Microsoft addresses 98 CVEs including a zero-day vulnerability that was exploited in the wild.
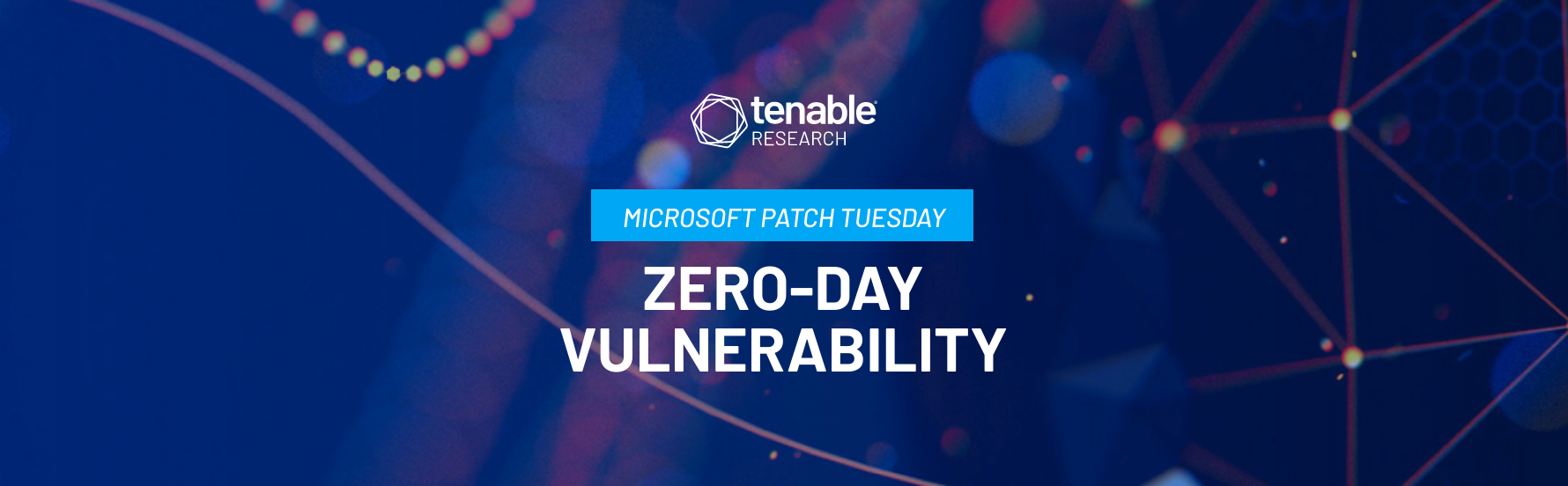
- 11Critical
- 87Important
- 0Moderate
- 0Low
Microsoft patched 98 CVEs in its January 2023 Patch Tuesday Release, with 11 rated as critical, and 87 rated as important.
This month’s update includes patches for:
- .NET Core
- 3D Builder
- Azure Service Fabric Container
- Microsoft Bluetooth Driver
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Local Security Authority Server (lsasrv)
- Microsoft Message Queuing
- Microsoft Office
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft WDAC OLE DB provider for SQL
- Visual Studio Code
- Windows ALPC
- Windows Ancillary Function Driver for WinSock
- Windows Authentication Methods
- Windows Backup Engine
- Windows Bind Filter Driver
- Windows BitLocker
- Windows Boot Manager
- Windows Credential Manager
- Windows Cryptographic Services
- Windows DWM Core Library
- Windows Error Reporting
- Windows Event Tracing
- Windows IKE Extension
- Windows Installer
- Windows Internet Key Exchange (IKE) Protocol
- Windows iSCSI
- Windows Kernel
- Windows Layer 2 Tunneling Protocol
- Windows LDAP - Lightweight Directory Access Protocol
- Windows Local Security Authority (LSA)
- Windows Local Session Manager (LSM)
- Windows Malicious Software Removal Tool
- Windows Management Instrumentation
- Windows MSCryptDImportKey
- Windows NTLM
- Windows ODBC Driver
- Windows Overlay Filter
- Windows Point-to-Point Tunneling Protocol
- Windows Print Spooler Components
- Windows Remote Access Service L2TP Driver
- Windows RPC API
- Windows Secure Socket Tunneling Protocol (SSTP)
- Windows Smart Card
- Windows Task Scheduler
- Windows Virtual Registry Provider
- Windows Workstation Service
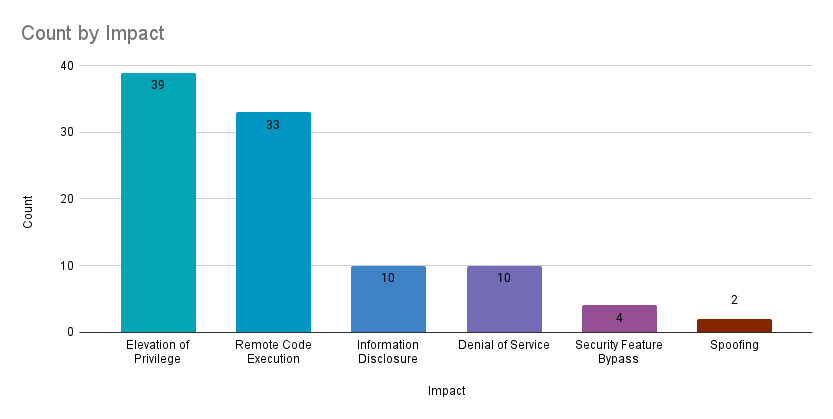
Elevation of privilege (EoP) vulnerabilities accounted for 39.8% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 33.7%.
