CISA is calling on router makers to improve security, because attackers like Volt Typhoon compromise routers to breach critical infrastructure systems. Meanwhile, data breaches hit an all-time high in the U.S. Plus, Italy says ChatGPT violates EU privacy laws. And a cyber expert calls on universities to beef up security instruction in computer science programs. And much more!
Dive into six things that are top of mind for the week ending February 2.
1 - CISA urges secure router design, as DOJ disrupts Volt Typhoon router botnet
Manufacturers of small office / home office (SOHO) routers must follow “secure by design” principles for their products, which have been recently targeted by malicious hackers, including the China-sponsored Volt Typhoon gang.
So said the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) this week in the alert “Security Design Improvements for SOHO Device Manufacturers.”
The agencies “urge SOHO router manufacturers to build security into technology products from the beginning and encourage all customers of SOHO routers to demand better security by design,” the joint alert reads.

Recommendations for manufacturers of SOHO routers include:
- Ensure that they deliver automatic updates to these devices to patch security vulnerabilities, and that ideally the process requires no user intervention
- Boost the security of the routers’ management interface system so it’s safe to use when exposed to the public internet
- Set secure default configurations for the routers, and discourage customers from shifting to less secure settings
- Publicly and transparently disclose their routers’ vulnerabilities via the Common Vulnerabilities and Exposures (CVE) program
- Provide security-focused incentives for router designers and developers
The agencies also said in a statement that attackers use hacked SOHO routers as “launching pads” to compromise U.S. critical infrastructure providers. One of those attackers has been Volt Typhoon, but the router botnet it had been using to sting critical infrastructure operators got disrupted recently by the U.S. Department of Justice (DOJ).
The operation deleted the botnet’s malware from the hundreds of infected routers and disrupted the botnet’s communications, the DOJ said in the statement “U.S. Government Disrupts Botnet People’s Republic of China Used to Conceal Hacking of Critical Infrastructure.”
“China’s hackers are positioning on American infrastructure in preparation to wreak havoc and cause real-world harm to American citizens and communities, if or when China decides the time has come to strike,” FBI Director Chris Wray told the U.S. House of Representatives’ House Select Committee on the Chinese Communist Party, as quoted in an Associated Press article.
Speaking to the Associated Press, Tenable Chairman and CEO Amit Yoran said Wray’s warning is “an urgent call to action. Continuing to turn a blind eye to the risk sitting inside our critical infrastructure is the definition of negligence.”
To get more details, read the joint CISA/FBI alert “Security Design Improvements for SOHO Device Manufacturers,”
2 - Italian government says ChatGPT violates GDPR
And the drumbeat of AI regulatory challenges keeps getting louder.
This week, Italy’s data privacy watchdog declared that OpenAI’s ChatGPT generative AI chatbot runs afoul of the EU’s General Data Protection Regulation (GDPR).
Last year, the Italian data protection authority, known as Garante, imposed – and then lifted – a temporary ban on ChatGPT. However, it has now “concluded that the available evidence pointed to the existence of breaches of the provisions contained in the EU GDPR,” Garante said in the statement “ChatGPT: Italian DPA notifies breaches of privacy law to OpenAI.
OpenAI, which has 30 days to respond to Garante’s claims, told news outlets that it believes its practices are aligned with GDPR and that it will work with Garante on this matter.

Meanwhile, the U.S. Federal Trade Commission (FTC) last week said it is probing investments and partnerships between generative AI companies and cloud service providers.
Specifically, the FTC has requested information from Google’s parent company Alphabet, Amazon, Anthropic, Microsoft and OpenAI. Why these five? Both Amazon and Google have invested in Anthropic, while Microsoft has invested in OpenAI.
“Our study will shed light on whether investments and partnerships pursued by dominant companies risk distorting innovation and undermining fair competition,” FTC Chair Lina M. Khan said in the statement “FTC Launches Inquiry into Generative AI Investments and Partnerships.”
Here are some of the issues the FTC wants to know more about:
- Information about specific transactions, including the “strategic rationale” for investments and partnerships
- The implications of the partnerships and investments, such as new product release decisions
- The deals’ competitive impact on issues such as market share, competitors and sales growth potential
The companies have 45 days to respond.
