The Volt Typhoon hacking gang is stealthily breaching critical infrastructure IT environments so it can strike on behalf of the Chinese government, cyber agencies say. Plus, ransomware gangs netted $1 billion-plus in 2023. In addition, new group tasked with addressing the quantum computing threat draws big tech names. And enterprises go full steam ahead with generative AI, despite challenges managing its risks. And much more!
Dive into six things that are top of mind for the week ending February 9.
1 - Alert: China-backed Volt Typhoon positioning itself to strike U.S. critical infrastructure
IT and operational technology security teams, listen up.
Volt Typhoon, a Chinese government-sponsored hacker group, could, at a moment’s notice, severely disrupt U.S. critical infrastructure operations, potentially harming Americans and hobbling military capabilities.
So said cybersecurity agencies from the U.S., U.K., Canada, Australia and New Zealand issued this week via the joint advisory “PRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure.”
The agencies believe that Volt Typhoon hackers, using stealthy “living off the land” techniques, are “pre-positioning” themselves in IT networks in order to move laterally to OT systems, and sow chaos if and when geopolitical or military conflicts erupt with the People's Republic of China (PRC).
Specifically, Volt Typhoon has compromised the IT environments of multiple critical infrastructure organizations, mostly in the communications, energy, transportation and water sectors, including an alarming breach that lasted a whopping five years, the agencies said.
“The PRC cyber threat is not theoretical,” Jen Easterly, Director of the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said in a statement. “And what we’ve found to date is likely the tip of the iceberg.”
Thus, IT and OT security teams at critical infrastructure organizations should urgently apply the advisory’s mitigations and use its guidance to hunt for malicious activity. In addition, they should incorporate the recommendations in the joint guide “Identifying and Mitigating Living Off the Land Techniques,” also released this week.
The advisory echoes comments made last week by FBI Director Chris Wray at a congressional hearing, after the U.S. government announced it had disrupted a botnet that Volt Typhoon was using to breach critical infrastructure systems.
Speaking to the Associated Press, Tenable Chairman and CEO Amit Yoran called Wray’s warning “an urgent call to action.”
“Continuing to turn a blind eye to the risk sitting inside our critical infrastructure is the definition of negligence,” Yoran added.
For more information about OT security, check out these Tenable resources:
- “Building Resilient OT Environments: Safeguards for Electric Utilities” (blog)
- “Critical Infrastructure Cybersecurity: Disrupt OT Attack Vectors” (white paper)
- “How to Tackle OT Challenges: Asset Inventory and Vulnerability Assessment” (blog)
- “2024 OT Security Trends: From the Boardroom to the Industrial Floor” (webinar)
- “A Practical Way To Reduce Risk on the Shop Floor” (blog)
VIDEOS
Ransomware in OT Systems
The Business Risk From a Ransomware Attack on OT Systems
2 - Report: Ransomware payments top $1 billion in 2023
After dropping in 2022, ransomware bounties unfortunately rebounded in a big way last year, crossing the $1 billion threshold.
That’s according to data from blockchain analysis firm Chainalysis, which attributed the bounceback to various factors, including:
- an intensification and escalation in attack frequency, efficiency, scope and volume
- the targeting of deep-pocketed organizations
- victims’ widespread exposure to vulnerabilities, such as the zero-day bug that impacted Progress Software’s MOVEit Transfer product
“Last year’s developments highlight the evolving nature of this cyber threat and its increasing impact on global institutions and security at large,” reads the Chainalysis report “Ransomware Payments Exceed $1 Billion in 2023, Hitting Record High After 2022 Decline.”
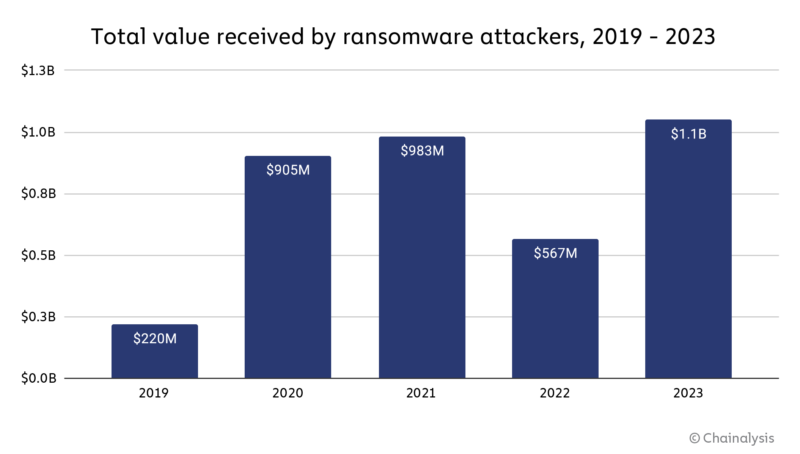
The dip in 2022 was “an anomaly, not a trend,” which Chainalysis attributes to one-time factors such as many ransomware gangs’ decision to shift their activities to the Russia-Ukraine war; and the FBI’s timely provision of decryption keys to Hive ransomware victims.
