Handling end-of-life conditions for software and hardware products is complicated by different stages and definitions. Tenable is leading the way on defining these disparate vulnerabilities under a comprehensive Security End of Life framework that addresses the common risk exposure to our customers.
Since its founding, Tenable has worked closely with our customers to help them address the vulnerabilities, misconfigurations and out-of-compliance conditions that can be exploited by attackers to breach an organization. Today, Tenable Research is taking another major step to help our customers better manage when commonly used software and hardware products are no longer receiving security updates. Tenable Research refers to this as Security End-of-Life (SEoL).
We hear from our customers that SEoL is a pain point for them and presents particular challenges for their security teams. Among those challenges are:
- A lack of standardization for how SEoL events are announced/reported
- How they can detect SEoL products in their IT environments
- How they should prioritize the impact of SEoL vulnerabilities
To help address these challenges, Tenable Research has redefined its strategy on how we detect and communicate the end of vendor support for hardware and software security updates. Our new Security End-of-Life Plugin program leverages our industry leadership and extensive customer telemetry to create a single holistic framework that covers all SEoL definitions. We believe the benefits of creating a scalable framework for this program are:
- Standardizing the way we find out about SEoL products
- Standardizing how we create the plugins to detect them
- Standardizing how we communicate the severity of those detections to our customers
- An increase in Tenable coverage for SEoL software/hardware products
This blog covers what these conditions are, why they are important for customers to know about and how Tenable Research is leading the way.
What is meant by Security End of Life?
When a software or hardware product reaches the “Security End-of-Life” state, it means that it will no longer receive any more security updates from the vendor. Without security updates, the risk of that software being compromised grows over time. As the vulnerability landscape changes, hackers and cybercriminals regularly leverage vulnerabilities in EoL products that are still present in people's environments. Why? Because organizations have not effectively patched them. The recently published 2022 Threat Landscape Report by Tenable Research provides a number of examples where cybercriminals did just that. For example, CVE-2017-11882 is a memory corruption vulnerability in the Equation Editor component of Microsoft Office that could lead to remote code execution (RCE) and received a CVSSv3 score of 7.8. It has been exploited in attacks by diverse threat actors and is incorporated into some of the top malware strains.
We view products in the SEoL state as a vulnerability type that needs to be detected, analyzed and remediated, just like any other security weakness or misconfiguration. However, end of vendor support for security updates does not mean that a product is immediately less secure the day after vendor support ends. If the product still functions as it should and there are no known exploits or reports of security issues, then the product should generally be trusted in an environment with plans to replace the capability soonest. The need for a dynamic and data-driven security framework is the need that SEoL is designed to fulfill.
Lack of standardization
The problem is that there is no industry-wide standard for addressing SEoL conditions. There is no standard way for vendors to alert vulnerability management providers about impending SEoL conditions, meaning there is no standard way for the users of those products to know they are exposed. There is no consistent way of rating the severity associated with detected SEoL products, which leads to confusion and sometimes faulty guidance from vulnerability management providers on how critical a SEoL product is.
Organizations understand these problems and have been looking for a way for their vulnerability management providers to solve them. That is why standardizing how Tenable provides detection and management of SEoL products has been the most requested feature enhancement from our customers.
Tenable Research understands these problems as well. That is why we reached out to many of our customers to discuss this problem in depth and to get a feel for what they needed to properly address this issue. Combining this feedback with our extensive subject matter expertise, Tenable Research has created its Security End-of-Life plugin program.
Tenable’s Security End-of-Life plugin program
This program provides a new approach to managing products that have reached the SEoL phase. This new approach is based on creating a scalable framework that will standardize the way we find out about SEoL products, standardize how we create the plugins to detect them and standardize how we communicate the severity of those detections to our customers.
