There is a lot of noise on cybersecurity for the manufacturing shop floor, but where do you start? Let’s keep it simple and touch on why attackers do what they do, and what you can do to stop them. It’s all about reducing risk, and maximizing your efforts to get the best results. Read on to learn more about the threat landscape and some tactics to manage the threats.
Whatever name we want to put on it, the trend widely called digitization or convergence in IT/OT in manufacturing has its good and bad points. Increased data about quality, efficiency and sustainability makes for faster and more informed decisions. The increased connections and new systems mean traditionally isolated systems are connected. In the rush to connect, we expand the attack surface, resulting in deficient security and safety controls. In this blog post, we look at the true nature of vulnerabilities and their fixes on the shop floor.
Let's take a deep and meaningful look into the threats facing us today:
- Bad guys trying to make money off of you
- Bad guys trying to make money off of someone else by damaging you
Yeah, that’s kinda it. We can slice and dice it many ways but the things we need to do to prevent and/or fix it are the same. It all comes down to a set of impactful defenses we summarize below.
So let us take a deep and meaningful look into the defenses you can put in place:
- You can fix vulnerabilities
- You can chase threats
Yeah, that’s kind of it, but we are going to look at fixing vulnerabilities because that is where money is best spent. Chasing down intrusions and threats sounds glamorous – very James Bond with cool terms we appropriate from the military. The truth of the matter is it is pretty expensive and requires full-time employees (FTEs) dedicated to hunting. What we can also do is look for the effects of attacks and quickly respond. This is resiliency which is much more important in ICS, and much more straightforward in ICS.
So, vulnerability management it is, then. It is a pretty charged topic in the OT world, but bear with me. Fixing vulnerabilities is not just patching. Otherwise, I wouldn’t waste my time or yours.
So, what is a vulnerability?
The National Institute of Standards and Technology (NIST) defines it as: “Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source.”
I bet most of you thought about Windows system patching, maybe CVE or CVSS scores of one flavor or another. I would modify the NIST definition from “information system” to “system.” It would be more inclusive of OT, and really of anything that introduces cyber risk. Doesn’t that make you think of a vulnerability differently? With that context, here are some common vulnerabilities (you could also call them weaknesses if that helps):
- Flaws in software coding (yup, blame the other guy)
- Hardware and software designed without security in mind, such as legacy equipment, which is very common in manufacturing environments.
- Configuration or implementation decisions that ignore security
- Poor process, poor standards
- Inadequate knowledge of system capabilities
My favorite vulnerability falls under the third bullet above; shop floor computers that use a shared username and password. Another example of a configuration weakness is the many devices that have no authentication at all when a method is available.
Notice that only the first one of the categories can be fixed by a “patch”. I’m going to go wide here and clump everything that requires an upgrade “patch.” Disclaimer, depending on the nature of the system requiring a patch, the process can be disruptive to the production process. With that said, Windows hotfixes, upgrades, anything on Patch Tuesday, firmware upgrades on a controller, new versions of software, etc … are in scope. Admittedly a wide net, but we want to take a holistic view. We fear and loathe patching, yell at IT for suggesting them, start bar fights, hold grudges, and argue endlessly at conferences. I digress. Let’s cover the steps in the vulnerability management process:
- Vulnerability identification: Vulnerabilities in a system are detected through vulnerability scanning, penetration testing or code review (or other stuff).
- Vulnerability assessment: Gauging the probability of a vulnerability being exploited by an attacker and determining the impact should the vulnerability be exploited.
- A formally designed program would call this risk quantification.
- Vulnerability resolution: Mitigation or remediation. But what is the difference?
- Remediation– Correct or remove the vulnerability – typically a patch.This is often not possible in all parts of an ICS environment. In controllers, it rarely meaningfully raises your security posture, resulting in the next step.
- Mitigation– Reduce, lessen or decrease the likelihood of a successful attack or lessen the impact of a successful attack. These are often called compensating controls.
How Tenable OT Security helps cybersecurity professionals in the manufacturing industry
Let's look at the vulnerability management process outlined above, through the lens of a security practitioner using Tenable OT Security.
Example 1:
Step 1: Here, we are continuously monitoring and scanning a manufacturing environment with Tenable OT Security. You can see we were able to identify CVE-2020-6998 present on a Rockwell controller. Not only do we identify the vulnerability, but we also get options for remediation. We can follow the links on the screen for instructions and resources. In the image below, we can see the option to upgrade the firmware to version 33.011 or later.

