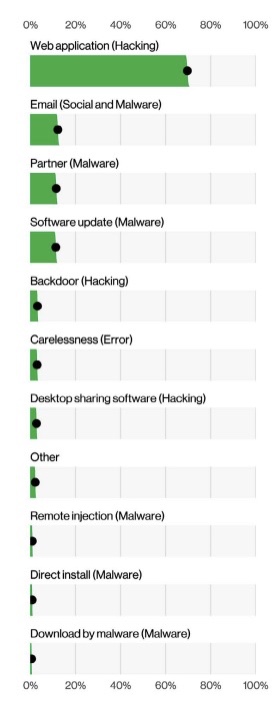
(Source: “2022 Verizon Data Breach Incident Report,” Verizon, May 2022)
That’s why you must continuously scan them for vulnerabilities, misconfigurations, certificate issues and other security flaws and weaknesses.
For more information:
- “Top 10 Web Application Security Risks” (OWASP Foundation)
- “Cloud Security Basics: Protecting Your Web Applications” (Tenable)
- “Website Security” (CISA)
- “5 application security threats and how to prevent them” (TechTarget)