For more information about the AI regulatory landscape:
- “AI Regulation is Coming- What is the Likely Outcome?” (Center for Strategic and International Studies)
- “Effective AI regulation requires understanding general-purpose AI” (The Brookings Institution)
- “States Take the Lead on Regulating Artificial Intelligence” (Brennan Center for Justice)
- “AI: the world is finally starting to regulate artificial intelligence” (The Conversation)
- “Europe agreed on world-leading AI rules. How do they work and will they affect people everywhere?” (Associated Press)
PODCAST / VIDEO
The EU’s AI Act, Explained (The Wall Street Journal)
Decoding the EU Artificial Intelligence Act (Stanford University)
3 - CISA official: Comp Sci programs must add security courses
Most top computer science programs in the U.S. don’t require students to take a single cybersecurity course, a situation that these universities must urgently address.
So said Jack Cable, a Senior Technical Advisor at CISA, in a blog post.
“This is unacceptable,” Cable wrote. “All too often, attacks exploit simple weaknesses that any developer with basic security knowledge could have stopped.”
At 23 of the top 24 computer science programs cybersecurity is treated at best as an elective, instead of as critical knowledge that every software developer should have.
“It is long overdue for academia to reconsider their role in producing a software developer workforce that enables increasingly damaging cyberattacks,” Cable wrote in the blog post titled “We Must Consider Software Developers a Key Part of the Cybersecurity Workforce.”

At a recent roundtable discussion in which Cable participated, the panelists identified three key challenges that make it difficult for universities to offer cybersecurity courses in computer science programs.
- The computer science field continues to view cybersecurity as a subdiscipline
- Computer science faculty lack resources and experience in cybersecurity
- Demand for software developers with security skills is weak
Possible solutions include adding security to computer science programs’ accreditation requirements; and increasing computer science curriculum materials.
If you have suggestions for boosting security education in computer science programs, you can share your ideas at this CISA “request for information” page.
4 - Data breaches in the U.S. skyrocket in 2023
How is the U.S. doing in the data protection realm? Things are bad and getting worse.
That’s the main takeaway from the Identity Theft Resource Center’s “2023 Annual Data Breach Report,” released this week. Data compromise incidents ballooned 78% last year, compared with 2022, and 72% compared with the previous all-time high recorded in 2021.
The overwhelming majority of those incidents were data breaches, and most were caused by cyberattacks, according to the report, which is now in its 18th annual edition.

Meanwhile, transparency is on the decline, as data breach notices that lack specific information about their attack vector almost doubled in 2023. Data breach notices with actionable information have dropped from about 100% in 2018 to 54% last year.
“Rather than dwell on the past, we are focused on what we can do moving forward to reduce the impact on victims,” ITRC President and CEO Eva Velasquez said in a statement.
“It starts with finding ways to reduce the value of personal information to identity criminals and seeking ways to improve the breach notice process to help protect both people and businesses,” Velasquez added.
For more information about data breach prevention and response:
- “What Security Leaders Need to Know About the ‘Mother of All Breaches’” (information Week)
- “Data Breach Response: A Guide for Business” (Federal Trade Commission)
- “17 Security Practices to Protect Your Business’s Sensitive Information” (Business.com)
- “Average cost of a data breach reaches $4.45 million in 2023” (Help Net Security)
- “Best and worst data breach responses highlight the do’s and don’ts of IR” (CSO)
5 - Report probes security views of open source project leaders
As the Log4j crisis laid bare, the security of widely-used open source software (OSS) is critical for the estimated 90% of organizations that use it globally.
If you’re interested in this topic, check out a new report published this week by the Open Source Security Foundation (OpenSSF) that focuses on a fundamental link in the OSS security chain: OSS project leaders, or maintainers as they’re more commonly known, and contributors.
Maintainers’ responsibilities typically include establishing an OSS project’s goals, steering the project, building a community of collaborators and ensuring the quality and security of the code.
“Which security practices do they espouse, and what ideas do they have to encourage their adoption?,” wrote Anna Hermansen, Ecosystem Manager at Linux Foundation Research, in a blog about the report.