Step 2: Based on what process the controller runs, we may not be able to do anything, or even improve anything. Why did I say remediating the device may not make anything better? Well, even when a provider like Siemens or Rockwell provides an authentication method in a controller, it is rarely used. So, all anyone needs is the coding tool from the manufacturer like Studio 5000 or TIA Portal, to access the device. Even better, a bad guy might just get access to the Windows workstation normally used to program that controller. My point is, exploits for controllers can be a waste of time if there is no authentication.
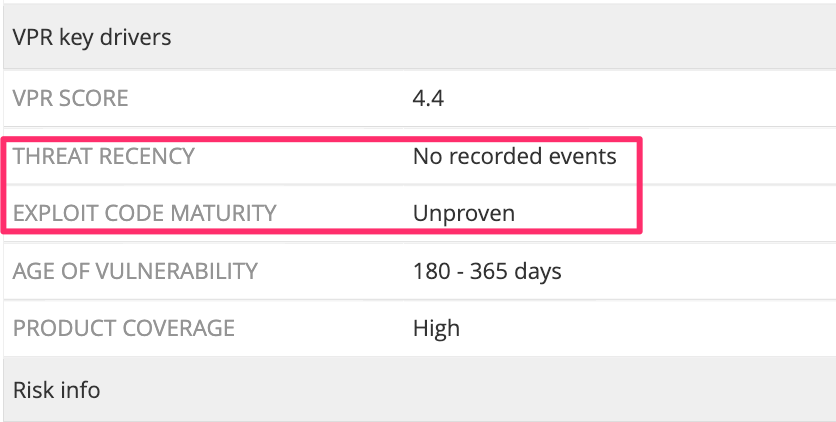
Tenable OT Security leverages Vulnerability Priority Ratings (VPR), helping users understand the exploitability of a vulnerability. The image below shows a summary of our research for this specific vulnerability, saying there aren’t any known exploits in the wild. The VPR score is low, indicating low risk if this vulnerability is present in your environment.
Step 3: Based on the above assessment, the best option might be mitigation. For this one, and many other Rockwell devices, that means blocking traffic on port 44818 from “outside the manufacturing zone.”
Tenable OT Security can build you a visual network map that shows you all of the connections in the ICS network and their IP addresses. In the figure below, we get a clear view of the devices that need connectivity and those that do not, making the most challenging part of writing firewall rules significantly easier.

Using this information, we can take it a step further than blocking traffic on port 44818 by implementing firewalls or other network controls to segment the ICS network. We can limit traffic so only those devices that need to communicate with the controller can.
The conclusion here is that there are many vulnerabilities more important than this one and that many are covered by the application of firewall rules. So there is no reason to go through the arduous task of deciding if you can upgrade the firmware on this controller, which eliminates the need to schedule downtime to patch systems. Less downtime means saving the company money.
Example 2: On to a less contentious set of vulnerabilities and the mitigations that cover a wide range of them. I see these a fair number of times when working with manufacturing clients.
