Check out the new ransomware trends documented by DHS, as well as a joint CISA-FBI alert about the Snatch ransomware. Plus, find out what CISA has in store for its Known Exploited Vulnerabilities catalog. Furthermore, don’t miss new source-code management tips from the OpenSSF. And much more!
Dive into six things that are top of mind for the week ending September 22.
1 - DHS shines light on ransomware trends
It looks like 2023 is shaping up to be a banner year for ransomware gangs.
During the first half of this year, ransomware actors have extorted at least $449 million globally, and are on track to have their second most profitable year yet. So says the U.S. Department of Homeland Security in its “Homeland Threat Assessment 2024” report.
“Ransomware actors continue to target a variety of victims, almost certainly reflecting malicious cyber actors’ target refinement to entities perceived as the most vulnerable or likely to pay a ransom,” reads the 38-page report.

Other ransomware insights from the report include:
- The number of ransomware attacks in the U.S. grew by 47% between January 2020 and December 2022
- The average ransomware-recovery period for a business is 22 days, a disruption that often costs 50 times more than the ransom
The report also highlights new and refined tactics employed by ransomware groups, such as:
- An increase in double extortion attacks
- The use of distributed denial of service (DDoS) attacks
- Harassment of a victim’s customers to further pressure the victim to pay the ransom
- The use of intermittent encryption, in which files are only partially locked down, in order to operate faster
- An improved ability to adapt and customize their attacks
For more information about recent ransomware incidents and trends, check out these Tenable resources:
- “CVE-2023-20269: Zero-Day Vulnerability in Cisco Adaptive Security Appliance and Firepower Threat Defense Reportedly Exploited by Ransomware Groups” (blog)
- “FAQ for MOVEit Transfer Vulnerabilities and CL0P Ransomware Gang” (blog)
- “FBI and CISA Release Cybersecurity Advisory on Royal Ransomware Group” (blog)
- “The Ransomware Ecosystem” (report)
- “Tenable’s Ransomware Ecosystem Report” (on-demand webinar)
2 - Insurer: Ransomware causes jump in cyber insurance claims
And speaking of ransomware, it’s being identified as the main driving force behind a recent spike in cyber insurance claims.
Insurance provider Coalition said in its “2023 Cyber Claims Report: Mid-year Update” that cyber claims rose 12% in the first half of 2023 compared with the second half of 2022, a surge driven primarily by ransomware attacks.
Ransomware claims increased 27% in the first six months of this year, while the average ransom demand grew 47% to $1.62 million.
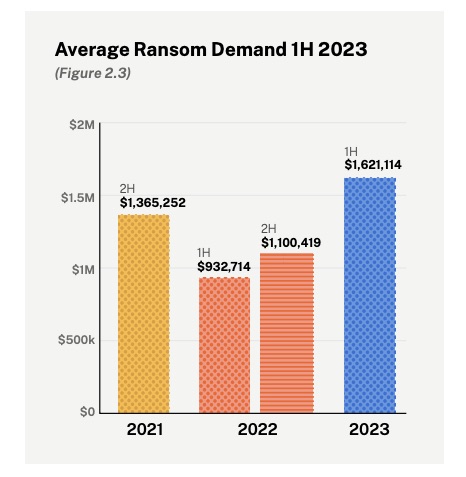
(Source: Coalition’s “2023 Cyber Claims Report: Mid-year Update,” September 2023)
The severity of ransomware claims hit a record in the first half of 2023 with an average loss amount of more than $365,000. Overall, ransomware claims accounted for 19% of all reported claims during the period.
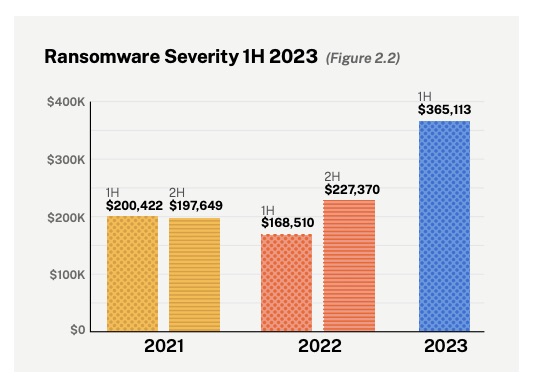
(Source: Coalition’s “2023 Cyber Claims Report: Mid-year Update,” September 2023)
To get more details, read the report’s announcement and the full report.