CVE-2023-21674 | Windows Advanced Local Procedure Call (ALPC) Elevation of Privilege Vulnerability
CVE-2023-21674 is an EoP vulnerability in Windows operating systems that received a CVSSv3 score of 8.8 and has been exploited in the wild as a zero day. The vulnerability exists in the Advanced Local Procedure Call (ALPC) functionality. ALPC is a message passing utility in Windows operating systems. When exploited, an attacker can leverage the vulnerability to break out of the sandbox in Chromium and gain kernel-level execution privileges.
CVE-2023-21730 | Windows Cryptographic Services Elevation of Privilege Vulnerability
CVE-2023-21730 is an EoP in Windows operating systems that received a CVSSv3 score of 7.8. The vulnerability exists in Windows Cryptographic Services, a suite of cryptographic utilities in Windows operating systems. The vulnerability can be exploited by a remote, unauthenticated attacker. The exploit requires no user interaction and has a low attack complexity. However, according to the Microsoft Exploitability Index, exploitation is less likely. Discovery is credited to Microsoft's Offensive and Security Engineering (MORSE) team.
CVE-2023-21760, CVE-2023-21765, CVE-2023-21678 | Windows Print Spooler Elevation of Privilege Vulnerabilities
CVE-2023-21760, CVE-2023-21765, and CVE-2023-21678 are EoP vulnerabilities in Windows Print Spooler. The three vulnerabilities were assigned a CVSSv3 score of 7.8 and are rated as “Exploitation Less Likely.” CVE-2023-21678 was disclosed to Microsoft by the National Security Agency (NSA). This continues a trend observed last year, where the NSA disclosed three vulnerabilities in Print Spooler, beginning with CVE-2022-29104 and CVE-2022-29132 in May 2022 and leading to CVE-2022-38028 in October 2022.
Due to the ubiquity of the Windows Print Spooler, it has seen continued interest by researchers and attackers as an ideal target since the discovery of PrintNightmare and we expect this trend to continue for the foreseeable future.
CVE-2023-21543, CVE-2023-21546, CVE-2023-21555, CVE-2023-21556 and CVE-2023-21679 | Windows Layer 2 Tunneling Protocol (L2TP) Remote Code Execution Vulnerabilities
CVE-2023-21543, CVE-2023-21546, CVE-2023-21555, CVE-2023-21556 and CVE-2023-21679 are RCE vulnerabilities in Windows operating systems, all given a CVSSv3 score of 8.1. The vulnerabilities can be exploited by a remote, unauthenticated attacker targeting a machine acting as a Remote Access Server. However, the vulnerabilities have a high attack complexity, meaning the attacker will have to perform actions on the target prior to exploitation for it to be successful. Discovery is credited to RyeLv for CVE-2023-21543, and Yuki Chen with Cyber KunLun for the others.
CVE-2023-21763 and CVE-2023-21764 | Microsoft Exchange Server Elevation of Privilege Vulnerabilities
CVE-2023-21763 and CVE-2023-21764 are EoP vulnerabilities in Microsoft Exchange Server that received CVSSv3 scores of 7.8 and could grant an authenticated attacker SYSTEM privileges. Microsoft has rated these as “Exploitation Less Likely,” but has offered no explanation why. Piotr Bazydlo with Trend Micro Zero Day Initiative is credited with reporting both of these vulnerabilities.
CVE-2023-21745 and CVE-2023-21762 | Microsoft Exchange Server Spoofing Vulnerabilities
CVE-2023-21745 and CVE-2023-21762 are spoofing vulnerabilities in Microsoft Exchange Server that both received CVSSv3 score of 8.0. However, these flaws have distinct characteristics from one another. CVE-2023-21745 can be exploited by an adjacent attacker — either via the local area network, or over the internet — and was rated “Exploitation More Likely.” It was reported by Piotr Bazydlo with Trend Micro Zero Day Initiative. On the other hand, CVE-2023-21762 also requires an adjacent attacker, but is restricted to a shared physical or local network, or an “otherwise limited administrative domain.” Successful exploitation could lead to disclosure of New Technology LAN Manager (NTLM) hashes and NTLM relay attacks.
CVE-2023-21746 | Windows NTLM Elevation of Privilege Vulnerability
CVE-2023-21746 is an EoP vulnerability in Windows NTLM that received a CVSSv3 score of 7.8 and was rated “Exploitation Less Likely.” Successful exploitation would allow an attacker to gain SYSTEM privileges. It was disclosed by Andrea Pierini with Semperis and Antonio Cocomazzi with Sentinel One.
Tenable Solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains January 2023.
