As we bid adieu to 2023, we highlight major trends that impacted cybersecurity professionals in the past 12 months. Learn how the cyber world changed in areas including artificial intelligence, CNAPP, IAM security, government oversight and OT security.
1 - Excitement over GenAI for cyber defense
Artificial intelligence, and generative AI (GenAI) specifically, captured the world’s imagination in 2023, as we all marveled at the technology’s potential for good and evil. Cybersecurity teams were no exception.
Yes, cyberattackers quickly leveraged GenAI for malicious purposes, such as to craft better phishing messages, build smarter malware and quickly create and spread misinformation.
But cyber defenders also saw this powerful technology begin to find its way into their tool boxes – boosting a broad swath of cyber capabilities, including vulnerability detection, identity and access management (IAM), incident response, malware analysis and security operations.
In short, the optimism over AI’s promise for cyber defense was palpable this year.
Among 3,800 senior executives surveyed for PwC’s “2024 Global Digital Trust Insights” report, 69% said their organizations plan to use GenAI for cyber defense in the next 12 months, while 47% already use it for cyber risk detection and mitigation.
The “State of Cybersecurity 2024” report from the Computing Technology Industry Association (CompTIA), which polled 511 U.S. business and IT pros involved in cybersecurity, shows how respondents foresee using AI.
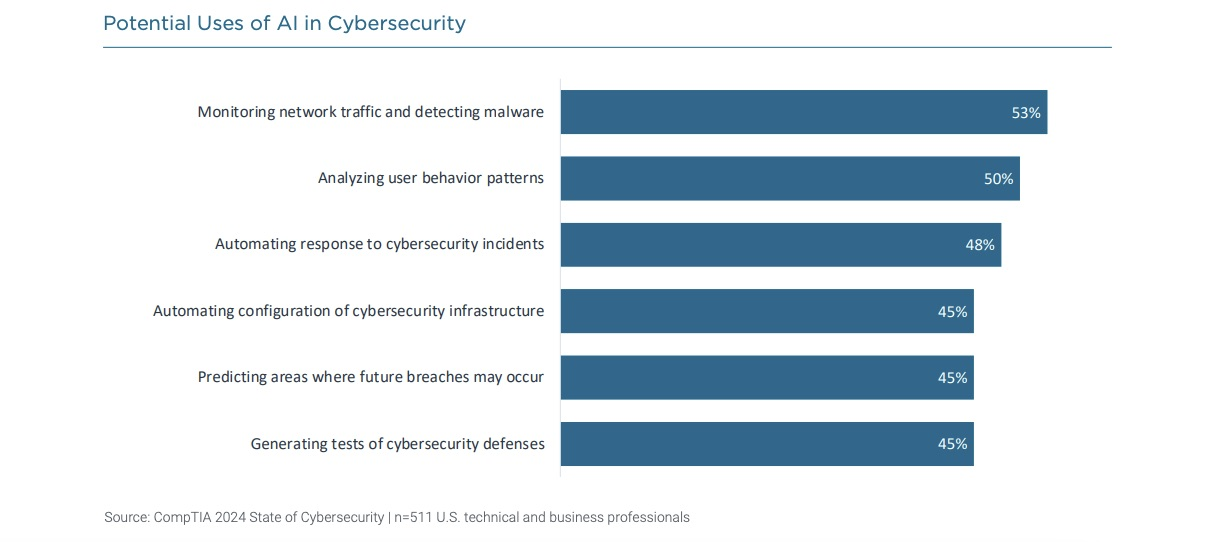
Tenable, whose products have had AI technology for years, was very much at the center of this trend, as it integrated GenAI capabilities across the Tenable One Exposure Management Platform in 2023.
“AI has the potential to change how cybersecurity professionals search for patterns, how they explain what they’re finding in the simplest language possible, and how they decide what actions to take to reduce cyber risk,” former Tenable CPO Nico Popp wrote in the blog “AI Is About To Take Cybersecurity By Storm”.