The $1.1 billion extorted from ransomware victims is the highest annual total since Chainalysis started tracking this statistic in 2019.
“Although 2022 saw a decline in ransomware payment volume, the overall trend line from 2019 to 2023 indicates that ransomware is an escalating problem,” the report reads.
For more information about ransomware trends and prevention, check out:
- “Ransomware trends, statistics and facts heading into 2024” (TechTarget)
- “FAQ for MOVEit Transfer Vulnerabilities and CL0P Ransomware Gang” (Tenable)
- “Ransomware prevention a focus for storage stewards in 2024” (TechTarget)
- “MGM Resorts Reveals Over $100M in Costs After Ransomware Attack” (Infosecurity Magazine)
- “Preventing Ransomware and Malware Starts with Good Cyber Hygiene” (Infosecurity Magazine)
VIDEOS
Tenable CEO Amit Yoran discusses Las Vegas ransomware attacks with CNN (CNN)
2024 Ransomware Trends and Predictions (SANS Institute)
3 - Linux Foundation, tech giants team up to fight quantum computing threat
The urgency to prepare for future attacks that’ll use ultra powerful quantum computers continues to intensify.
This week, the Linux Foundation launched the Post-Quantum Cryptographic Alliance (PQCA), a group tasked with tackling the cryptographic security threats from quantum computers.
Expected to be available by 2030, quantum computers will be able to decrypt data protected with today’s public-key cryptographic algorithms. Consequently, it’s critical to develop quantum-resistant encryption algorithms in order to prevent a global data-theft disaster.

The PQCA, whose members include Amazon, Cisco, Google, IBM, Nvidia and the University of Waterloo, “will help accelerate the development and adoption of post-quantum cryptography in open source and beyond,” Jim Zenlin, the Linux Foundation’s Executive Director, said a statement.
Specifically, the PQCA will:
- Produce high-assurance software implementations of standardized algorithms via its PQ Code Package project
- Support the development and standardization of new post-quantum algorithms via its Open Quantum Safe project
- Help organizations and open source projects align with the U.S. National Security Agency’s “Commercial National Security Algorithm Suite 2.0”
In addition, several PQCA members are co-authors of the first four algorithms selected by the U.S. National Institute of Standards and Technology’s (NIST) “Post-Quantum Standardization Project.”
Back in September, MITRE launched a similar industry group called the “Post-Quantum Cryptography Coalition,” to which IBM and the University of Waterloo also belong.
To get more details, check out:
- The Linux Foundation’s announcement “Post-Quantum Cryptography Alliance Launches to Advance Post-Quantum Cryptography”
- The Post-Quantum Cryptography Alliance’s website
- The Open Source Security Foundation’s blog “Post-Quantum Cryptography Alliance Launch”
For more information about the quantum computing threat:
- “Next steps in preparing for post-quantum cryptography” (U.K. National Cyber Security Centre)
- “Inside NIST's 4 Crypto Algorithms for a Post-Quantum World” (DarkReading)
- “NIST: Quantum-resistant algos will be ready in 2024” (Tenable)
- “Quantum apocalypse: Experts warn of ‘store now, decrypt later’ hacks” (Silicon Republic)
- “Will Quantum Computers Become the Next Cyber-Attack Platform?” (InformationWeek)
VIDEOS
Post-Quantum Cryptography: the Good, the Bad, and the Powerful (NIST)
Quantum Computers, explained (Cleo Abram)
Michio Kaku: Quantum computing is the next revolution (Big Think)
4 - Google: Weak credentials are top vector for cloud compromises
It’s the passwords, stupid.
A whopping 51% of compromises suffered by Google Cloud customers in 2023 were caused by credential issues, namely the use of weak passwords or of no passwords at all. That’s a key insight from the “H1 2024 Threat Horizons Report,” published this week by Google's Cybersecurity Action Team.
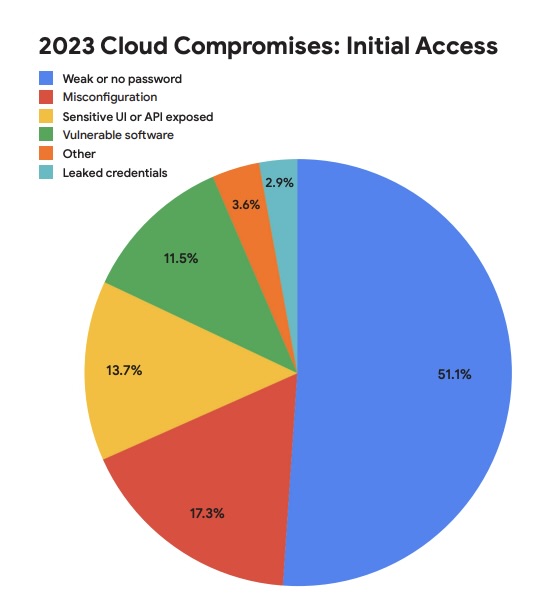
(Source: Google Cybersecurity Action Team’s “H1 2024 Threat Horizons Report,” February 2024)
So what was the top motivation driving these hackers? Most were looking to use the cloud environment’s processing power for their cryptomining activities.