Here are key findings from the report, which is titled “Maintainer Perspectives on Open Source Software Security” and is based on a survey of 441 OSS project maintainers and contributors:
- Software composition analysis (SCA) and static application security testing (SAST) are the tools most commonly used to assess the security of OSS packages
- Reviewing source code manually, however, remains “pervasive” with 39% of maintainers and contributors engaging in this practice
- Almost 70% of OSS project contributors would like to have defined, standardized best practices for secure software development
- While 87% of projects provide basic documentation for the software protocol, only 69% explain how to identify bugs and contribute to the software
- Contributors would like software security tools to gain more intelligence, and for security processes to become more automated
Which of the following best practices does your OSS project support?
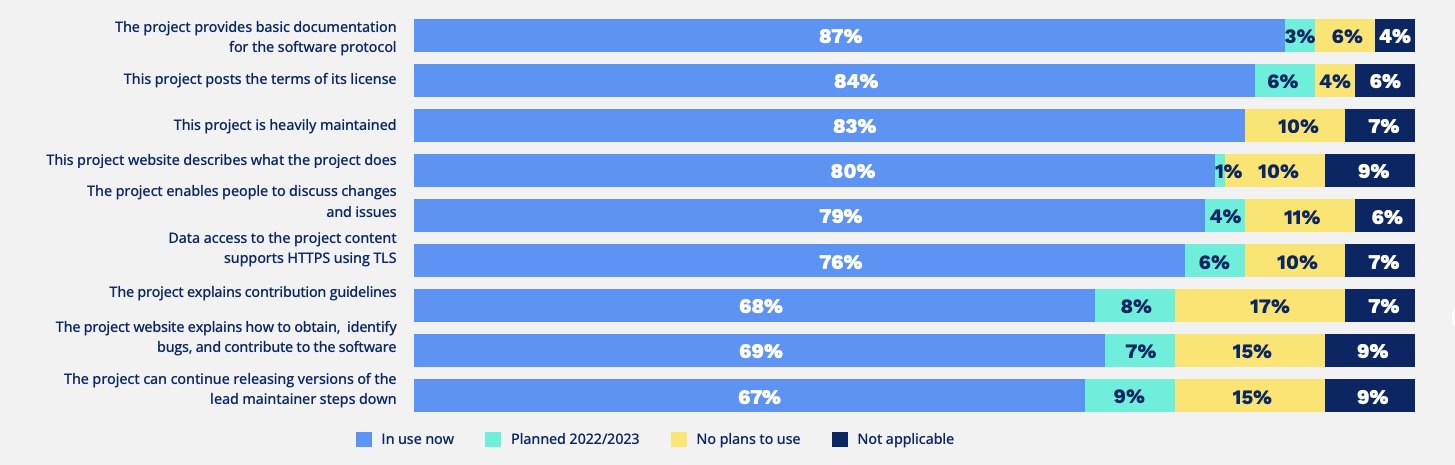
(Source: “Maintainer Perspectives on Open Source Software Security” report, Open Source Security Foundation, January 2024)
“If we don’t understand where maintainers are coming from, we have fewer opportunities to provide them with the necessary tools and resources,” Hermansen added in the blog titled "Maintainer Motivations, Challenges, and Best Practices on Open Source Software Security.”
For more information about open source software security:
- “Create an open source security policy for your organization” (TechTarget)
- “CISA Open Source Software Security Roadmap” (CISA)
- “White House releases report on securing open-source software” (CyberScoop)
- “Managing open source components in the software supply chain” (TechTarget)
- “NSA, CISA call on software developers, suppliers to improve open source software management practices” (Federal News Network)
6 - New Ivanti bugs disclosed, first patches roll out
And if you’re following the weeks-long saga of the Ivanti vulnerabilities, the vendor this week disclosed two new bugs in Ivanti Connect Secure and Ivanti Policy Secure, and released a first set of patches. Meanwhile, CISA again called for impacted organizations to urgently address this issue, and ordered federal civilian agencies to disconnect the affected products by midnight on Feb. 2.
To get all the latest details, check out the Tenable blog “CVE-2023-46805, CVE-2024-21887, CVE-2024-21888 and CVE-2024-21893: Frequently Asked Questions for Vulnerabilities in Ivanti Connect Secure and Policy Secure Gateways.”
For more information:
- “US gives federal agencies 48 hours to disconnect flawed Ivanti VPN tech” (TechCrunch)
- “Ivanti tried to patch its VPN security flaws — but just found more problems” (TechRadar)
- “Two new Ivanti bugs discovered as CISA warns of hackers bypassing mitigations” (The Record)