For more information about using AI for cybersecurity, check out these Tenable resources:
- “How Generative AI Is Changing Security Research” (report)
- “GenAI Drives Broader Use of Artificial Intelligence Tech for Cyber” (blog)
VIDEOS
Tenable CEO Amit Yoran discusses AI and preventive security on CNBC
How Generative AI is Changing Security Research: The Development of the G-3PO Tool
Making Decisions Easier with AI
2 - And an AI challenge: Using it safely and responsibly
Here’s another way in which AI impacted cyber teams in 2023: As organizations rushed to adopt AI to boost business operations, cyber teams – along with others like IT, GRC and legal – got tasked with ensuring AI use is secure, compliant and responsible.
No small task. Global AI regulations are in flux, and organizations are scrambling to adopt usage policies. This year, we saw high-profile incidents in which employees inadvertently entered confidential corporate information into ChatGPT.
McKinsey & Co.’s “The state of AI in 2023: Generative AI’s breakout year” surveyed 1,684 organizations, of which 913 are using AI in at least one business function. Among those, 548 are using GenAI.
The study found only 21% have GenAI usage policies; only 38% are actively mitigating its cybersecurity risks; and 28% are mitigating its compliance risks.
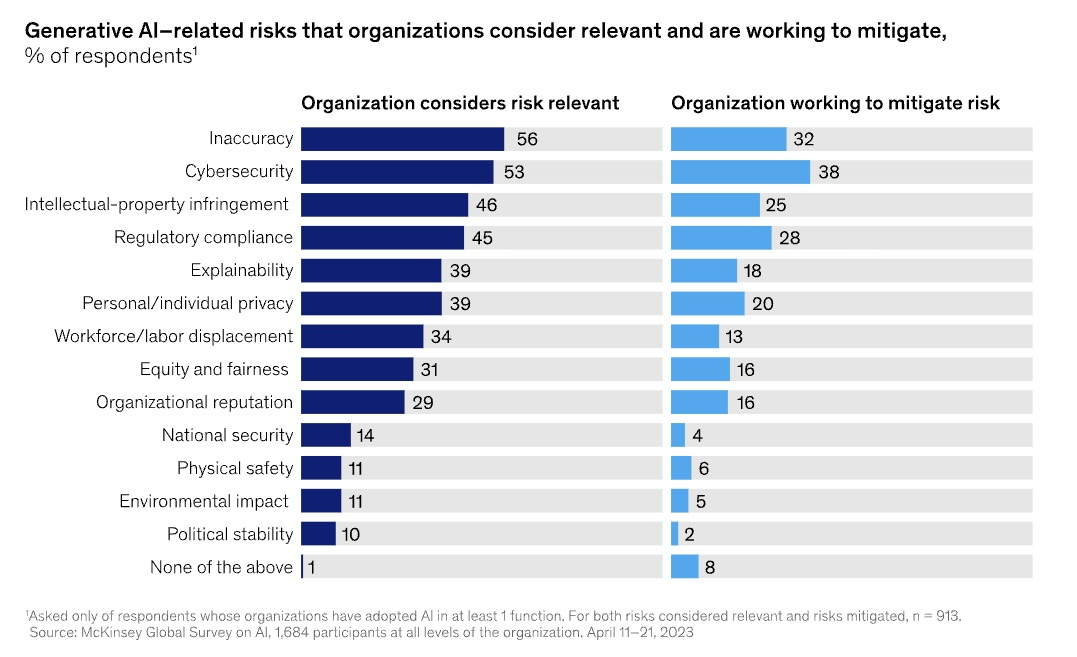
Of particular interest to cyber teams is the issue of protecting enterprise AI systems from cyberattacks, the topic of the Stanford University and Georgetown University report “Adversarial Machine Learning and Cybersecurity: Risks, Challenges, and Legal Implications.”
