Microsoft addresses 70 CVEs in its June 2023 Patch Tuesday update including six rated as critical.
- 6Critical
- 62Important
- 1Moderate
- 1Low
Microsoft Patched 70 CVEs in its June Patch Tuesday Release, with six rated as critical, 62 rated as important, 1 rated as moderate and 1 rated as low. As part of its Patch Tuesday release, Microsoft published several non-Microsoft CVEs including five vulnerabilities for GitHub and three vulnerabilities for AutoDesk. We did not include these advisories in our overall Patch Tuesday counts.

This month’s update includes patches for:
- .NET Core
- 3D Builder
- Azure Service Fabric Container
- Microsoft Bluetooth Driver
- Microsoft Edge (Chromium-based)
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Local Security Authority Server (lsasrv)
- Microsoft Message Queuing
- Microsoft Office
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft WDAC OLE DB provider for SQL
- Visual Studio Code
- Windows ALPC
- Windows Ancillary Function Driver for WinSock
- Windows Authentication Methods
- Windows Backup Engine
- Windows Bind Filter Driver
- Windows BitLocker
- Windows Boot Manager
- Windows Credential Manager
- Windows Cryptographic Services
- Windows DWM Core Library
- Windows Error Reporting
- Windows Event Tracing
- Windows IKE Extension
- Windows Installer
- Windows Internet Key Exchange (IKE) Protocol
- Windows iSCSI
- Windows Kernel
- Windows Layer 2 Tunneling Protocol
- Windows LDAP - Lightweight Directory Access Protocol
- Windows Local Security Authority (LSA)
- Windows Local Session Manager (LSM)
- Windows Malicious Software Removal Tool
- Windows Management Instrumentation
- Windows MSCryptDImportKey
- Windows NTLM
- Windows ODBC Driver
- Windows Overlay Filter
- Windows Point-to-Point Tunneling Protocol
- Windows Print Spooler Components
- Windows Remote Access Service L2TP Driver
- Windows RPC API
- Windows Secure Socket Tunneling Protocol (SSTP)
- Windows Smart Card
- Windows Task Scheduler
- Windows Virtual Registry Provider
- Windows Workstation Service
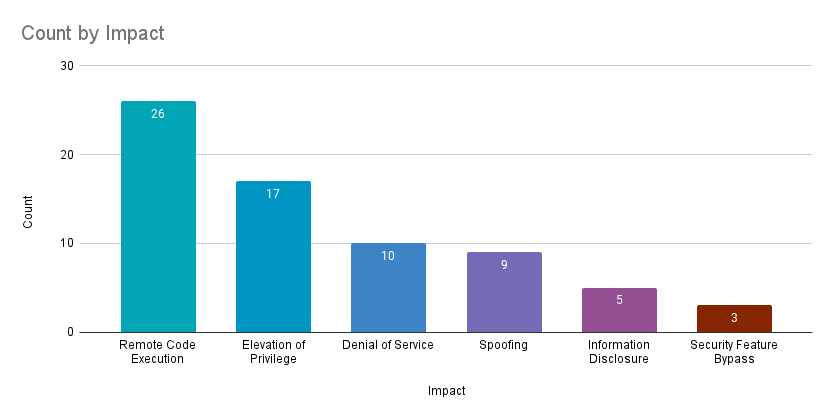
Remote code execution (RCE) vulnerabilities accounted for 37.1% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 24.3%.
CVE-2023-29357 | Microsoft SharePoint Server Elevation of Privilege Vulnerability
CVE-2023-29357 is an EoP vulnerability in Microsoft SharePoint Server 2019 that was assigned a CVSSv3 score of 9.8 and rated critical. A remote, unauthenticated attacker can exploit the vulnerability by sending a spoofed JWT authentication token to a vulnerable server giving them the privileges of an authenticated user on the target. According to the advisory, no user interaction is required in order for an attacker to exploit this flaw. Microsoft also provides mitigation guidance for the vulnerability that says users that use Microsoft Defender in their SharePoint Server farm(s) and have AMSI enabled are not affected. CVE-2023-29357 was given a rating of “Exploitation More Likely” according to Microsoft’s Exploitability Index.
