The new capability is designed to make it more efficient for security teams to pass remediation recommendations on to the infrastructure team to implement. Here’s how it works.
What often determines how quickly a security issue is remediated (if at all) is the efficiency with which the security team can generate the finding and provide guidance to the infrastructure team on the proposed remediation.
This is because the security team responsible for determining whether or not there’s a security issue is usually focused on different goals than the infrastructure team responsible for environment availability and administration. While the security team wants any security issue to be repaired, the infrastructure team is often (and very justifiably) focused on ensuring that the remediation doesn’t cause more damage and that the infrastructure can continue supporting the required business logic. The infrastructure team, therefore, is very careful in applying any changes — especially to a production environment. Production has the most sensitive resources, as well as the resources that need to be most available, making it essential for teams to perform remediation responsibly without breaking anything.
Our understanding of these unique operational challenges facing cloud security teams was a major driver in our efforts to enhance the Tenable Cloud Security user experience with the ability to generate pull requests for remediation suggestions.
Tenable Cloud Security integrates with infrastructure-as-code repositories by allowing workflows to retrieve and send relevant information from state files to its API, as such:
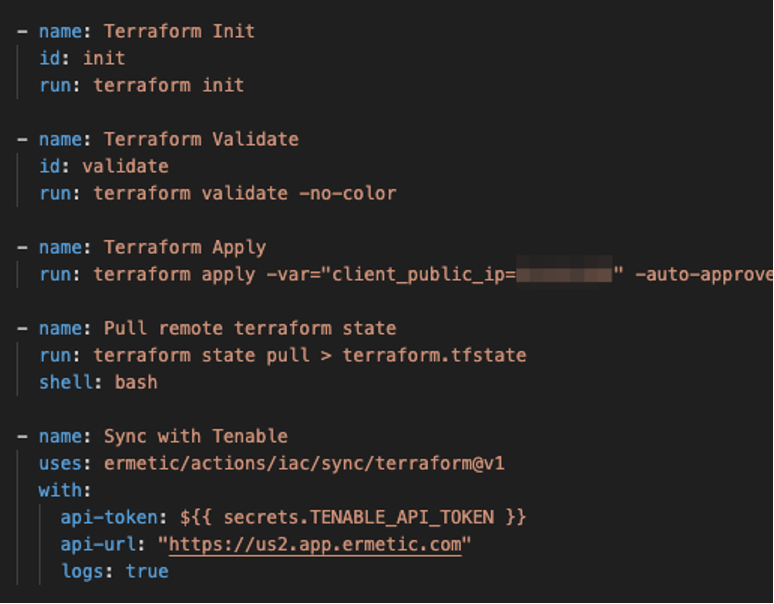
In Figure 1, we can see an example of a GitHub Actions workflow where Terraform state files are being retrieved as part of the provisioning process and then sent to the Tenable Cloud Security API.
Processing the state files allows Tenable to map the resources it scans for misconfigurations and other security-related findings to the line of code that provisioned them. As an important note, we don’t take state files as is in their entirety, but only within the parameters needed to perform this task.
An example of the end result of this operation can be seen below:
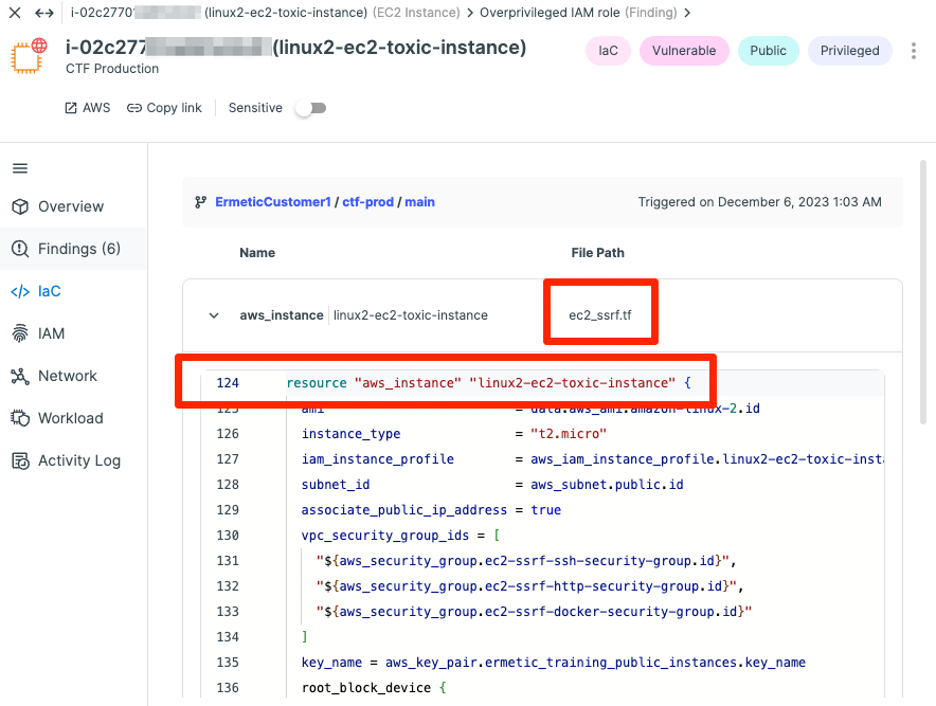
We dub this cutting-edge ability “cloud-to-code,” as it creates an invaluable connection between security findings that can sometimes only be detected once the resource is already provisioned and running to the code.