Here’s a small sampling of advice and recommendations issued in 2023:
- ISACA’s “Considerations for Implementing a Generative Artificial Intelligence Policy”
- McKinsey & Co.’s “What every CEO should know about generative AI”
- OWASP’s “Top 10 Critical Vulnerabilities for Large Language Model Applications”
- Team8’s “A CISOs Guide: Generative AI and ChatGPT Enterprise Risks”
- “Guidelines for secure AI system development” from the U.S. and U.K. governments
- The Cloud Security Alliance’s “Security Implications of ChatGPT”
3 - CNAPP takes center stage in cloud security
In the vast cloud security landscape, one development stands out: The accelerated adoption of cloud native application protection platforms (CNAPPs), as cybersecurity teams grapple with growing multi-cloud complexity.
Here are some telling data points from the Cloud Security Alliance’s “Cloud Native Application Protection Platform Survey Report,” which was released in August and polled 1,200 IT and security pros:
- 85% of organizations have either implemented or plan to implement CNAPPs in their cloud environments, a trend driven in part by multi-cloud use
- Fewer than 30% of organizations have integrated CSPM, CWP and CIEM across multi-cloud environments
- Asked to name CNAPP’s core value proposition, respondents’ top choices were:
- comprehensive visibility over security posture (25%)
- data posture understanding and data protection (16%)
- multi-cloud threat protection (13%)
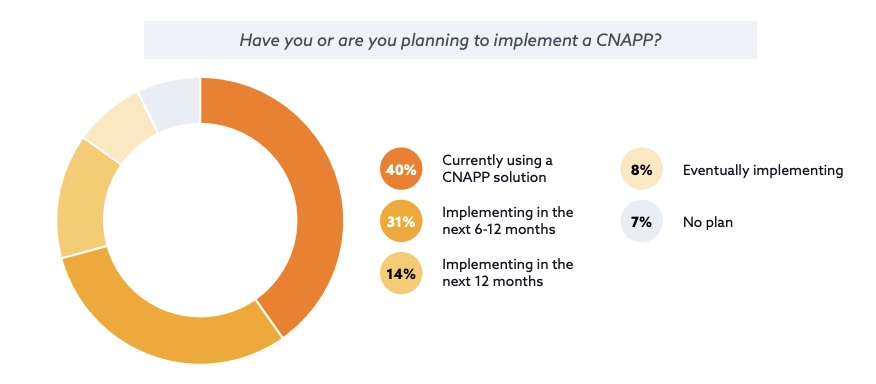
(Source: Cloud Security Alliance’s “Cloud Native Application Protection Platform Survey Report, August 2023)
To learn more about cloud security and CNAPP, check out these resources from Tenable:
- “Decrypting CNAPP: Moving Beyond the Acronyms and Analyst Jargon to a Unified Approach to Cloud Security” (blog)
- “Navigating Cloud Security Challenges: Key Concerns for Cybersecurity Professionals” (blog)
- “Five Core Principles for Hybrid Cloud Security” (blog)
- “A Cloud Security Master Class” (on-demand webinar)
- “Holistic Security for AWS, Azure and GCP: Comprehensive Cloud-Native Application Protection for Multi-Cloud Environments” (white paper)
VIDEO
What is a Cloud-Native Application Protection Platform?
4 - Cloud adoption further complicates IAM security
Securing identity and access management (IAM) systems, a perennial challenge, remained complex in 2023, largely due to cloud adoption growth.
Here’s a telling stat: Roughly between mid-2022 and mid-2023, 90% of organizations suffered at least one identity breach. That’s according to the Identity Defined Security Alliance’s “2023 Trends in Identity Security” report, which surveyed 529 respondents in charge of IT security or identities.
Why the difficulty in protecting digital identities? Reasons respondents gave included:
- A rise in identities driven primarily by adoption of cloud apps
- Roadblocks caused by complicated identity frameworks and by complex technical environments
Meanwhile, the U.S. Cyber Safety Review Board (CSRB) spotlighted IAM security in its August report of the Lapsus$ cyber extortion group. “IAM weaknesses were a consistent theme in attacks across all targeted entities and present opportunities to make ongoing improvements,” reads the report.
Recently, Tenable CTO Glen Pendley stressed the importance of securing cloud identities in his Dark Reading article “Securing Cloud Identities to Protect Assets and Minimize Risk.”