The creation of this SEoL program within Tenable Research is key to addressing a number of these problems. Let’s start by describing the different ways a product may take to arrive at the SEoL stage:
- Announced - A product vendor announces that the product will no longer receive security updates or fixes
- Abandoned - A product that stops addressing security vulnerabilities despite not having issued a formal SEoL announcement
- Third party advisements - Protocols and services not recommended for use after a certain date by security or industry governing bodies due to security concerns
By setting up processes that will scan vendor security maintenance lifecycle data sources and ingest machine readable SEoL information from vendors, Tenable Research is adopting a consistent and scalable method for ensuring that Tenable provides coverage on as many SEoL products as possible. For products and protocols that don’t have an identified vendor associated with them Tenable Research will work with certification bodies, other organizations and our world-class internal subject matter experts to flag those products as SEoL.
For products that have reached SEoL, Tenable Research is standardizing how the detection plugins are built. Prior plugin development for SEoL products lacked comprehensive criteria for what constituted a end of life event or what the criticality of this event. Tenable Research’s subject matter experts have engineered a dynamic and well-defined framework that standardizes which SEoL-related information, conditions and variables are needed. The end result? We can automate the creation of the SEoL plugins. While we will still build SEoL plugins manually when the situation requires it, this plugin framework provides a solid foundation for adding more SEoL coverage at a faster pace.
The operational impact
One of the main objectives in our design process for this new SEoL plugin program has been to help our customers better manage the impact of SEoL detections on their operations. As described above, we’re addressing customer concerns over the lack of coverage for SEoL products and the lack of consistency in how those detections are made. Our new SEoL plugin framework will increase our coverage and standardize our detection capabilities. In addition, these new SEoL plugins will only produce findings once the SEoL date has been reached, thereby reducing noise and false alerts.
Another area of concern we wanted to address was the severity ratings associated with SEoL detections. Even though SEoL products are a recognized vulnerability for all organizations, not all SEoL products are critical in nature. Previous SEoL plugins were created with severities of High OR Critical, which could introduce a large interruption into our customer operations. Defaulting to High or Critical was inconsistent with Tenable’s product philosophy of providing guidance to help our customers prioritize their workflows as to which vulnerabilities need to be addressed first.
That is why under our new program the default severity level for a SEoL detection plugin will be set at Informational. Existing Unsupported type plugins from Tenable will be deprecated over time and replaced with plugins created through this new program. It is important to note that the severity will retain its originating value upon conversion.
In a future iteration of the Security End of Life initiative, Tenable Research is exploring a mechanism capable of analyzing a number of factors combined with its rich vulnerability intelligence to determine if a given severity rating will need to be raised. By starting with an Informational severity as the default, this new plugin framework will not cause Tenable customers to have to drop what they are doing and remediate all newly discovered SEoL detections. For those times when a particular SEoL product or conditions warrant it, the severity level will be raised to alert them when critical ones are discovered in their environment.
Finally, we are introducing two new dashboards to help customers in the day-to-day management of SEoL products in Tenable Security Center (formerly Tenable.sc) and Tenable Vulnerability Management (formerly Tenable.io). The first is the Security End of Life Summary table that displays products that have entered the Security End of Life state of the security maintenance lifecycle. The plugin name, severity and total count will be displayed and users can drill down into the data to obtain a vulnerability summary where additional details on each identified SEoL finding can be viewed (see example below).