According to Trend Micro’s Zero Day Initiative (ZDI), CVE-2023-29357 was used during the March Pwn2Own Vancouver contest during a successful demonstration of a chained attack. ZDI notes that while Microsoft recommends enabling AMSI as a mitigation, they have “not tested the efficacy of this action.”
CVE-2023-29363, CVE-2023-32014 and CVE-2023-32015 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
CVE-2023-29363, CVE-2023-32014 and CVE-2023-32015 are RCEs in Windows operating systems that were each given a CVSSv3 of 9.8 and rated critical. The vulnerability lies in the operating systems’ implementation of Pragmatic General Multicast (PGM), an experimental multicast protocol, in the Windows message queueing service component. A remote, unauthenticated attacker could exploit these flaws by sending a malicious file to a vulnerable target. Microsoft’s mitigation guidance states that for a system to be vulnerable, it must have message queueing services enabled.
CVE-2023-29363 is credited to Jarvis_1oop of vulnerability research institute, who also disclosed CVE-2023-28250, another critical RCE vulnerability affecting Windows PGM that was patched in April’s Patch Tuesday release.
As successful exploitation of these vulnerabilities requires that the Windows message queueing service is enabled, Tenable customers can utilize Plugin ID 174933 to identify systems which have the service running.
CVE-2023-28310 and CVE-2023-32031 | Microsoft Exchange Server Remote Code Execution Vulnerability
CVE-2023-28310 and CVE-2023-32031 are RCEs in several versions of Microsoft Exchange Server that are both rated as important and assigned CVSSv3 scores of 8.0 and 8.8 respectively.
CVE-2023-28310 can be exploited by an authenticated attacker on the local network to execute commands on the target through a remote PowerShell Session. CVE-2023-32031 allows a remote, authenticated attacker to target server accounts using network calls to trigger arbitrary code execution. Both CVE-2023-32031 and CVE-2023-28310 were given a rating of “Exploitation More Likely” and affect Microsoft Exchange Server 2016 Cumulative Update 23 and 2019 Cumulative Updates 12 and 13.
CVE-2023-29362 | Remote Desktop Client Remote Code Execution Vulnerability
CVE-2023-29362 is a RCE in Windows operating systems that was given a CVSSv3 score of 8.8 and rated as important. The flaw lies in the Remote Desktop Client component of Windows operating systems and the Remote Desktop Client for Windows Desktop application. The vulnerability can be exploited by a remote, unauthenticated attacker with control over a Remote Desktop Server, when a user connects to an attacker controlled Server using the vulnerable client.
Windows 10 21H2 End Of Life
Microsoft announced that Windows 10 21H2 has reached its end of life for Home, Pro, Pro Education, and Pro for Workstations editions. This means that users of these versions of Windows 10 21H2 will no longer receive security updates and should upgrade as soon as possible. Plugin ID 170963 can be used to identify hosts that have unsupported installations of Windows 10 version 21H2.
Tenable Solutions
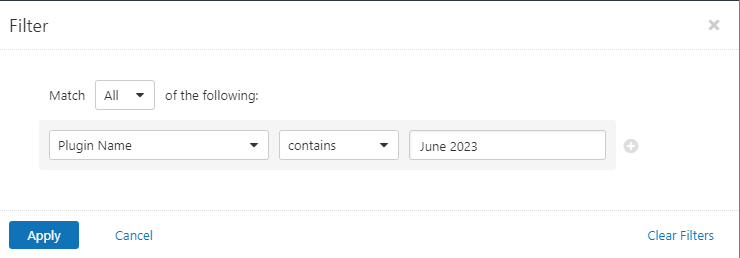
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains June 2023.
