What's involved in shifting cloud security responsibilities to the app development team with governance by the security team?
With new hacks in the news every day, businesses are rightfully pushing their application development teams to implement security into their daily operations. After all, it's a cybersecurity best practice to integrate security into every step of the development process. But, without any overlying strategy or security governance you end up with a disorganized “cybersecurity potluck.” This manifests itself in too many tools, too many alerts and siloed teams, which, as we know, can invite bad actors to the table.
What is a cybersecurity potluck?
In many organizations security resembles a potluck: Everybody brings something different to contribute and is looking at security from their own silos. Developers might be using an open-source infrastructure as code (IaC) tool, the cloud team might be using a cloud security posture management (CSPM) tool and the operations team might be using a web application scanning tool. These are all in addition to the tools the vulnerability management and traditional infosec teams are using. According to a commissioned study conducted by Forrester Consulting on behalf of Tenable, more than two thirds of organizations have used 10 or more preventive cybersecurity tools in the past 12-24 months1. And it takes a lot of resources to manage all these siloed tools. Nine in 10 (93%) have 10 or more employees devoted to deployment, support, maintenance and/or vendor relationships for the preventive cybersecurity tools in use.
Each tool might be great on its own, but if they don’t integrate with each other you lose the visibility and context you need to do proactive cybersecurity. The disconnects are enough to make your stomach ache.

Source: Tenable, August 2023
All these tools —and the disconnected data they spit out — make informed security decisions messy. Security teams are already saddled with ”alert overload,” data inconsistencies and the financial and resource costs of purchasing and managing disparate tools. As a result, crucial vulnerabilities and misconfigurations may be overlooked in the application development process, exposing your organization to potential cyberthreats. In addition, there is no clear way to communicate risk and security posture to stakeholders who aren’t well-versed in the role-specific jargon.
When security is done in silos, it creates a false sense of safety. It becomes too easy to assume that a problem in one area is constrained to just that area when, in fact, it could have a far-reaching impact across your attack surface. Attackers do not honor your silos. An attacker might enter through a cloud asset or on-prem system and then move laterally to exploit a misconfiguration or CVE in another system — giving them the ability to gain privileged access.
So, while it’s helpful in an organizational sense to have dedicated teams taking ownership of singular aspects of security, without integration amongst the various tools and their findings, as well as governance from the security team throughout the app development lifecycle, it’s virtually impossible to protect the entire attack surface.
It doesn’t have to be this way.
To address the challenge of silos, security teams need to govern the entire application development lifecycle from code to deployment, providing their expertise across teams. Once they’ve designed an application development governance program, security teams then need a unified platform that acts as the single source of truth for their entire security program.
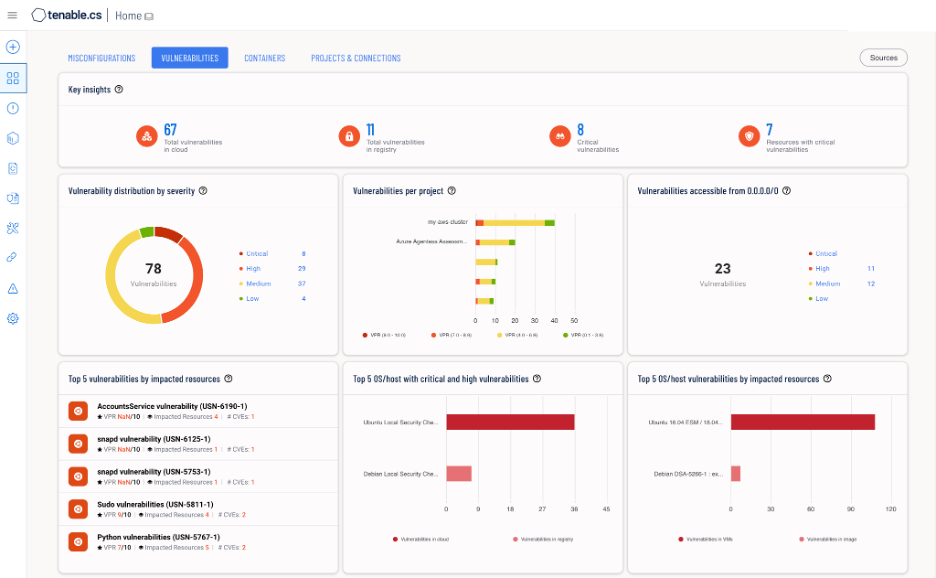
Figure 1: The Tenable Cloud Security dashboard, showing vulnerabilities across public cloud, runtimes and container images.
