Learn about a new guide packed with best practices recommendations to improve IAM systems security. Plus, cybersecurity ranks as top criteria for software buyers. Also, guess who’s also worried about ChatGPT? Oh, and do you know what a BISO is? And much more!
Dive into six things that are top of mind for the week ending March 24.
1 - Best practices to boost IAM security from CISA and NSA
Feel like your organization could boost the security of its identity and access management (IAM) systems? You might want to check out a guide published this week by the U.S. government titled “Identity and Access Management Recommended Best Practices Guide for Administrators.”
Created by the Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA), the document seeks to help organizations better prevent, detect and respond to IAM attacks.
Specifically, CISA and the NSA offer IAM security best practices focused on five areas:
- Proper, centralized, policy-based IAM governance that strengthens enterprise IT security and regulatory compliance
- Techniques and methods to harden the IT environment and make it harder for threat actors to launch successful IAM attacks
- Implementation of identity federation and single sign-on, both of which beef up IAM security
- Adoption of multi-factor authentication, which reduces the chances that bad actors will compromise user accounts
- Establishment of effective IAM monitoring and auditing processes to make it easier to detect suspicious activity

For more information about IAM security, check out these Tenable resources:
- “Eliminating Attack Paths in Active Directory: A closer look at preventing privilege escalations” (white paper)
- “Adopt a Proactive Process for Detecting and Preventing Critical Attack Paths in AD” (on-demand webinar)
- “Active Directory Security Needs Immediate Attention: CIOs and CISOs Can Make All the Difference” (white paper)
- “Active Directory Holds the Keys to Your Kingdom, But Is It Secure?” (Frost & Sullivan white paper)
- “How Automated Discovery of AD Threats Eliminates Blind Spots and Makes Your SOC Identity Aware” (on-demand webinar)
2 - Study: Security is top of mind for software buyers
Security is the main factor that U.S. businesses take into consideration when buying software It also plays a large part in their decision to stop using a software product.
That’s according to the “Security Features Survey” released this week by Capterra, an online marketplace for software and tech services. The report is based on a survey of 289 respondents involved in their companies’ software purchasing process.