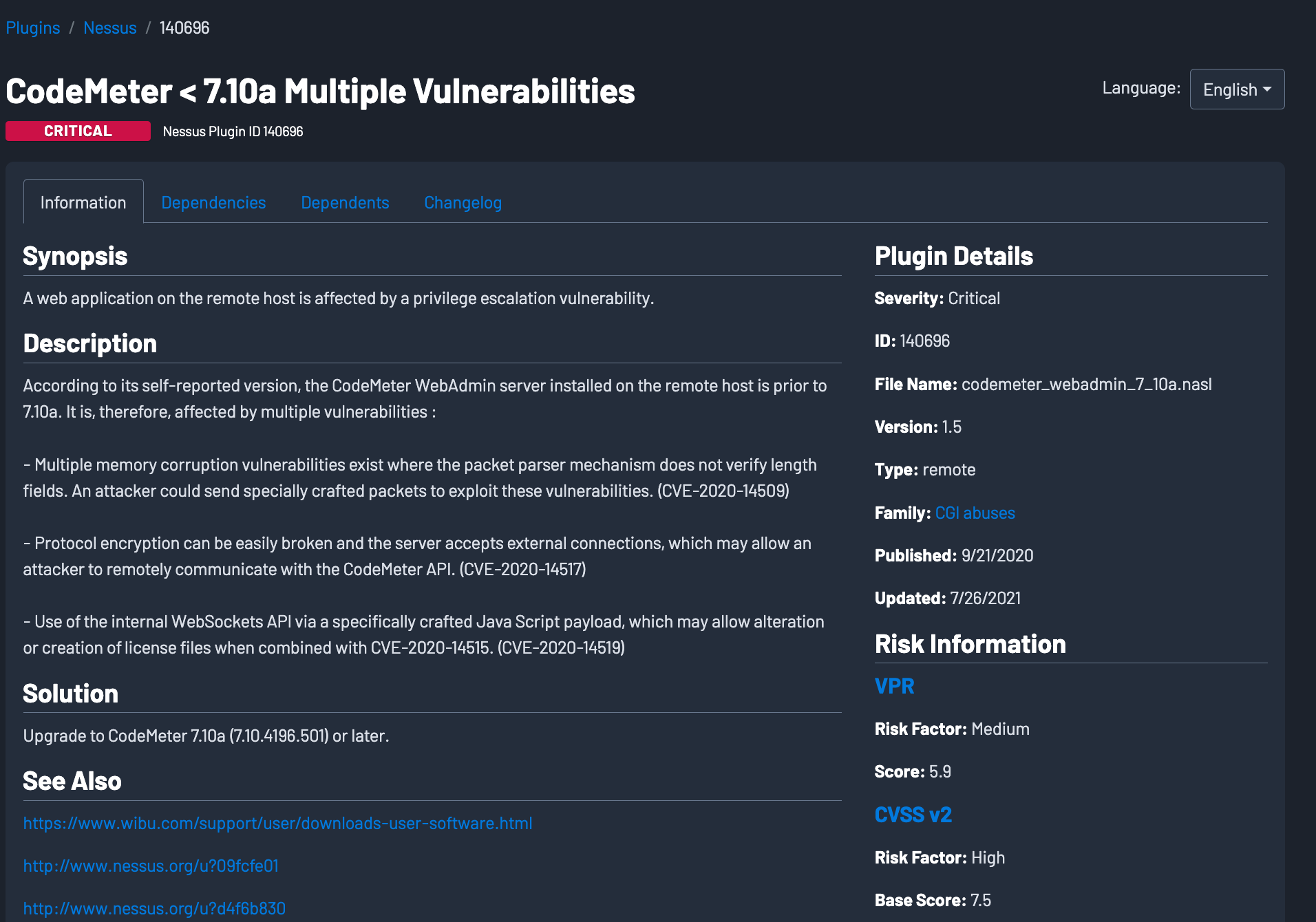
Step 1: Let’s take a look at CVE-2020-16233, a vulnerability running on a Windows machine. Nessus is embedded in Tenable OT Security, which makes light work of identifying vulnerable IT systems. This Windows workstation is running the CodeMeter software license management program.
Step 2: Many manufacturing environments have a sizable inventory of IT devices on the OT network. How we treat controller vulnerabilities and their mitigations is separate and distinct from how we treat workstation vulnerabilities and their remediations.
Step 3: In the image below, you can see the remediation option and additional resources. Because this vulnerability is on a Windows workstation, a software upgrade isn’t likely to cause disruption, though we recommend confirming this assumption before starting the patching process. It’s safe to say IT system patching is typically easier than OT system patching.
Key takeaways for manufacturing industry cybersecurity professionals
1. Threats facing the manufacturing industry are based on two motivations:
- Bad guys trying to make money off of you
- Bad guys trying to make money off of someone else by damaging you
What we do to reduce the likelihood of a successful attack is the same.
2. The defense strategy is simple and consists of two main tactics:
- You can fix vulnerabilities
- You can chase threats
3. Both of the tactics above are important. However, I recommend a proactive approach by fixing vulnerabilities because that is where money is best spent. Resiliency is much more important in ICS. The steps in the vulnerability management process are:
- Vulnerability identification
- Vulnerability assessment
- Vulnerability resolution
- Remediation
- Mitigation
Learn more:
- Tenable OT Security manufacturing web page
- Tenable OT Security manufacturing solution brief: Securing Manufacturing without Risking Productivity
- Tenable OT Security manufacturing white paper: Securing the Manufacturing Shop Floor