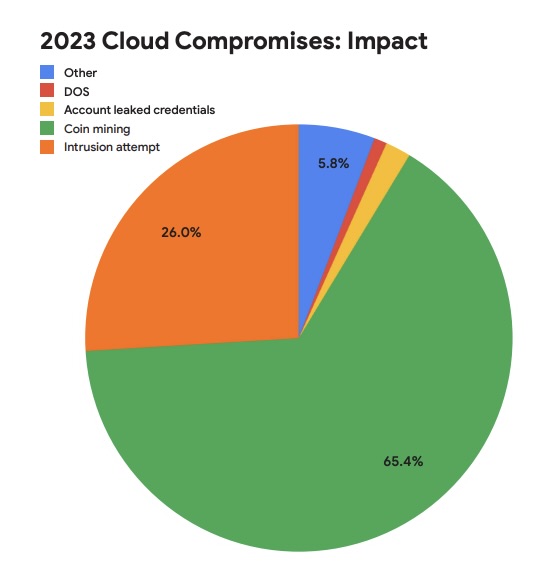
(Source: Google Cybersecurity Action Team’s “H1 2024 Threat Horizons Report,” February 2024)
“Credential abuse resulting in cryptomining remains a persistent issue, with threat actors continuing to exploit weak or nonexistent passwords to gain unauthorized access to cloud instances, while some threat actors are shifting to broader threat objectives,” the report reads.
For more information about cloud security in general, and about identity and access management in the cloud specifically:
- “Cloud identity: Are you who you say you are?” (ComputerWeekly)
- “Cloud Leaders Sound Off on Key Challenges” (Tenable)
- “Top 8 cloud IAM best practices to implement” (TechTarget)
- “Poor Identity Hygiene at Root of Nation-State Attack Against Microsoft” (Tenable)
- “Defining Shadow Access: The Emerging IAM Security Challenge” (Cloud Security Alliance)
- “Beyond the Horizon: Top 5 Cloud Security Trends to Watch in 2024” (Tenable)
5 - Enterprises lack generative AI controls, plow ahead anyway
And a recent survey shows that enterprises continue adopting generative AI due to its transformative potential, while admitting their ability to manage its risk and governance are shaky.
In its “State of Generative AI in the Enterprise” report, Deloitte polled about 2,800 high-level executives from 16 countries and found the following regarding their generative AI risk-management capabilities:
- Only 25% say their organizations are either “highly” or “very highly” ready to deal with generative AI governance and risk issues
- Governance concerns cited include: lack of confidence in results; intellectual property issues; data misuse; regulatory compliance; lack of transparency
- Only 47% say their organizations are doing enough to educate staff on generative AI’s capabilities, benefits and value

Simultaneously, respondents see a tremendous potential in generative AI, with 79% expecting it to unleash “substantial organizational transformation” in less than three years.
“Business leaders are under an immense amount of pressure to act, while ensuring appropriate governance and risk mitigation guardrails are in place,” Deloitte Global CEO Joe Ucuzoglu said in a statement.
For more information about how to use AI securely and responsibly:
- “Considerations for Implementing a Generative Artificial Intelligence Policy” (ISACA)
- “Top 10 Critical Vulnerabilities for Large Language Model Applications” (OWASP)
- “A CISOs Guide: Generative AI and ChatGPT Enterprise Risks” (Team8)
- “Envisioning Cyber Futures with AI” (Aspen Institute)
- “Using AI securely: Global cyber agencies publish new guide” (Tenable)
6 - U.K. bank: More people fell for romance scams in 2023
And with Valentine’s Day approaching, here’s a reminder: Cybercriminals are always hunting for lonely hearts online that they can steal money from.
The number of people scammed by cyber fraudsters pretending to be love interests rose 22% last year, according to Lloyds Bank. However, there was a silver lining: victims’ average monetary loss dropped 16% compared with 2022.

Other findings include:
- Men were slightly more likely to fall for these scams
- Women’s losses on average were much higher (76%) than men’s
- People between 55 and 64 were more likely to get scammed but those between 65 and 74 lost the most money on average
Those figures are based on the U.K. bank’s analysis of romance scams reported by its customers during 2023.
“Social media and online dating apps are rife with fake profiles, and it can be hard to tell who is genuine,” Liz Ziegler, Fraud Prevention Director at Lloyds Bank, said in a statement.
So how can you spot a romance scammer? Lloyds Bank recommends being wary of any stranger that contacts you out of the blue online, especially if the person:
- looks like a professional model in their profile photos
- always has a litany of excuses for not meeting you in person
- asks you for personal or financial details
- requests that you send them money