The report features interesting findings about how and why organizations assess the security features of cloud and on-prem software they’re considering for purchase, including:
- Half of respondents rank security as the most important criteria when choosing a software product
- 45% of surveyed organizations have stopped using a software product as a result of security concerns
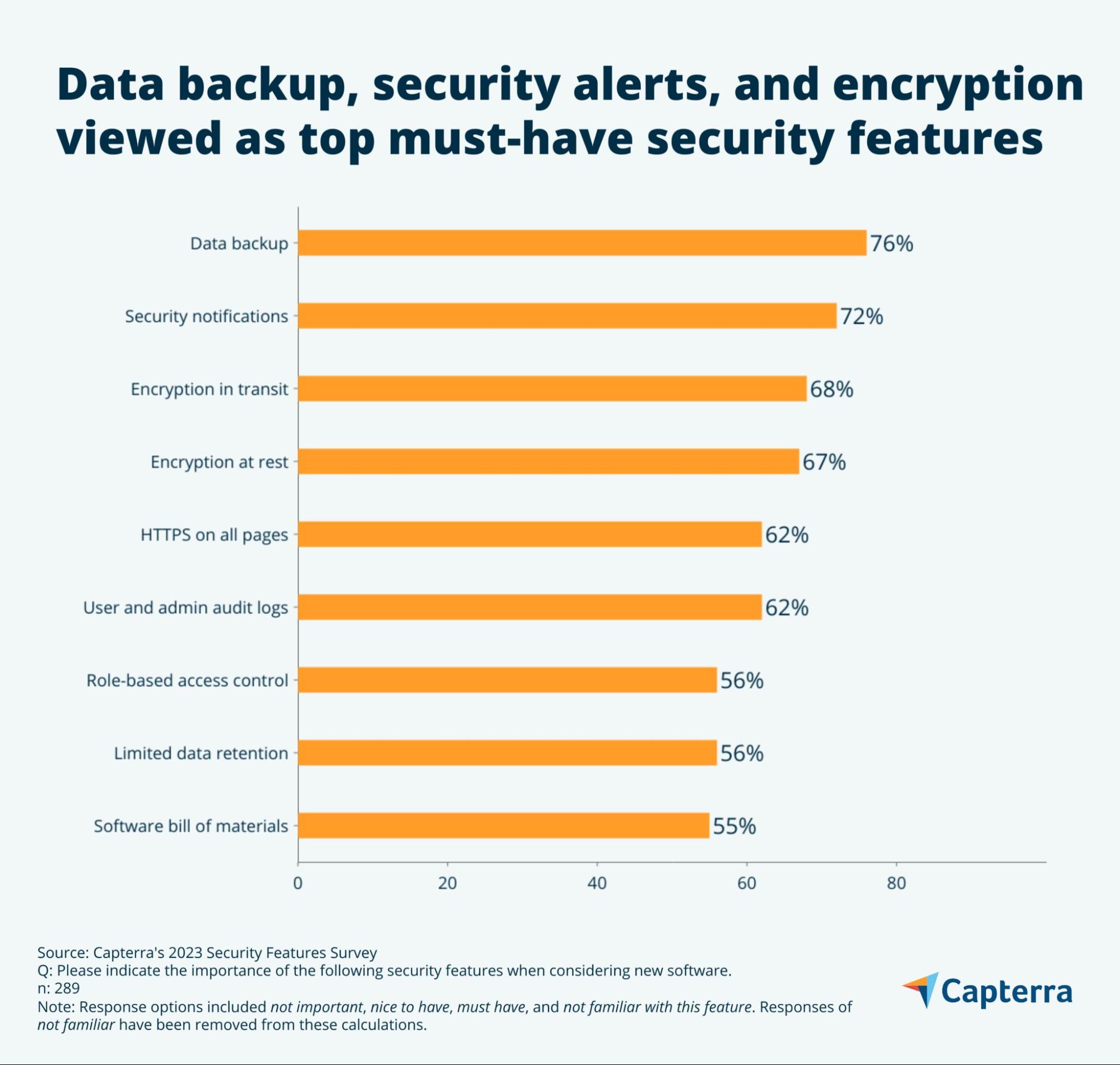
- The top “must have” security features are data backup capabilities, vendor security notifications, and in-transit and at-rest encryption
The report also found that the use of two-factor authentication jumped from 64% in 2021 to 92% last year, and that software buyers are not only interested in traditional password-based authentication but also in emerging methods, including software tokens (52%), hardware tokens (40%) and biometric authentication (39%).
Moreover, many respondents said they place importance on product security certifications and security attestations from technology industry organizations like the Cloud Security Alliance and the Payment Card Industry, and from government agencies like the U.S. National Institute of Standards and Technology.
For more information about the importance of prioritizing strong security features in software-purchasing decisions:
- “CISA director calls on tech companies to build security into products” (Axios)
- “Commercial Software Assessment Guideline” (Univ. of California at Berkeley)
- “CISA issues supply chain security guide for software buyers” (Tenable)
- “Best practices for boosting supply chain security” (ComputerWeekly)
- “Biden National Cyber Strategy Seeks to Hold Software Firms Liable for Insecurity” (The Wall Street Journal)
3 - SEC wants securities market players to boost cybersecurity
The U.S. Securities and Exchange Commission has proposed new requirements for stronger cybersecurity measures and controls from participants in U.S. securities markets, including broker-dealers, clearing agencies and national securities exchanges.

The SEC’s proposed new requirements for these organizations include:
- Immediately inform the SEC via “written electronic notice” of any “significant” cybersecurity incident they suffer
- Have and enforce written policies and procedures that address their cybersecurity risks
- Review and assess the effectiveness of these policies and procedures at least annually
For more information, you can read the SEC’s announcement, fact sheet and the full proposed rule, as well as coverage and commentary from The Record, Security Magazine, Davis Polk, Retail Banker International and The Wall Street Journal.