3 - Critical infrastructure orgs warned about Snatch ransomware
And staying with the ransomware topic, the FBI and CISA are urging cybersecurity teams to prepare to fend off attacks from ransomware group Snatch, which targets critical infrastructure organizations in sectors including defense, agriculture and information technology.
The joint advisory “#StopRansomware: Snatch Ransomware,” published this week, details tactics, techniques and procedures, as well as indicators of compromise associated with this ransomware variant.
“After data exfiltration often involving direct communications with victims demanding ransom, Snatch threat actors may threaten victims with double extortion, where the victims’ data will be posted on Snatch’s extortion blog if the ransom goes unpaid,” the document reads.

Snatch, which appeared in 2018 and was originally known as Team Truniger, uses a ransomware-as-a-service (RaaS) model to operate, and employs a variety of frequently changing methods to breach systems and establish network persistence, the agencies said.
For more information about the Snatch ransomware:
- “What banks need to know about Snatch ransomware” (American Banker)
- “Feds issue Snatch ransomware warning as gang claims latest victim” (SC Magazine)
- “Snatch gang ‘consistently evolved’ in targeting multiple industries” (The Record)
- “Ransomware gang Snatch claims attack on Briars Group and two other organisations” (TechMonitor)
- “Ransomware group takes credit for February attack on city of Modesto” (The Record)
4 - CISA’s KEV catalog of exploited bugs hits 1,000
A catalog of vulnerabilities exploited in the wild that CISA began compiling almost two years ago recently reached 1,000 items, prompting the agency to look back on the project – and to look forward at what’s to come.
CISA launched the Known Exploited Vulnerabilities (KEV) catalog in November 2021, in order to highlight an important criteria to consider when prioritizing which bugs to fix first: whether a vulnerability has been exploited in the wild.
“The purpose of the KEV is simple: while focusing on vulnerabilities that have been exploited isn’t sufficient, it’s absolutely necessary – so let’s start there,” reads CISA’s blog about the KEV milestone.

However, now that the KEV catalog has more than 1,000 vulnerabilities – specifically 1,008 at the time of this writing – the question of how to prioritize this catalog is starting to pop up. Hint: context is everything.
“The answer is nuanced but essential: the importance of a given vulnerability isn’t constant, but is highly dependent on how the vulnerable product is being used in a specific instance,” the blog reads.
(Tenable addressed this question with recommendations tailored for Tenable customers right after the KEV catalog’s launch in a blog titled “CISA Directive 22-01: How Tenable Can Help You Find and Fix Known Exploited Vulnerabilities.”)
To include a vulnerability in the KEV catalog, CISA must first confirm beyond doubt that it was exploited in the wild and that an effective mitigation exists for it. The bug must also have a Common Vulnerabilities and Exposures (CVE) ID.
Federal civilian executive branch agencies are required to remediate internet-facing KEVs within 15 days and all other KEVs within 25 days. Since November 2021, these agencies have collectively remediated more than 12 million KEV vulnerabilities, including 7 million this year.
So what future plans does CISA have for the KEV catalog? Here are a couple:
- Continue to incorporate it into vulnerability management tools so that the data is easily accessible to VM teams. CISA mentions Tenable as one of its commercial partners that has integrated the KEV catalog into their products.
- Include a wider variety of information about each vulnerability in order to provide richer context about it. For example, CISA may add a field for KEVs being used by ransomware actors.
For more information about prioritizing vulnerability remediation, check out these Tenable blogs:
- “You Can't Fix Everything: How to Take a Risk-Informed Approach to Vulnerability Remediation”
- “CVSSv4 is Coming: What Security Pros Need To Know”
- “Mind the Gap: How Waiting for NVD Puts Your Organization at Risk”
- “What Is VPR and How Is It Different from CVSS?”