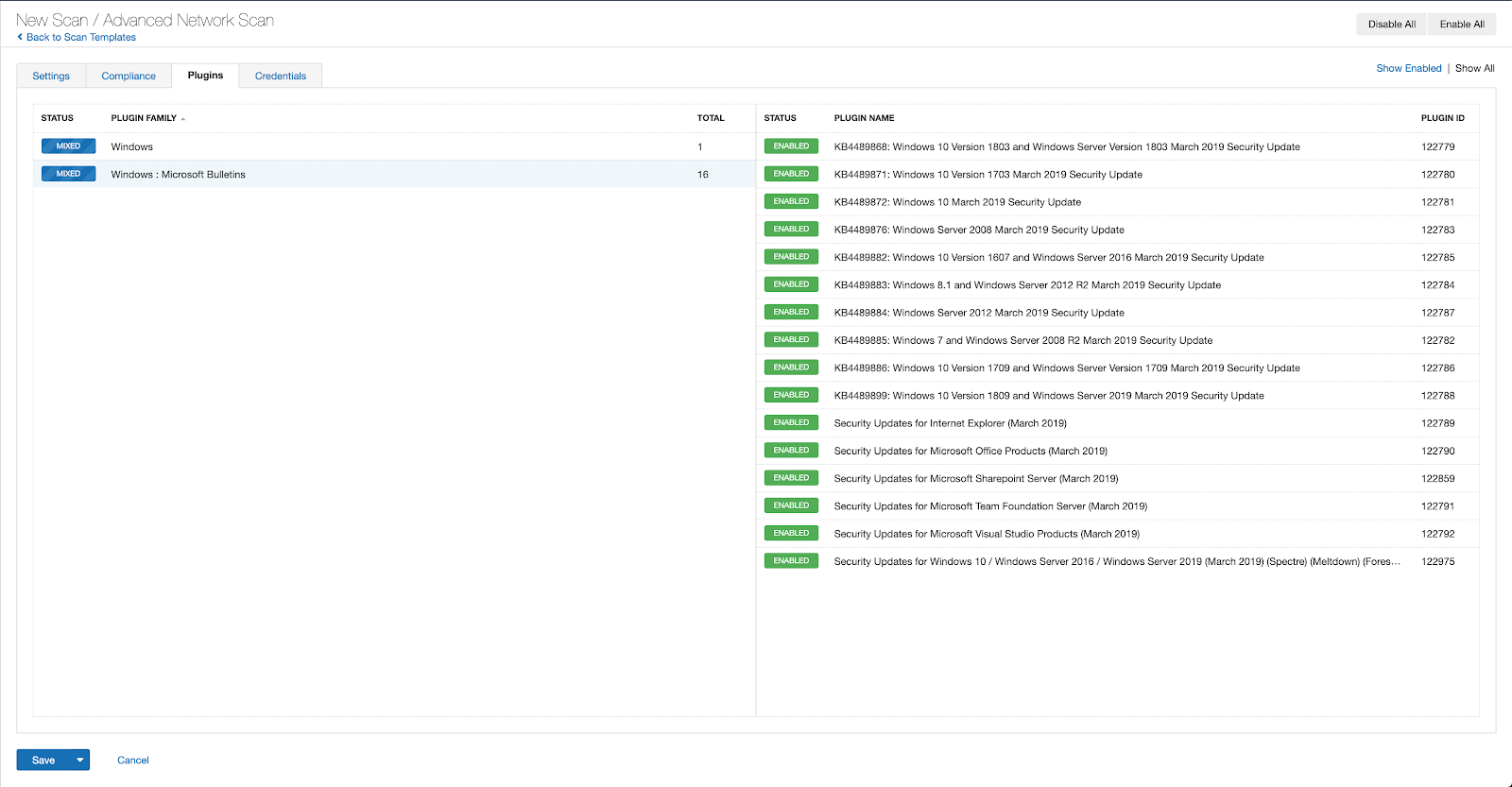
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable Vulnerability Management:
A list of all the plugins released for Tenable’s June 2023 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's June 2023 Security Updates
- Tenable plugins for Microsoft June 2023 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
