Background
Cloud cryptomining has become an emerging trend in recent years, powered by the scalability and flexibility of cloud platforms. Unlike traditional on-premises infrastructure, cloud infrastructure allows attackers to quickly deploy resources for cryptomining, making it easier to exploit. One of the most common cryptomining threats for cloud environments is the Kinsing malware.
Kinsing is a notorious malware family active for several years, primarily targeting Linux-based cloud infrastructure. Known for leveraging various vulnerabilities to gain unauthorized access, the threat actors behind the Kinsing malware typically deploy backdoors and cryptocurrency miners (cryptominers) on compromised systems. After infection, Kinsing uses system resources for cryptomining, which leads to higher costs and slower server performance.
Recently, we discovered that Kinsing also attacks Apache Tomcat servers, and uses new techniques to hide itself on the filesystem, including utilizing innocent and non-suspicious file locations for persistence. In this article, we present our technical findings and share relevant indicators of compromise (IOCs) to help the community defend against this emerging threat.
Technical details
Kinsing campaigns are known for taking advantage of vulnerabilities in containers and servers in order to deploy malware, specifically backdoors and cryptominers. In this case, we've detected multiple infected servers within a singular environment, including an Apache Tomcat server with critical vulnerabilities. Apache Tomcat is an open source server that provides static data (like images and other static content), which makes it fully accessible from the internet, making it an attractive attack surface.
The Kinsing malware uses different locations to stay undetected and hides itself as a system file. We've found it in four locations, presumably for persistence purposes. Interestingly, three of these locations are manual files, or 'man' pages, where malware is rarely found. This unusual technique leverages the assumption that defenders typically don't search for malicious files in those locations. Here are the locations:
- /var/cache/man/cs/cat1/: typically used for user-level commands and applications.
- /var/cache/man/cs/cat3/: usually associated with library functions and programming interfaces.
- /var/lib/gssproxy/rcache/: The gssproxy (Generic Security Services Proxy) is a service that provides a proxy interface to the Kerberos library, making it easier for applications to use Kerberos authentication.
- /var/cache/man/zh_TW/cat8/: used for system administration and maintenance commands. Note the tz_TW folder - this is a Taiwan / Chinese folder. We can assume that the attackers have managed to create this directory structure as part of their malware installation and assume they won’t get discovered on this path.
These locations are typically used for legitimate system files, allowing the malware to blend in and avoid detection. By leveraging these seemingly innocuous paths, the attackers increase the chances of their malware staying unnoticed on compromised systems.
The malicious file itself detected is not new. It was first spotted at the end of 2022 in China. This specific attack on the Tomcat server started in mid-2023 based on the creation dates:
- var/cache/man/cs/cat3/ 06/22/2023
- var/cache/man/zh_TW/cat8/ 07/04/2023
- var/cache/man/cs/cat1/ 07/30/2023
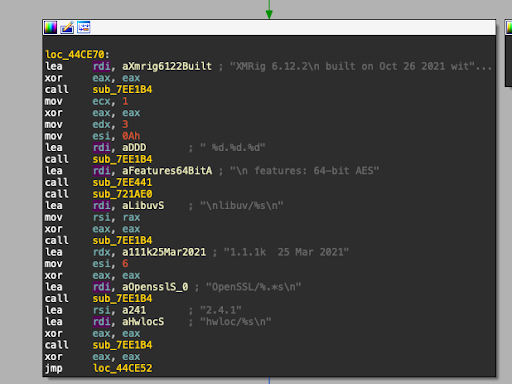
We see that the malicious operation has been active for almost a year without anyone noticing it. The malware has a cryptominer embedded in it called XMRig. XMRig is an open-source CPU mining software used for the mining of Monero, a cryptocurrency with high privacy. In the figure below, we can see that the version of XMRig is 6.12.2, while the current version on GitHub is 6.21.2:
Identifying affected systems
An effective detection mechanism that leverages research (such as the one presented here) is essential to locate this type of compromise.
To address this need, Tenable Cloud Security has recently introduced a new malware detection feature designed to enhance our existing cloud security capabilities and work in full synergy with them. This capability effectively identifies malware across various cloud workloads, providing a critical layer of security by detecting threats to mitigate the harm they may cause. Our solution offers practical, straightforward integration with your cloud infrastructure, ensuring that security is both seamless and robust.
/**/| Malware Name | SHA-256 | |
|---|---|---|
| XMRig |
|
To understand how this feature can work for your organization, we invite you to request a demo of Tenable Cloud Security.
