Check out a hair-raising warning from AI experts. Plus, find out why securing identities is getting harder than ever – and how to fix it. Also, how a cloud security framework can help you – a lot. In addition, check out nifty SaaS security tips. And much more!
Dive into six things that are top of mind for the week ending June 2.
1 – Experts warn of nuclear-scale “extinction” risk from AI
And this week we’re starting the blog on a happy note by relaying this warning: As artificial intelligence technology gets more sophisticated, AI systems could wipe out the human race if the risk of misuse and abuse isn’t properly mitigated.
So said a dream team of AI experts in an ominous statement released this week.
“Mitigating the risk of extinction from AI should be a global priority alongside other societal-scale risks such as pandemics and nuclear war,” reads the one-line statement from the Center for AI Safety. Signatories include “AI godfather” Geoffrey Hinton and Sam Altman, CEO of ChatGPT-creator OpenAI.

In an accompanying press release, the Center for AI Safety Director Dan Hendrycks urged “global action” in anticipating and addressing risks from future, more advanced AI systems, including human extinction.
Alrighty then.
Should you want a deeper dive into this topic of catastrophic AI risks, you can nuke a bag of popcorn and plop down on your couch to watch Hendrycks’ recent video “AI and Evolution.”
For more information about AI cybersecurity risks, check out these Tenable blogs:
- “How Enterprise Cyber Leaders Can Tame the ChatGPT Beast”
- “CSA Offers Guidance on How To Use ChatGPT Securely in Your Org”
- “As ChatGPT Fire Rages, NIST Issues AI Security Guidance”
- “A ChatGPT Special Edition About What Matters Most to Cyber Pros”
- “ChatGPT Use Can Lead to Data Privacy Violations”
2 – Tool sprawl, technical complexity hamper identity security
We’ve got a problem securing digital identities.
A whopping 90% of organizations suffered at least one identity breach in the past year, up from 84% in the prior 12-month period, according to a survey released this week by the Identity Defined Security Alliance (IDSA) and conducted by Dimensional Research.
The good news? Almost all respondents (97%) plan to increase their investments in the coming year in “security outcomes,” the term the IDSA uses for 19 best practices designed to beef up the protection of identities.
Some of these best practices include:
- Grant and remove regular and privileged user accounts through governance-driven provisioning
- Use device characteristics and expected user behavior for authentication
- Make sure all privileged access requires multi-factor authentication and is periodically attested
- Follow the principle of least privilege to ensure access rights are continuously discovered and granted

So what’s behind this identity security problem? Here’s what emerged from the survey, which polled 529 respondents who are directly responsible for IT security or identities at companies with more than 1,000 employees:
- The top two roadblocks are the complication of identity frameworks – due to multiple vendors and architectures – and complex technical environments
- Other obstacles include insufficient budget, expertise, standards, people and governance
- Only 49% of leaders at polled organizations grasp identity risks and proactively invest in security before an incident occurs
- Cloud adoption is the number one cause for the rise in identities, followed by increases in remote work, mobile usage and third-party relationships
To get more details about the “2023 Trends in Securing Digital Identities” report, read the announcement, download the report and check out the IDSA recommendations.
For more information about identity and access management security, check out these Tenable resources:
- “Eliminating Attack Paths in Active Directory: A closer look at preventing privilege escalations” (white paper)
- “Adopt a Proactive Process for Detecting and Preventing Critical Attack Paths in AD” (on-demand webinar)
- “Active Directory Security Needs Immediate Attention: CIOs and CISOs Can Make All the Difference” (white paper)
- “Active Directory Holds the Keys to Your Kingdom, But Is It Secure?” (Frost & Sullivan white paper)
- “Best practices to boost IAM security from CISA and NSA” (blog)
3 – How to nail the UX of passkeys, the password alternative
Looking to deploy passkeys in your organization as you move away from passwords? You might want to check out a new guide from the FIDO Alliance about getting passkeys’ user experience (UX) right.
The 44-page guide, published this week and titled “FIDO Alliance UX Guidelines for Passkey Creation and Sign-ins,” details 10 UX principles and three content principles, along with resources including a UX architecture diagram and a demo video.
Based on FIDO standards, passkeys are faster, easier and safer than passwords, according to the FIDO Alliance, a tech industry consortium that promotes alternative login technologies and authentication standards.
However, passkeys’ user experience is different, so the guide aims to help online service providers “ensure a consistent, thoughtful, and simple user experience for their users” when rolling out passkeys, said FIDO Alliance Executive Director Andrew Shikiar.
The FIDO Alliance’s UX principles for passkeys include:
- Prompt people to create passkeys while they’re doing account-management tasks, such as account creation or recovery, and not while shopping or signing-in
- Make passkeys a prominent option in account settings, on par with the username, password and multi-factor authentication
- Create a “hero” prompt for passkeys with specific symbols, headline, messaging and call to action
Example of a hero prompt for passkeys
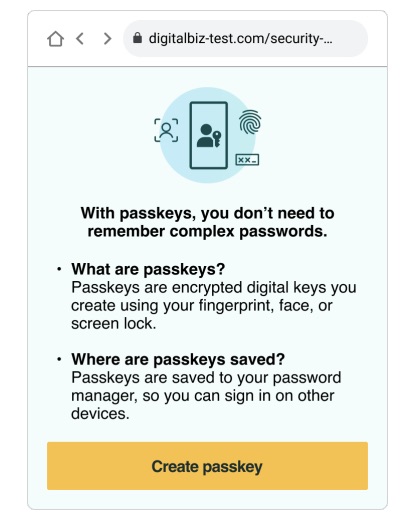
(Credit: FIDO Alliance)
To get more details, check out the report’s announcement, a report resources page, the full report and a passkeys page.
4 – The case for adopting a cloud cybersecurity framework
As companies increase their use of cloud computing, they must extend their security and compliance controls accordingly to these new environments – but that is easier said than done. How can security teams ramp up their cloud security efforts methodically, precisely and effectively?
Start by adopting a cloud cybersecurity framework, such as those from the Cloud Security Alliance (CSA), the International Organization for Standardization (ISO) and the U.S. National Institute of Standards and Technology (NIST).
That’s the recommendation from Steve Durbin, CEO of the Information Security Forum (ISF), a non-profit organization which provides research, tools and guidance on information security and risk management.

