Learn all about the recommendations the NAIAC made to the U.S. government for responsible AI. Plus, employees go gaga over ChatGPT, while cyber teams get tasked with securing it. Also, we look at cloud IAM challenges and how to tackle them. And much more!
Dive into six things that are top of mind for the week ending June 30.
1 – AI advisory group submits annual report to Biden, Congress
Set up federal AI leadership roles. Launch AI research and development initiatives. Provide AI training to civil servants. Boost funding for AI programs.
Those are just a few of the 24 recommendations that the U.S. National Artificial Intelligence Advisory Committee (NAIAC) made in its first annual report to the White House and to Congress.
NAIAC, created in May 2022 and consisting of 26 AI experts, organized the 89-page report under four main themes:
- Leadership in trustworthy AI
- Leadership in research and development
- Support and opportunity for the U.S. workforce
- International collaboration

“This report frames AI as a technology that requires immediate, significant, and sustained government attention. The U.S. government must ensure AI-driven systems are safe and responsible, while also fueling innovation and opportunity at the public and private levels,” the report reads.
To get more details, check out:
2 – Employees: I want my ChatGPT
Organizations, and quite prominently their cybersecurity teams, are scrambling to figure out if and how to use generative AI tools like ChatGPT securely, lawfully and responsibly. And what do employees think? Most are all for the ultra-popular and deeply controversial chatbot.
According to a survey of 9,305 U.S. professionals from job search website Glassdoor, a resounding majority of respondents – 80% – said they oppose bans or restrictions on ChatGPT at their workplace.
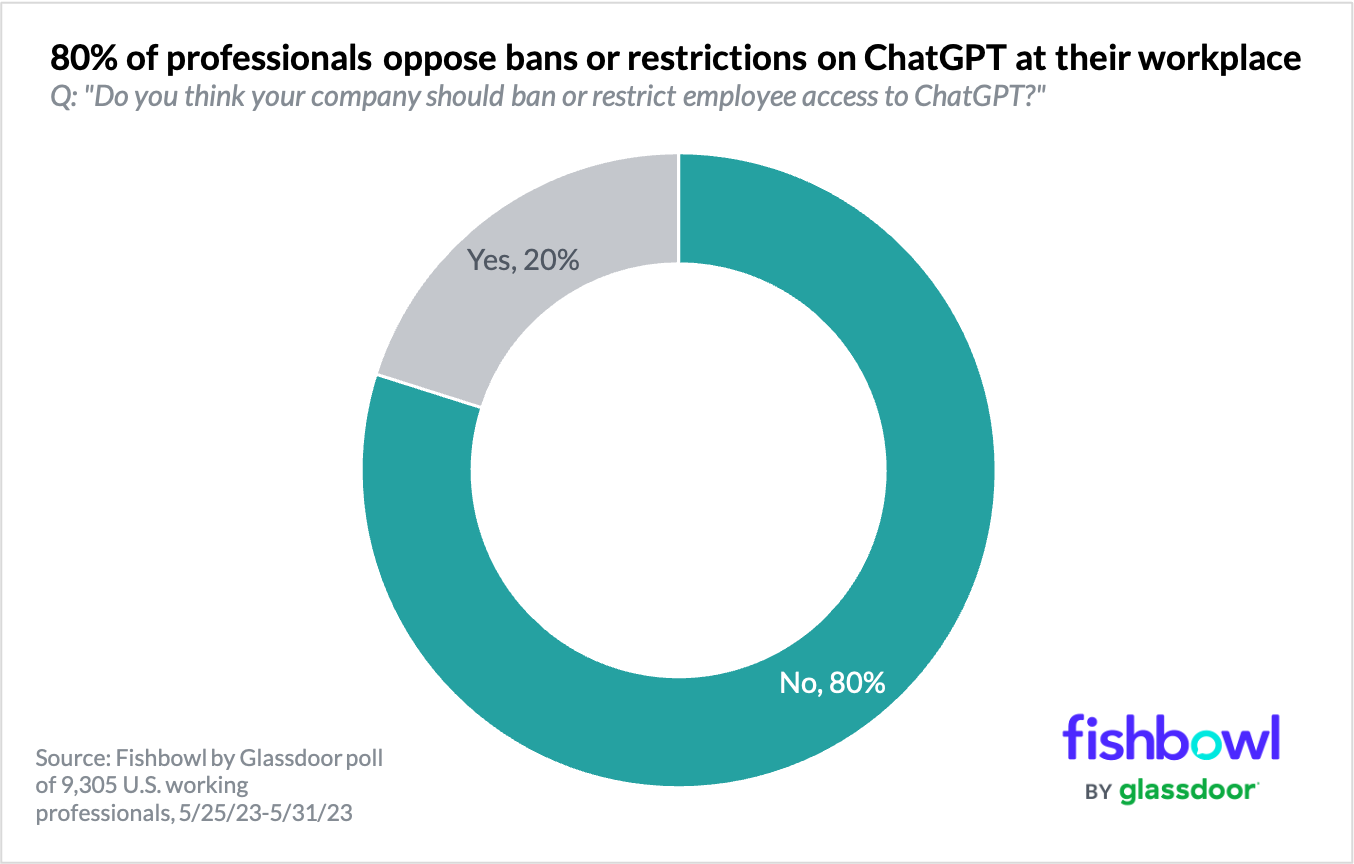
The survey, conducted by Glassdoor’s Fishbowl social networking unit, also found that ChatGPT gets the most love from folks in advertising, marketing, consulting and healthcare. Meanwhile, legal teams are less enthused.
For more information about the secure use of generative AI tools like ChatGPT in the workplace, check out these Tenable blogs:
- “Cloud Security Alliance unpacks ChatGPT for security folks”
- “Building Your Own ChatGPT? Learn How To Avoid Security Risks of AI Models”
- “As ChatGPT Concerns Mount, U.S. Govt Ponders Artificial Intelligence Regulations”
- “How Enterprise Cyber Leaders Can Tame the ChatGPT Beast”
- “A ChatGPT Special Edition About What Matters Most to Cyber Pros”
3 – CISA’s SCuBA project releases cloud app security docs
Cyber teams tasked with protecting cloud apps, listen up: the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released this week two guides from its Secure Cloud Business Applications (SCuBA) project. SCuBA’s goal is to help civilian federal agencies secure their cloud apps and their data via secure configurations – and the advice is also relevant for private-sector companies.