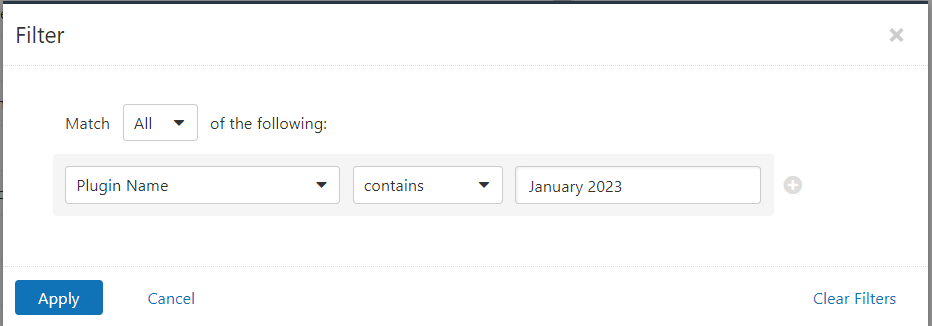
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
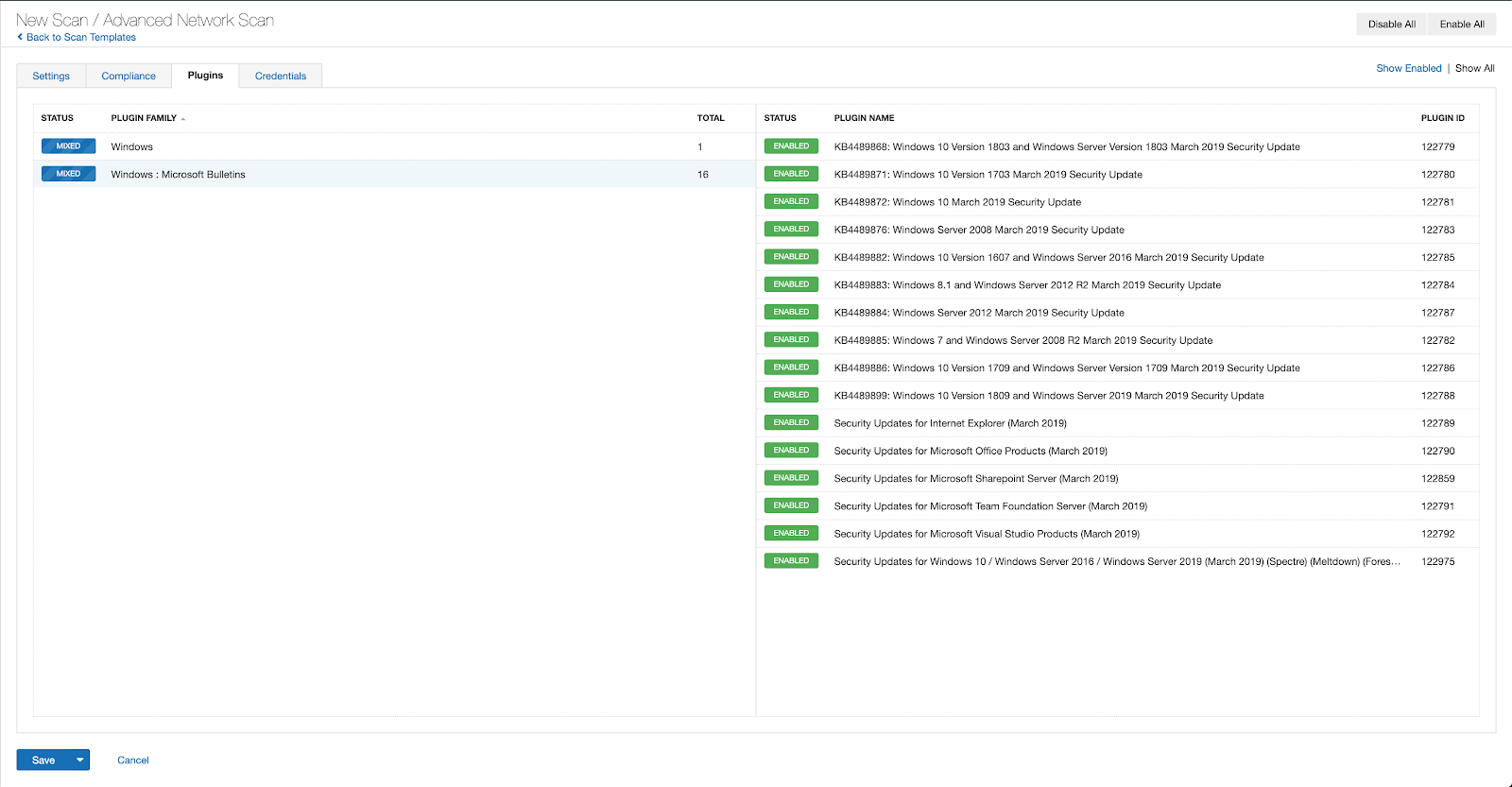
A list of all the plugins released for Tenable’s January 2023 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's January 2023 Security Updates
- Tenable plugins for Microsoft January 2023 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.