“A cloud cybersecurity control framework provides a systematic approach to identifying, assessing, and mitigating security risks. It provides step by step guidance on what security controls should be implemented by which parties across the entire cloud supply chain,” he wrote this week in a Help Net Security article titled “Why organizations should adopt a cloud cybersecurity framework.”
He highlights four key advantages of adopting a cloud cybersecurity framework:
- It provides a holistic view of security and of evolving security requirements
- It streamlines compliance tasks
- It helps define required tools, processes, rules, expectations and responsibilities
- It helps prioritize security investments and prevent overspending
For more information about cloud cybersecurity frameworks:
- “Top cloud security standards and frameworks to consider” (TechTarget)
- “Understanding the 5 Most Important Cybersecurity Frameworks” (Acceleration Economy)
- “Cloud Security Technical Reference Architecture” (CISA)
- “7 Regulatory and Compliance Frameworks with Broad Cloud Security Implications” (Tenable)
VIDEOS
Tenable Cloud Security Coffee Break: The Challenges of Multi-cloud Compliance (Tenable)
NIST Cybersecurity Framework for cloud (Cloud Security Architecture)
5 – Tighten your SaaS application security with these tips
And you can never have enough information about securing software-as-a-service (SaaS) apps, so here are a few recommendations IANS Research made recently on its blog:
- Reduce the number of SaaS apps at your company by weeding out consumer-grade ones designed for personal use and keeping those built for workplace use
- Be proactive and quick about approving and blocking SaaS apps, so that you provide secure, enterprise-grade options to employees
- Choose app versions that offer the security features you need, and activate and configure these security controls so they’re on by default for all your users
- Train employees in how to use SaaS apps securely and establish simple, clear usage rules
For more information about SaaS security specifically, and cloud security in general, check out these Tenable blogs:
- “Organizations struggle with SaaS data protection”
- “Cloud Security Basics: Protecting Your Web Applications”
- “Don’t downplay SaaS security”
- “Revisiting CSA’s top SaaS governance best practices”
- “Identifying XML External Entity: How Tenable.io WAS Can Help”
VIDEOS
Tenable Cloud Security Coffee Break: Web app security
2023 will be the year of SaaS security | Tenable at Web Rio Summit 2023
6 – Proposed U.S. law seeks disclosure of apps’ geographical origin
Legislation introduced this week in the U.S. Senate would require the Apple App Store, the Google Play Store and other app shops to disclose where apps are developed and owned.
The bill is known as the “Know Your App Act” and was introduced by Sen. Tim Scott from South Carolina, Sen. Roger Wicker from Mississippi and Sen. James Lankford from Oklahoma, all three from the Republican Party.
The introduction of the “Know Your App Act” comes as politicians from both major parties debate whether TikTok should be banned due to concerns that its maker, the Chinese company ByteDance, may be sharing U.S. users’ data with the Chinese government.

“Our adversaries will exploit every available tool, including popular apps that gather huge amounts of data on Americans, to gain an advantage over the United States,” Senator Wicker said in a statement. “It is crucial for users to take steps to limit their exposure and be made aware of the risks associated with using foreign-controlled apps.”
To get more details, you can read the bill and check out its announcement.
For more information about the TikTok controversy:
- “Bipartisan opposition to banning TikTok emerges on Capitol Hill” (NBC News)
- “How could the US ban TikTok?” (The Hill)
- “Despite growing support in Congress for a TikTok ban, Hawley fails to force his bill forward” (Kansas City Star)
- “TikTok congressional hearing: CEO Shou Zi Chew grilled by US lawmakers” (Reuters)
VIDEOS
Tenable CEO Amit Yoran discusses proposed U.S. TikTok ban on CNN
Tenable Cyber Watch: U.S. Government Mulls TikTok Ban