One such finding is over-privileged identity and access management (IAM) roles — you can identify an IAM role by analyzing its actual activity and detecting discrepancies between what it’s allowed to do and what it actually utilizes. This is, of course, not something that can be done before the resource is up and running.
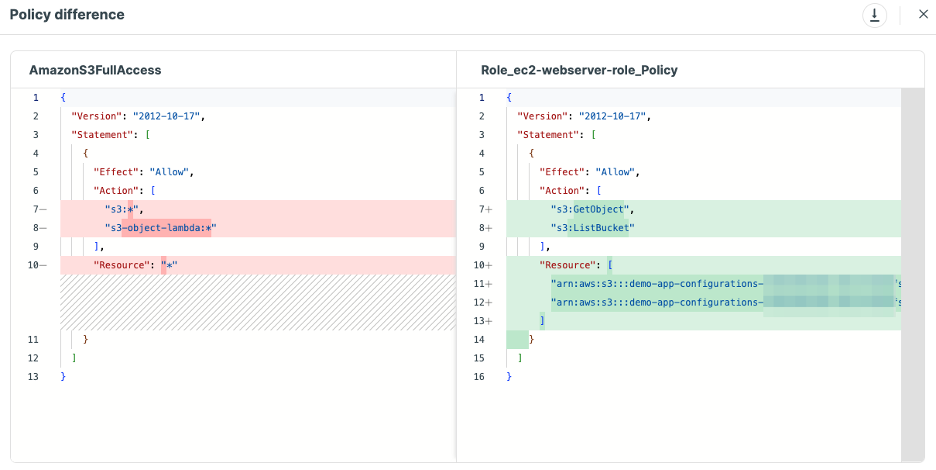
Tenable Cloud Security, as a pioneer in right-sizing permissions, happens to perform this kind of analysis, and, even better, it not only indicates if an IAM role is over-privileged, it also produces a right-sized policy for it, as can be seen in Figure 3:
Now here’s the fun part: leveraging cloud-to-code and an integration with the code repository itself, Tenable Cloud Security now supports creating a pull request directly from the console, allowing the security team using it to easily suggest modifications to the infrastructure to make it more secure.
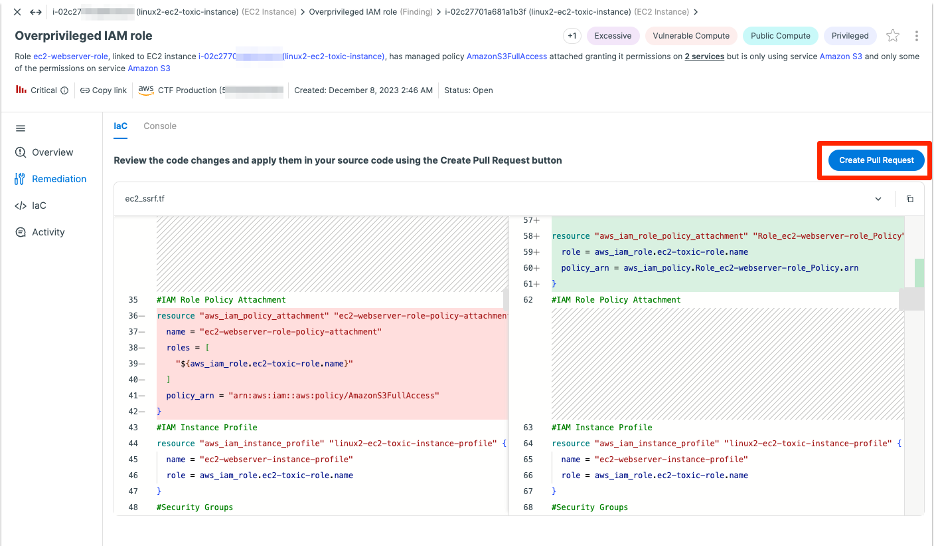
So what does this mean? In order to actually apply the change, the infrastructure team needs to simply review (and hopefully test) the modification. Once it’s approved, they can push it to production.
This is arguably the most effective method of communication between security and infrastructure teams around the remediation of findings; it’s safe, fast, accurate — and requires very little specialized expertise to be applied.
Want to learn more about Tenable Cloud Security or request a demo? Visit https://www.tenable.com/products/tenable-cloud-security