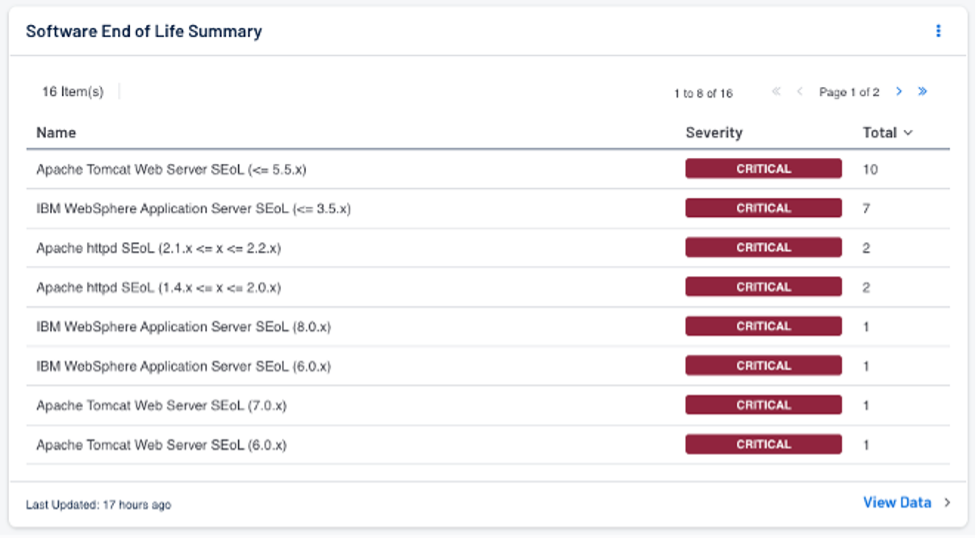
Source: Tenable, April 2023
The second dashboard, the Security End of Life by product family bar chart will display the products that have entered the SEoL state of the security maintenance lifecycle. The product family and total count will be displayed, and users can drill down into the data to obtain a vulnerability summary where additional details on each identified vulnerability can be viewed (see example below).
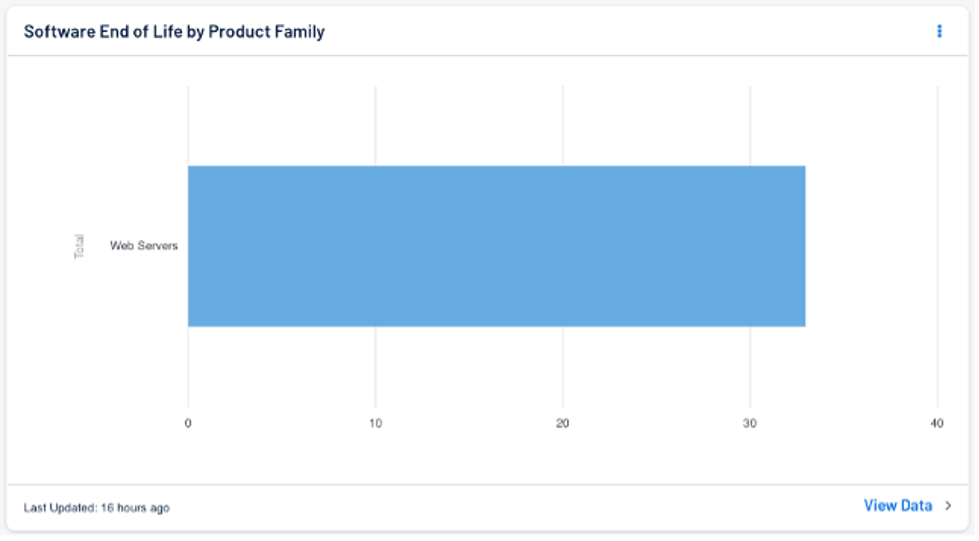
Source: Tenable, April 2023
Conclusion
The mission of Tenable Research has always been about eliminating the attacker’s advantage and helping our customers leverage our vulnerability expertise and insights to reduce their cyber risk. The SEoL plugin program is another example of that mission.
With the introduction of the Security End-of-Life plugin program, Tenable Research aims to provide our customers a standardized solution to an often overlooked vulnerability type. This program will increase the coverage of products that have reached the SEoL state through standardization and automation, reduce the operational impact by developing a better way to communicate the severity of these vulnerabilities and simplify management through the introduction of relevant dashboards.
Learn more
- Visit the Tenable Community to access the Security End of Life Plugins FAQ