- “Tenable 2022 Threat Landscape Report: Reduce Your Exposure by Tackling Known Vulnerabilities”
- “AA23-215A: 2022's Top Routinely Exploited Vulnerabilities”
5 - OpenSSF releases source code management guidance
The Open Source Security Foundation (OpenSSF) has published the “Source Code Management (SCM) Best Practices Guide,” which is intended as a repository of SCM security policies and guidelines.

The guide, which covers practices including user authentication, access control and change management, is aimed at developers and security operations teams that want to boost the security of their source code projects on SCM platforms.
“This guide is a comprehensive resource dedicated to raising awareness and education for securing and implementing best practices for SCM platforms,” reads an OpenSSF blog.
Recommendations include:
- CI/CD hardening policies, such as establishing who can trigger a pipeline
- Branch protection policies, such as code-review requirements
- Access controls and permissions, such as setting specific roles for users and groups, and granting access on the principle of least privilege
For more information about securing open source software projects:
- “The Rising Threat of Software Supply Chain Attacks: Managing Dependencies of Open Source projects” (The Linux Foundation)
- “Microsoft worker accidentally exposes 38TB of sensitive data in GitHub blunder” (The Register)
- “Solving open-source security — from Alpha to Omega” (SC Magazine)
- “Insecure open source components create supply chain risks” (Tenable)
- “Software Supply Chain Best Practices” (Cloud Native Computing Foundation)
6 - Report: Security of cell IoT modules must improve
Most cellular internet-of-things (IoT) modules shipped globally in the second quarter had no dedicated hardware security, and almost a third had no security features at all.
Given this reality, makers of these IoT modules should ramp up their adoption of dedicated hardware security, and buyers should choose IoT products with this security feature.
That’s according to IoT Analytics’ “Global Cellular IoT Module and Chipset Market Tracker & Forecast Q2 2023” report, which tracks revenue and shipments from vendors of IoT modules and chipsets for cellular IoT deployment.
Specifically, the report found that only 34% of cellular IoT modules shipped in Q2 had dedicated hardware security. Meanwhile, 37% had non-dedicated hardware security, and the rest – 29% – had no security features at all.
“With a hardware-based root of trust, manufacturers and consumers can ensure the authenticity of the modules—helping to address cloning and counterfeiting—and protection of the device’s keys,” reads an IoT Analytics statement about the report.
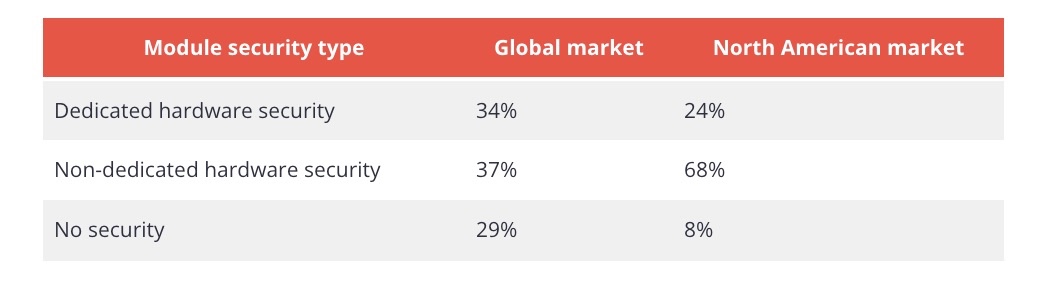
(Source: IoT Analytics’ “Global Cellular IoT Module and Chipset Market Tracker & Forecast Q2 2023”, September 2023)
For more information about the security of cellular IoT components:
- “Flaws in industrial wireless IoT solutions can give attackers deep access into OT networks” (CSO Online)
- “Tips on securing IoT devices gleaned from enterprises that use them” (Network World)
- “US FCC chair says China’s IoT cellular components makers Quectel, Fibocom may pose national security risks” (South China Morning Post)
- “Lawmakers press FCC for action on Chinese-made cellular modules” (The Record)
