I am often asked, “How can I be more productive and get better results from my vulnerability scans?” This question could be the result of a failed audit, network outage or breach that was previously undetected. Traditionally, vulnerability scanning may consume a large amount of resources. Vulnerability scanning is also often perceived as being disruptive and intrusive to the environment. The Tenable.io Credentialed Scan Failures report can assist you and your organization in making better, more informed decisions on how to improve your vulnerability management program.
Identify vulnerability or prove exploitability?
Non-credentialed scanning
There are two philosophies of vulnerability scanning. The first philosophy believes that a system needs to be penetrated to prove that the system is, in fact, vulnerable. This non-credentialed type of intrusive scanning methodology is based on attacking a system in the same manner that a malicious actor would. There is merit to this type of scanning, as successful attacks prove that devices are vulnerable to exploits.
Tenable.io uses advanced technologies to try to avoid any unnecessary disruption to services, but there is the risk of having the non-credentialed scan leave fragile systems and some network devices in an unstable state. This instability may lead to a loss of data and revenue, and has the potential for significant legal or financial impact. All too often, when using non-credentialed scanning, more questions than answers are created.
Credentialed scanning
The second philosophy is credentialed scanning. Credentialed scanning is a less disruptive scanning technique that is performed with valid credentials. Operations from OS identification to port scanning are performed locally on the host. For example, devices can be queried locally to see if a patch has been applied.
Looking directly at the installed software, including the version numbers, vulnerabilities can easily be identified. Password policies can be read, USB devices can be enumerated and anti-virus software configurations can be checked, all with minimal to no impact on the device. This consumes far less system and network resources than the previous method. Credentialed scanning also presents less risk to the environment, and the results are far more accurate.
The Tenable.io solution
The benefits of credentialed scanning are significant. To ensure that you are reaping those benefits, you need to be certain that credentialed scanning is working. When I want to know how many credentialed scan failures have occurred, I look to the Credentialed Scan Failures report in Tenable.io.
The Credentialed Scan Failures report delivers an organized list of failed credentialed scans that you can use to quickly identify and remediate scanning issues on a network. The report covers a 25-day scanning history and provides a breakdown of various Windows scan issues and SSH failures, as well as general credential failures. You can use this report to present information on the success (or failures) of your credentialed vulnerability scanning program.
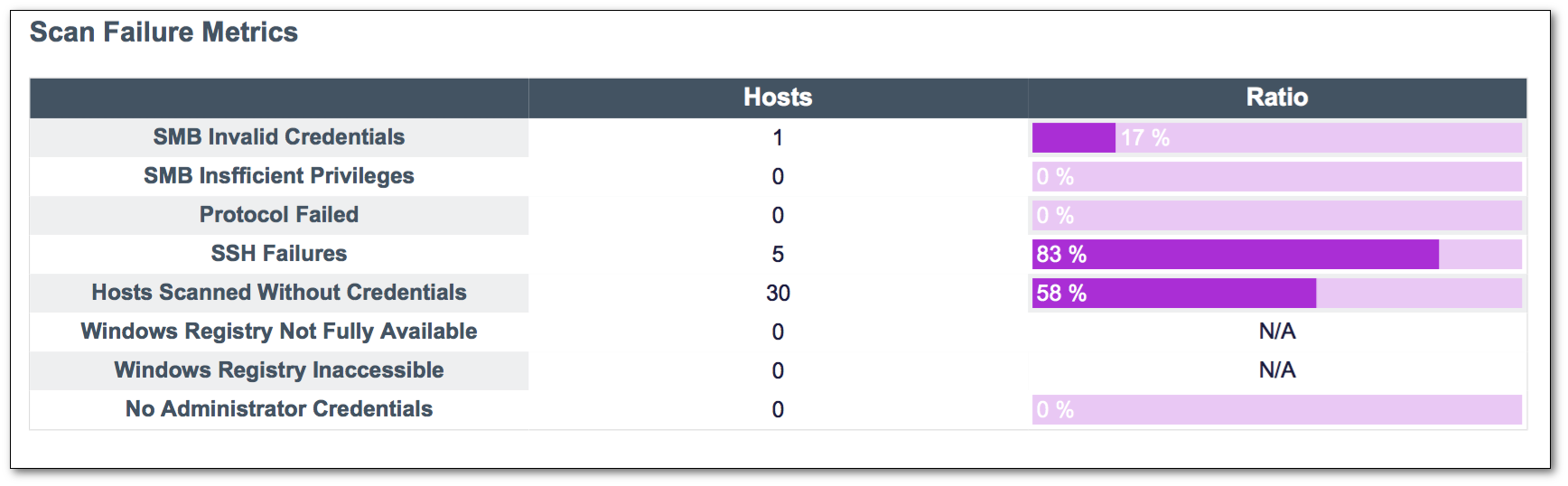
Key elements in this report, such as the Scan Failure Metrics element, provide an overview into many issues that may be attributed to credentialed scan failures. This summary is useful for executives who want a complete overview of the status of credentialed scanning within the organization. For those who want a deeper dive, failures identified on this element are expanded in detail in other chapters of the report.
For example, you see in the above image that there is one SMB invalid credential failure, five SSH failures and thirty hosts scanned without credentials. Referencing the report sections specific for those failures, you can identify why those failures occurred and remediate the issues. You can also identify each and every host by IP and DNS that was scanned without credentials.
Benefits of credentialed scanning
Vulnerability scanning on a regular basis, audits and penetration tests should all be part of your ongoing risk management program. Scanning without credentials is valid for some attack vectors and identifying what is visible. But credentialed scanning looks under the hood and beyond the surface to provide a very accurate snapshot of your environment. Credentialed scans are quick, easy and safe, resulting in a better picture of your overall vulnerability state and enabling you to identify and analyze potential security issues before the hackers do.
Try Tenable.io
Tenable.io provides accurate information on how well your organization is addressing security risks and helps track improvements over time. Get a free trial of Tenable.io Vulnerability Management for 60 days.