Source: Tenable, August 2023
Let’s dive into what this type of approach could look like and dig into some best practices.
The main dish: A single policy framework governed by security teams
The first step to avoid a security potluck is to employ a single policy framework everyone involved in the application development lifecycle can follow and adhere to. The policies need to be defined and enforced by the security team. A single policy framework ensures consistency in how cybersecurity is implemented throughout an organization. It establishes a standardized set of compliance guidelines that are followed throughout the development lifecycle.
What does a single policy framework look like in practice? Infrastructure is scanned against defined policies and then remediated in a scalable and repeatable way — regardless of where in the environment the security policy failed. For example, the same policies applied to test infrastructure as code (IaC) and evaluate container images should also be used to evaluate Kubernetes clusters. Policies should not change from build to deployment in cloud environments. In addition to enforcing and defining policies, security teams need to prescribe remediation actions when flaws or misconfigurations are discovered.
A single policy framework ensures consistency across silos, so that security measures are applied uniformly across different systems, departments and locations. It also cuts down on alert overload and improves efficiency by removing potential areas where labor is duplicated.
Chewing on the challenges
Implementing security governance across the application development lifecycle sounds easy in theory. In practice, there are a variety of challenges. For example, security teams might need to learn new domains and tooling or they might feel like they don’t have the control or resources to effectively manage DevOps pipelines.
However, good security tools can help security teams to govern development cycles without adding additional toil. Security tools need to be usable by a variety of teams and centralize information in a way anyone involved can understand. Tenable Cloud Security caters to both DevOps and security teams with specialized features and integrations with trusted tools, so existing workflows don’t have to be blown up in order to implement security
An example for security teams is Tenable’s no-code policy editor. This feature offers a straightforward interface and a low-code approach, enabling security pros to easily define policies against specific vulnerability attributes and container image attributes. They can use predefined policies from the Tenable policy portal, which is backed by the world-class Tenable Research team.
No side dishes required
To further address possible challenges, you might be wondering how security pros are expected to get DevOps teams to buy into a single policy framework approach for security governance throughout the application development process. In fact, the Forrester study shows that 43% of the 825 IT and security leaders surveyed say the DevOps team does not prioritize security in its code development process. So, how can you rely on DevOps teams to actively implement these security measures and ensure you have visibility into them? Wouldn’t they need to use a different security tool for their workflows?
Tenable Cloud Security can help security professionals address the challenges of multiple tools and silos. Not only are security policies easy for security pros to define, they are also easy to enforce by integrating directly into DevOps tooling. Tenable Cloud Security can integrate directly into your CI/CD pipelines, so security is embedded into the build process, not as an afterthought. Tenable Cloud Security helps provide developer guardrails that stop risky deployments before they happen and ensure everything developers put into production has met the policy requirements approved by the security team. There’s no need to blow up existing workflows. Tenable Cloud Security integrates with the tools that DevOps teams already know and trust, such as the Open Policy Agent (OPA), integrated development environments like Visual Studio Code and Git repositories.
Serving up visibility
Securing cloud infrastructure and build environments should be a responsibility on everyone’s plate, but it falls to security teams to lead the way and gain visibility into overall security posture so they can effectively prioritize remediation in the application development lifecycle. Getting visibility that’s consolidated, customizable and easy to understand saves time, makes you more secure, and enables you to better reconcile data that can be shared or used into boardroom presentations. With Tenable Cloud Security, security pros can focus on doing what they do best: securing the infrastructure.
1A commissioned study of 825 IT and security professionals conducted by Forrester Consulting on behalf of Tenable, May 2023.
Learn more
- Download the Container Security Solution Brief
- Read the Policy as Code eBook
- View the Container Security Solution Page
- Attend a Cloud Security Coffee Break