“Most attacks we see today are client-side attacks, in which attackers compromise someone's account and use their privileges to move laterally and access sensitive data and resources. To prevent this, you need visibility into your cloud's identity infrastructure,” he wrote.
For guidance for beefing up IAM security, check out:
- IDSA’s “Identity Defined Security Outcomes and Approaches” best practices
- Tenable’s blog “Identities: The Connective Tissue for Security in the Cloud” and on-demand webinar “Strengthen the Effectiveness of Your Identity Security Program with Zero Trust Maturity”
- CISA’s “Identity and Access Management: Developer and Vendor Challenges” and “Identity and Access Management Recommended Best Practices Guide for Administrators” publications
- Cloud Security Alliance’s blogs “Navigating the Top 10 Challenges in Cloud Identity and Access Management” and “Configuration and Monitoring of IAM”
5 - Known vulns: Everything old is new again
And in 2023, we re-confirmed that a frustrating scenario continues to play out: Attackers widely exploiting known vulnerabilities for which patches have long been available.
That was a key insight from Tenable Research’s “2022 Threat Landscape Report (TLR),” released in February. Tenable Research found this issue so prevalent that it ranked known vulnerabilities first on the report’s list of 2022’s top vulnerabilities.

(Source: “Threat Landscape Report” from Tenable Research, February 2023)
However, putting all the blame on security teams for not patching these bugs would be naive and simplistic, Tenable CSO and Head of Research Robert Huber cautioned.
“The lesson here is that the broad array of siloed cybersecurity tools and systems organizations have in place is not helping to reduce risk,” Huber wrote. Instead, cyber teams need a holistic view of their organization’s attack surface to properly manage risk and exposures, he added.
In June, CISA disclosed an incident that exemplifies this issue: Multiple attackers breached the web server of an unnamed U.S. federal agency by exploiting known, years-old vulnerabilities.
Further illustrating the challenge of prioritizing vulnerability remediation, CISA’s Known Exploited Vulnerabilities (KEV) catalog reached 1,000 items in September. By tracking known bugs exploited in the wild, it’s meant to help vulnerability teams prioritize. CISA marked the milestone in a blog and tackled the question of how to now prioritize “within the KEV.”
For more information about detecting, prioritizing and fixing vulnerabilities, check out these Tenable blogs:
- “You Can't Fix Everything: How to Take a Risk-Informed Approach to Vulnerability Remediation”
- “CVSSv4 is Coming: What Security Pros Need To Know”
- “Mind the Gap: How Waiting for NVD Puts Your Organization at Risk”
- “What Is VPR and How Is It Different from CVSS?”
- “Tenable 2022 Threat Landscape Report: Reduce Your Exposure by Tackling Known Vulnerabilities”
- “AA23-215A: 2022's Top Routinely Exploited Vulnerabilities”
6 - The stakes get higher for OT security in critical infrastructure
Urgency about the cyber safety of critical infrastructure grew in 2023. Threats multiplied and attacks intensified, especially from nation-state actors, as the attack surface for these organizations expanded due to factors like the convergence of IT and OT systems, and cloud adoption.
In terms of quantity, cyberattacks against critical infrastructure appear to be on the upswing globally, based on many reports that gather these stats for specific states, countries, industry sectors and attack methods.
The chart below, which tallies actual and projected global attacks costing victims more than $1 million, comes from the study “Impact, Vulnerabilities, and Mitigation Strategies for Cyber-Secure Critical Infrastructure,” published in April by researchers from Florida International University and Utah Valley University.