These are the two new documents published by SCuBA:
- Extensible Visibility Reference Framework (eVRF) Guidebook, which explains the eVRF framework and comes with workbooks for the Google Workspace and Microsoft 365 suites
- Technical Reference Architecture (TRA) document, a guide for adopting technology for cloud deployment, secure architecture and zero trust frameworks
“These resources will help organizations address cybersecurity and visibility gaps that have long hampered our collective ability to adequately understand and manage cyber risk,” CISA Executive Assistant for Cybersecurity Eric Goldstein said in a statement.
To get more details, check out:
- CISA’s announcement
- the TRA document
- the eVRF framework
- the SCuBA project’s main page
For more information about cloud app security, check out these Tenable blogs:
- “Organizations struggle with SaaS data protection”
- “Cloud Security Basics: Protecting Your Web Applications”
- “Don’t downplay SaaS security”
- “Revisiting CSA’s top SaaS governance best practices”
VIDEO
Tenable Cloud Security Coffee Break: Web app security
4 – NCC Group: Ransomware attacks spike
Ransomware attack victims ballooned in May, growing by 24% compared with April and by 56% with May 2022, according to data from the NCC Group’s Threat Intelligence team.
The main reason behind the upsurge was the threat activity from 8base, a new ransomware player that uses a double extortion strategy, NCC Group said in its “Monthly Theat Pulse” report for May.

Lockbit 3.0 actors were responsible for the most attacks (18%), although the loosely-coupled group experienced a drop of 27% in attacks compared to April. 8base accounted for 15% of attacks, of which more than half were aimed at companies in the industrial sector.
“We continue to see heightened levels of ransomware activity in 2023, as each passing month surpasses the volume of attacks witnessed during the same period in the previous year,” Matt Hull, Global Head of Threat Intelligence at NCC Group, said in the report.
To get all the details, read the full report.
For more information about ransomware protection:
- “How Can I Protect Against Ransomware?” (CISA)
- “7 Steps to Help Prevent & Limit the Impact of Ransomware” (Center for Internet Security)
- “Ransomware Preparedness: Why Organizations Should Plan for Ransomware Attacks Like Disasters” (Tenable)
- “Tips & Tactics: Ransomware” (NIST)
- “Mitigating malware and ransomware attacks” (U.K. NCSC)
VIDEO
Anatomy of a Threat: MOVEIt (Tenable)
5 – CSA’s top cloud IAM challenges
The Cloud Security Alliance’s Identity and Access Management Working Group has ranked the top 10 challenges in cloud identity and access management. Here’s a quick peek at five of them, along with CSA recommendations.
- Managing identities across multiple cloud environments. The CSA recommends adopting an IAM system that can support multiple cloud environments and provide a single source of truth for identity data.
- Ensuring compliance with regulations and standards. Look for an IAM system capable of enforcing the regulations and standards that impact your IAM strategy, such as GDPR, PCI DSS and HIPAA, the CSA suggests.
- Managing non-human identities. Your IAM system must manage identities not only for your users but also for applications, services and APIs.
- Managing identities for external third parties. Make sure your IAM solution lets you manage identities outside of your organization’s boundaries, such as external users, partners and suppliers who need access to your systems and data.
- Managing identities for IT/OT systems. The IAM system must manage identities for IT/OT systems that are located on-premises but that interface with cloud-based systems.

To get all the details, check out:
- the CSA’s blog “Navigating the Top 10 Challenges in Cloud Identity and Access Management”
- the Identity and Access Management Working Group’s main page
For more information securing IAM in the cloud:
- “Want to get cloud IAM right? Master the fundamentals” (ComputerWeekly)
- “Tool sprawl, technical complexity hamper identity security” (Tenable)
- “Five ways security teams can more effectively manage identities in the cloud” (SC Magazine)
- “How access management helps protect identities in the cloud” (VentureBeat)
6 – U.K.’s cyber agency updates risk management guidance
The U.K. National Cyber Security Centre (NCSC) this week announced its first update to its cyber risk management guidance in five years. So what’s new? Here are some highlights.

- An eight-step cybersecurity risk management framework designed to help organizations understand what’s the best approach to adopt
- A cybersecurity risk management “toolbox” that includes:
- Component-driven and system-driven approaches
- Qualitative and quantitative risk management information
- Threat modeling
- Attack trees
- Cybersecurity scenarios
- A “basic” method for risk assessment and management aimed at newbies to the topic and at organizations with simple needs
To get all the details, read the announcement “New techniques added to the NCSC’s ‘risk management toolbox” and check out the updated framework.
