For anyone who has followed the the Verizon Data Breach Investigations Report (DBIR) through its many iterations, the findings for 2017 come as no surprise. Credentials theft, phishing and ransomware remain the top attack vectors, and the best defense is still to focus on the basics of cyber hygiene with the goal of achieving cyber operational excellence across the organization.
Credentials theft, phishing and ransomware remain the top attack vectors, and the best defense is still to focus on the basics of cyber hygiene
Now in its tenth year, the DBIR is an annual glimpse into the murky world of cybercrime and its impact on the enterprise. The data-driven report still carries significant influence within the information security industry, but has earned criticism for not having anything new to say in recent years. But you can’t shoot the messenger just because you don’t like the message. If the DBIR findings are starting to sound repetitive, it’s because most organizations are still making the same mistakes with cybersecurity that they have been making for over a decade, by failing to prioritize security at the board level and not investing the time and resources to do security right.
Guard your credentials
Weak, stolen or compromised credentials remain the leading cause of breaches. With more than one billion credentials stolen in 2016 (page 7), relying on passwords alone without augmenting them with two-factor authentication is throwing caution to the wind. Since users like to reuse credentials from one site to another, you not only have to worry about protecting your own credentials from being stolen, but you also have to worry every time someone else’s database of passwords gets leaked online. This is why two-factor authentication is so important.
Teach and be vigilant
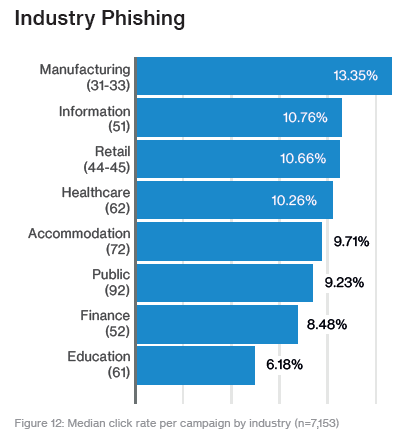
Links were made to be clicked on – that is their sole purpose. Users must click on links to do their jobs, but clicking on links in phishing emails is also one of the top ways attackers can gain entry into your networks. According to the DBIR, security-awareness training exercises, while somewhat effective, will never get you to zero links clicked; there is no significant difference in industries where users click links more frequently (page 11).
Regardless of the amount of security-awareness training you provide, your users are human and they will make mistakes, sometimes clicking on the wrong things. The key then becomes detection, containment and rapid remediation so that an incident doesn’t turn into a breach.
Don’t pay, remember to backup
When looking at ransomware figures in this year’s report, keep in mind that ransomware attacks seldom result in data disclosure. That means that ransomware numbers do not fall under Verizon's definition of a breach, so the report’s charts and graphs may not include ransomware attacks. But there is an interesting ransomware statistic on page 23: ransomware accounts for 72% of malware incidents in the healthcare industry as reported by DHHS. That seems like an absurdly high number. While it could be that healthcare has been disproportionately targeted due to their predilection to pay the ransom, it could be that the U.S. Department of Health and Human Services has stricter reporting requirements. Either way, the message is clear that ransomware should be considered a significant threat. The really sad thing about these numbers is that ransomware is easily defeated by proper backups. Make sure you not only do proper backups but you also test restores to assess the integrity of your data before a crisis occurs.
You can think of ransomware as the monetization of poor cyber hygiene, because when you come right down to it, ransomware is simply an exploitation of the most well-known vulnerabilities to gain entry into enterprise networks. This is especially true of the healthcare industry, where overall cyber readiness lags behind other industries such as financial services. Keeping all your assets patched and up to date – not just servers, but mobile devices, virtual machines, cloud apps – goes a long way towards preventing ransomware attacks. Patching works, as Verizon reported in Appendix B (read on).
Patching works
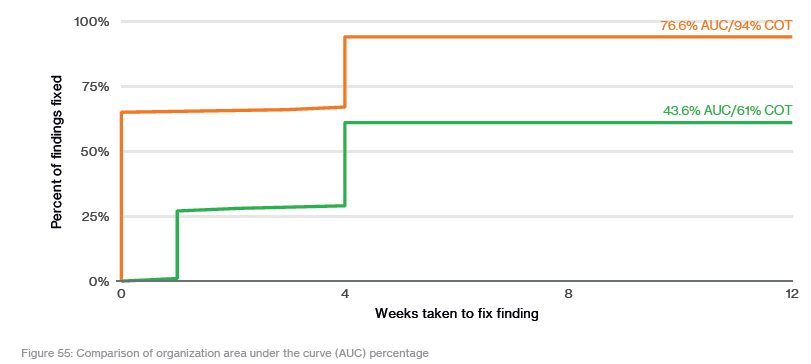
Verizon takes a deeper dive into the patching process in Appendix B (page 64) of the report. The good news is that:
Only a single-digit percentage of breaches in the DBIR involved exploiting a vulnerability.
Patching vulnerabilities and configuration weaknesses is still a highly effective deterrent to attacks. But there is still more patching to be done.
Verizon found that organizations tend to patch everything that they are going to patch rather quickly, and everything else tends to stay unpatched for a very long time:
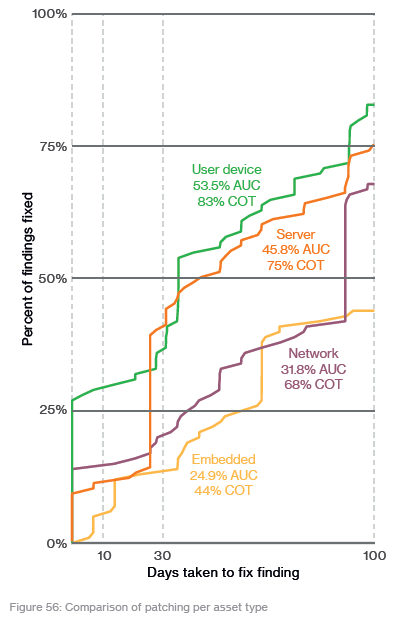
Verizon also breaks its patching data out by device type (page 65) with User and Server devices receiving the most patches, followed by Network patches and Embedded devices:
This is something that information security professionals have known for a long time: that routers, switches and other “closet” devices seldom see any patch love. It is nice to see data to back this up.
Back to basics
With data collected and collated from over sixty different organizations, the DBIR is a valuable tool to help CISOs determine how to allocate security resources to best defend their networks. such as how best to improve your threat response time, or how to make things more difficult for attackers.
A common theme throughout the report is that proper cyber hygiene, or simply following infosec best practices, will go a long way to protect your organization. Conduct a proper inventory of your hardware and software, patch systems in a prioritized manner, verify that your network equipment is properly configured and deployed, stay on top of inactive user credentials and enable two-factor authentication. Oh, and don’t forget your backups.