4 - Ransomware threat against EU transport skyrockets in 2022
Transportation providers in the European Union experienced an upswing in ransomware, denial of service and supply chain attacks in 2022.
That’s according to the European Union Agency for Cybersecurity’s “ENISA Threat Landscape: Transport Sector” report, which was released this week.
The report analyzed cyber incidents targeting EU providers of aviation, maritime, railway and road transport between January 2021 and October 2022.
Main Threats to EU Transport Sector
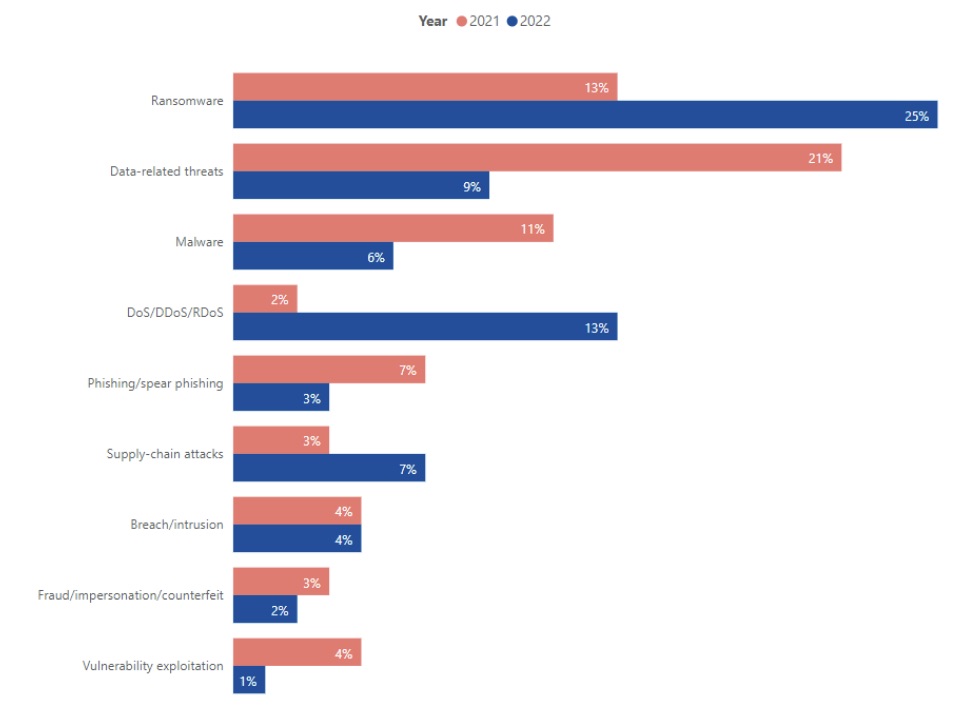
(Source: “ENISA Threat Landscape: Transport Sector”, March 2023)
Overall for the 22 month-period, ransomware emerged as the main cyberthreat impacting transportation providers, accounting for 38% of incidents, followed by data-related attacks (30%).
Most cyberattacks against the transport sector were carried out by cybercriminals (55%) motivated by financial gain, followed by hacktivists (23%) seeking to effect political or social change.
Types of Cyberthreat Actors Targeting EU Transportation Organizations
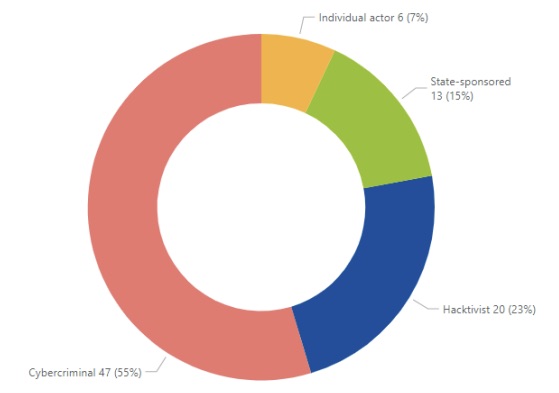
(Source: “ENISA Threat Landscape: Transport Sector”, March 2023)
In terms of the highest impact of the cyberattacks, services ranked as the most affected (28%), followed by data (26%) and IT systems (18%). On a positive note, ENISA states that for the period covered, it didn’t receive any reliable report of a cyberattack compromising the safety of transport.
