Unpatched Apache Airflow instances used in Amazon Web Services (AWS) and Google Cloud Platform (GCP) allow an exploitable stored XSS through the task instance details page.
Managed services for Apache Airflow in AWS (Amazon Managed Workflows for Apache Airflow) and GCP (Google Cloud Composer) provide scalable and secure orchestration of data workflows using Apache Airflow — an open-source platform to programmatically author, schedule and monitor workflows.
The Ermetic research team, now part of Tenable Research, had discovered that AWS and Google Composer managed Apache Airflow services were vulnerable to CVE-2023-29247 (Stored XSS). This vulnerability was previously reported and fixed by Apache; more information can be found here. However, the managed services provided by AWS and GCP were utilizing an outdated, unpatched version.
The research team confirmed the ApatchMe vulnerability by building a custom PoC and subsequently reported the vulnerability to AWS and GCP. In response, AWS now offers a new, non-vulnerable version of Apache Airflow and, for the unpatched versions, has added a CSP (Content Security Policy) as a guardrail. GCP is working on releasing a new, non-vulnerable version. We thank AWS and GCP for their cooperation and quick response.
Microsoft Azure also uses vulnerable managed Apache Airflow instances in its Data Factory service. While the specific version Azure uses was found to be vulnerable, we deemed it to be non-exploitable.
When creating a new environment while using the managed service for Apache Airflow in AWS or Google Composer, users can choose from a number of images containing different Apache Airflow versions. Each Apache Airflow instance is attached to a managed web panel that authenticates its users and grants them session cookies to perform sensitive authenticated operations. The web panel image versions offered by these two cloud providers were all vulnerable to CVE-2023-29247.
Current users of vulnerable services may still be running unpatched instances of Apache Airflow. Organizations should patch their instances as soon as possible by deploying an updated Apache Airflow image version.
How common is Apache Airflow?
Apache Airflow is one of the most popular orchestration tools, with 12 million downloads per month. As for managed services for Apache Airflow: a sampling from our research showed them to be in use by 20% of our customers.
Attack scenario
Authenticated threat actors can use ApatchMe to store their JavaScript payload in the victim's managed Apache Airflow and run JavaScript on behalf of the victim (who can be an admin or other user with more permissions than the threat actor, leading to privilege escalation). With JavaScript, threat actors can run any operation in the session that the victim could — edit tasks, read jobs, job runs, read plugins and configurations, list connections, add variables and more.
Reproduction process
No publicly available reproduction or PoC for the CVE exists so we reproduced it to achieve a stored XSS on a managed Apache Airflow web panel. We hooked a CSS animation to force the XSS to run automatically when a victim's page is visited.
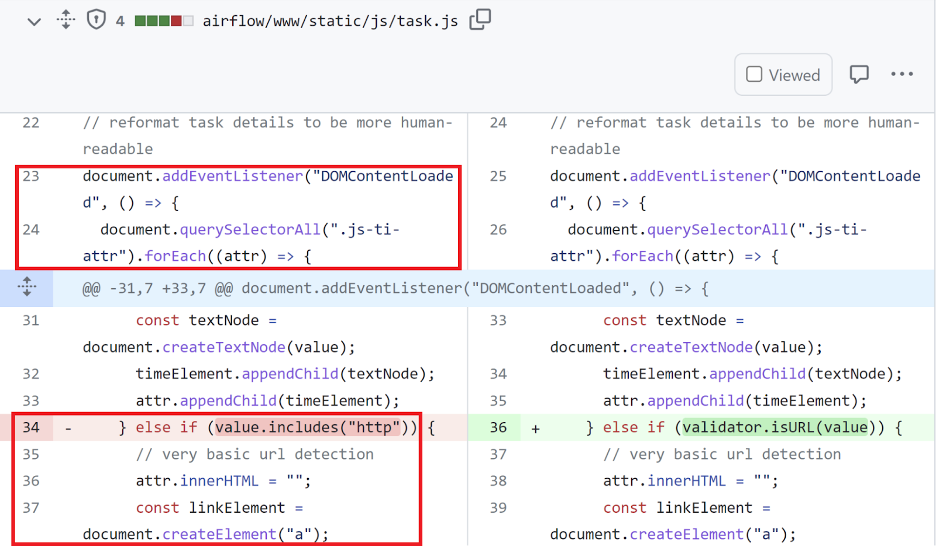
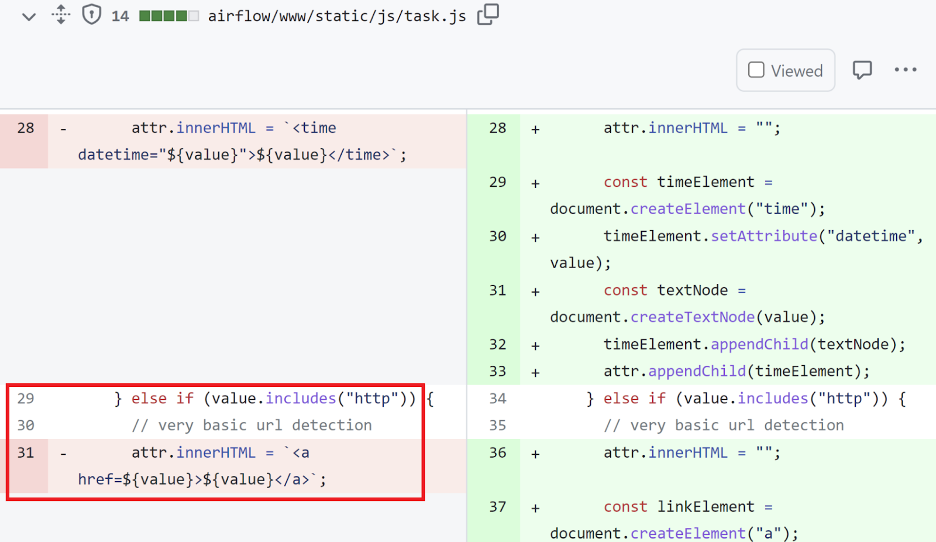
First, we noticed that all managed Apache Airflow image versions that cloud providers AWS, Azure and GCP were deploying were vulnerable. Since Apache Airflow is an open-source project, we can view the patch in github to find our starting point.