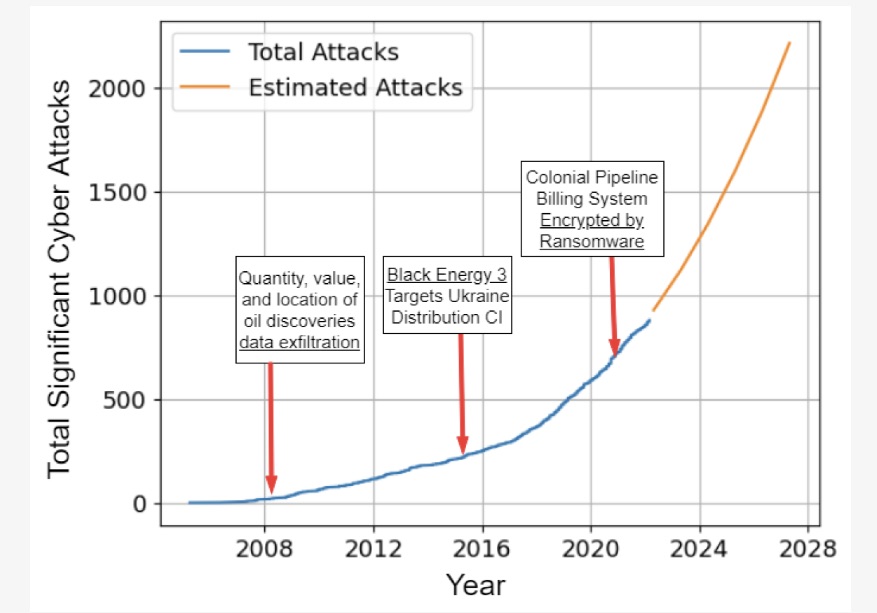
(Source: “Impact, Vulnerabilities, and Mitigation Strategies for Cyber-Secure Critical Infrastructure” study from Florida International University and Utah Valley University, April 2023)
Governments, worried about these facilities whose services are essential to society and to national security, took steps to boost their cybersecurity.
For example, here are some CISA initiatives:
- It launched in March its “Ransomware Vulnerability Warning Pilot Program” to help critical infrastructure facilities fend off ransomware attacks
- More recently it kicked off a pilot program to offer them free managed cybersecurity services
- In October, CISA and other agencies published guidance for improving open-source software security in OT environments
- In November, it launched the “Shields Ready” campaign to promote critical infrastructure security and resilience
For guidance on critical infrastructure cybersecurity:
- “Critical Infrastructure and the Cloud: Policy for Emerging Risk” (Atlantic Council)
- “How to Tackle OT Challenges: Asset Inventory and Vulnerability Assessment” (Tenable)
- “7 key OT security best practices” (TechTarget)
- “Guide to Operational Technology (OT) Security” (NIST)
- “Secure Both IT and OT Environments Effectively” (IANS Research)
- “A Practical Way To Reduce Risk on the Shop Floor” (Tenable)
VIDEOS
Tenable.ot Security Spotlight - The Ransomware Ecosystem
Tenable.ot Security Spotlight - Ransomware in OT Systems
And a bonus item!
This blog highlights six cyber trends, but it’s the season of giving so here’s one more: the new cybersecurity-disclosure rules from the U.S. Securities and Exchange Commission that just went into effect.
Adopted in July and finalized with some amendments in September, the rules establish new requirements for publicly traded companies regarding disclosures about their cybersecurity incidents, risk management, strategy and governance.
Their goal? To make cybersecurity disclosures more consistent, comparable and useful for decision-making, which will benefit companies, their investors and the markets, the agency said in a statement.

For example, with some exceptions, companies must disclose cyber incidents four business days after deeming them material, and describe their nature, scope and timing, as well as their actual or potential businesss impact. (In a bizarre pressure tactic, a ransomware gang filed an SEC complaint against a victim, alleging it didn’t comply with the new disclosure rules.)
“For a long time, the largest and most powerful U.S. companies have treated cybersecurity as a nice-to-have, not a must have. Now, it’s abundantly clear that corporate leaders must elevate cybersecurity within their organizations,” Tenable Chairman and CEO Amit Yoran told the Associated Press in July. He shared more of his thoughts in this LinkedIn post.
The new SEC rules are part of a broader trend by governments worldwide to place more accountability for cyber incidents on both technology vendors and cybersecurity leaders.
To get more details about the new rules, check out this July FAQ from Tenable; this statement from the SEC’s Division of Corporate Finance director; and guidance from the FBI and the Justice Department.
Also, check out coverage and analysis from CyberScoop, The National Law Review, TechCrunch, SANS Institute and SecurityWeek.