ENISA also found that the majority of cyberattacks against transportation providers were aimed at their IT systems, while operational technology (OT) systems were “rarely targeted,” although the agency expects ransomware groups to “target and disrupt” OT operations “in the foreseeable future.”
For more information, you can read the full report and the report announcement, as well as coverage from The Record, Infosecurity Magazine, SecurityWeek and International Railway Journal.
5 - OpenAI CEO worries about the potential to abuse ChatGPT
Add OpenAI’s chief executive to the ranks of people who feel uneasy about malicious uses of ChatGPT, his company’s ultra-famous generative AI chatbot, and of similar AI technologies.
In an interview last week with ABC News, Sam Altman expressed extreme optimism about artificial intelligence’s potential to benefit society, saying it can be “the greatest technology humanity has yet developed."
However, he conceded that he also worries about potential abuse. "I'm particularly worried that these models could be used for large-scale disinformation," Altman said. "Now that they're getting better at writing computer code, [they] could be used for offensive cyberattacks."
While Altman said OpenAI will continue to develop ChatGPT to prevent malicious uses of it, the generative AI chatbot has already reportedly been used to create malware, write phishing emails and spread falsehoods. And this week it was reported that a ChatGPT bug exposed the titles of some users' conversations with the chatbot.
For more information about cybersecurity concerns regarding ChatGPT and other generative AI tools like it, check out these Tenable blogs:
- “OpenAI’s ChatGPT and GPT-4 Used as Lure in Phishing Email, Twitter Scams to Promote Fake OpenAI Tokens”
- “Cybersecurity Snapshot: A ChatGPT Special Edition About What Matters Most to Cyber Pros”
- “Amid ChatGPT furor, U.S. issues framework for secure AI”
- “Check out our animated Q&A with ChatGPT”
- “U.K. cyber agency: Tread carefully when feeding data to ChatGPT”
- “ChatGPT gets jailbroken … and heartbroken?”
VIDEO
Anatomy of a Threat: GPT-4 and ChatGPT Used as Lure in Phishing Scams Promoting Fake OpenAI Tokens
6 - What’s a BISO? Do you need one?
In recent years, a new security executive role has emerged in enterprises and steadily gained traction: the BISO, or business information security officer. As the role continues to be discussed, more organizations may wonder if they’d benefit from hiring a BISO. Here are some resources to help you figure this out.
You can start with a well-researched feature story SecurityWeek published just last week titled “The Rise of the BISO in Contemporary Cybersecurity,” which examines how the role has evolved and includes interviews with various security leaders and with multiple BISOs themselves.
Next, you might want to check out a blog IANS Research posted also last week titled “Guidelines for the BISO Role,” which offers its explanation of what a BISO does – “connects the dots between the central security agenda and the various divisional CIOs” – and then dives deeper into the role’s responsibilities and desired skills, before providing a full-blown BISO job description.
Meanwhile, Cybersecurity Guide this week updated its “Business information security officer: A complete career guide” article, which, while aimed at folks interested in becoming BISOs, offers great insight into the potential value of the role for some organizations. Another good deep dive into the BISO role is CSO Online’s feature “The BISO: bringing security to business and business to security,” which ran earlier this year.
To get a sense about the compensation BISOs command, you can check out this Glassdoor page about BISO salaries.
While it’s not exclusively about BISOs, a blog Tenable Chief Security Officer Robert Huber published in 2020 about the importance of aligning cybersecurity and business mentions the role, noting that “the vast majority of business-aligned organizations (80%) have a BISO or similar title.”
You may also find these videos useful:
Business Information Security Officer: A Cybersecurity Secret Weapon (RSA Conference)
The Rise of the BISO Role (RSA Conference)