The following patches took place on April 7, 2023:
Source: github
Source: github
Our main conclusions from analyzing the above code patches are:
- The vulnerable code references only elements with the “js-ti-attr” attribute; through the task instance edit page, we have control over some of these elements.
- Although a check is conducted for a URL or date input, the URL check is flawed because the "http" string uses "contains". This enables the check to be bypassed easily and does not really check for a properly constructed URL.
- The vulnerable code uses the innerHtml property that parses HTML tags; this property (as opposed to innerText and other alternatives) is known to be vulnerable to XSS when populated with malicious user input.
- The fix involves using a dedicated library for the URL validation and not using the vulnerable and dangerous innerHtml property
We can abuse the flawed URL validation by inputting "http" anywhere we want in the payload.
Then our payload is inputted to a sink — an innerHtml property that is vulnerable to XSS. When injecting different payloads, we noticed we could not close the HTML ‘a’ tag to open a new one, because the server encodes the closing and opening tag characters (greater than (>) and less than (<)) before returning them to the innerHtml property.
Our only option is to inject into the href or close the attribute, and then inject more attributes into the ‘a’ tag.
In our first step to exploit the XSS, we can inject
javascript:alert('has-to-include-http')for a PoC. However, doing so requires a click on the payload, and it does not suffice for us.
After searching for more vectors to run the XSS automatically on a page visit, we inspected the CSS of the page and noticed that it uses animations. One of the events we can use to abuse the ‘a’ tag is the "onanimationend" that will (apparently) execute automatically on the animation end.
We can now target the animation fa-spin we found by inspecting the CSS of the page and inject the following:
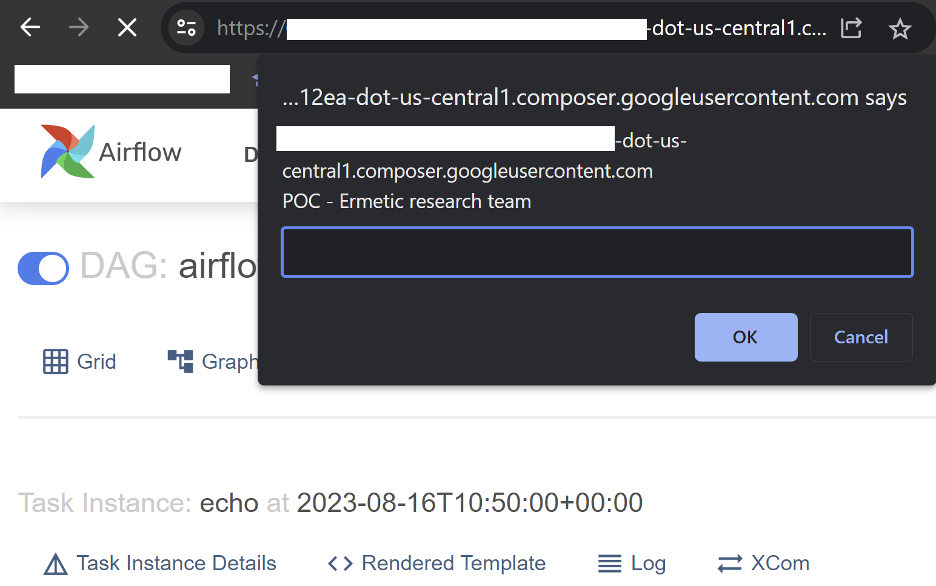
pochttp" style="animation-name:fa-spin"onanimationend="prompt(document.domain)"
With this payload, the XSS runs automatically on a page visit:
Source: Tenable, November 2023
Remediation
As mentioned, AWS released a new version of its Managed Workflows for Apache Airflow (MWAA) and, for the unpatched versions, added a CSP (Content Security Policy) as a guardrail. MWAA users can perform an environment update through the AWS Console by selecting the affected environment and then selecting Edit->Next->Next->Save to ensure that their current Airflow version has the latest security fixes. GCP is working on releasing a new, updated version. However, the vulnerable image versions are still available, making all instances deployed prior to the patch still vulnerable.
Users should take steps to update their Apache Airflow instances and choose the updated version when creating a new one.
Conclusion
Organizations should take action regarding already deployed Apache Airflow instances in their AWS or GCP managed services as they may be operating on outdated images (Azure-managed Apache Airflow instances are also prone but the vulnerability is not exploitable). It's crucial that you review and identify any such vulnerable deployments as the instances can remain susceptible if not updated.
We commend the prompt action of the cloud service providers in releasing updated image versions of Apache Airflow. Users can now avail themselves of these new images to protect their organizations from the ApatchMe vulnerability. For those managing existing instances, your immediate action should be to update or migrate to the patched versions.
Tenable is here to help
Feel free to contact us on X (formerly Twitter) with any questions or concerns you have about cloud security:
@terminatorLM
@IgalGofman
@NoamDahan
@arieitan
