According to the 2017 Verizon Data Breach Investigations Report (DBIR), privilege misuse accounts for approximately 15% of breaches and 18% of incidents among the organizations surveyed (page 38). Monitoring your network for unauthorized insider access and privilege misuse is essential to keeping your valuable data secure and meeting many regulatory requirements. Verizon estimates that as much as 60% of this threat pattern is the result of average users “absconding with data in the hope of converting it to cash somewhere down the line” (page 48). How can you block privilege misuse and tackle malicious insiders in your organization? Tenable.io™ can help you detect misconfigured accounts and unauthorized usage through credentialed compliance audit scanning.
What data is being accessed or stolen?
The Verizon DBIR tells us that personal information and medical records are the most common targets for financially-motivated actors, making up about 71% of the data targeted. Unauthorized database access (57%) and employee email access (9%) contributes to approximately 66% of these types of breaches (page 48). According to Verizon:
The practice of limiting, logging and monitoring internal account usage extends beyond rogue employees. One of the main goals of external adversaries is to gain access to legitimate internal credentials to advance their assault (page 49)
Verizon also notes:
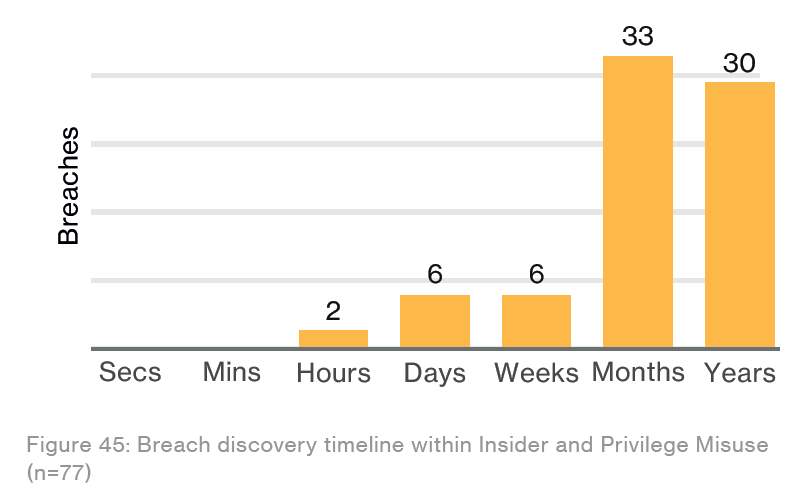
The discovery timeline for this pattern … shows that these breaches are more likely to take months and years to detect rather than weeks or less (page 49)
Source: Verizon 2017 Data Breach Investigations Report, page 49
This is where Tenable.io can help.
What can be done?
Blocking the impact of these incidents requires a two-fold approach: preventing unprivileged access and detecting anomalous or unauthorized behavior. There are many best practices to these ends, including monitoring system configurations, account usage, and password policies. Tenable.io supports configuration monitoring using several standards such as the CIS benchmarks, which can provide you with helpful guidelines that are known to promote operational excellence in network security. In addition to a variety of compliance check options, other common settings such as password policies, group assignments, and dormant user accounts can also be easily monitored using Tenable.io.
Configuration scanning in Tenable.io
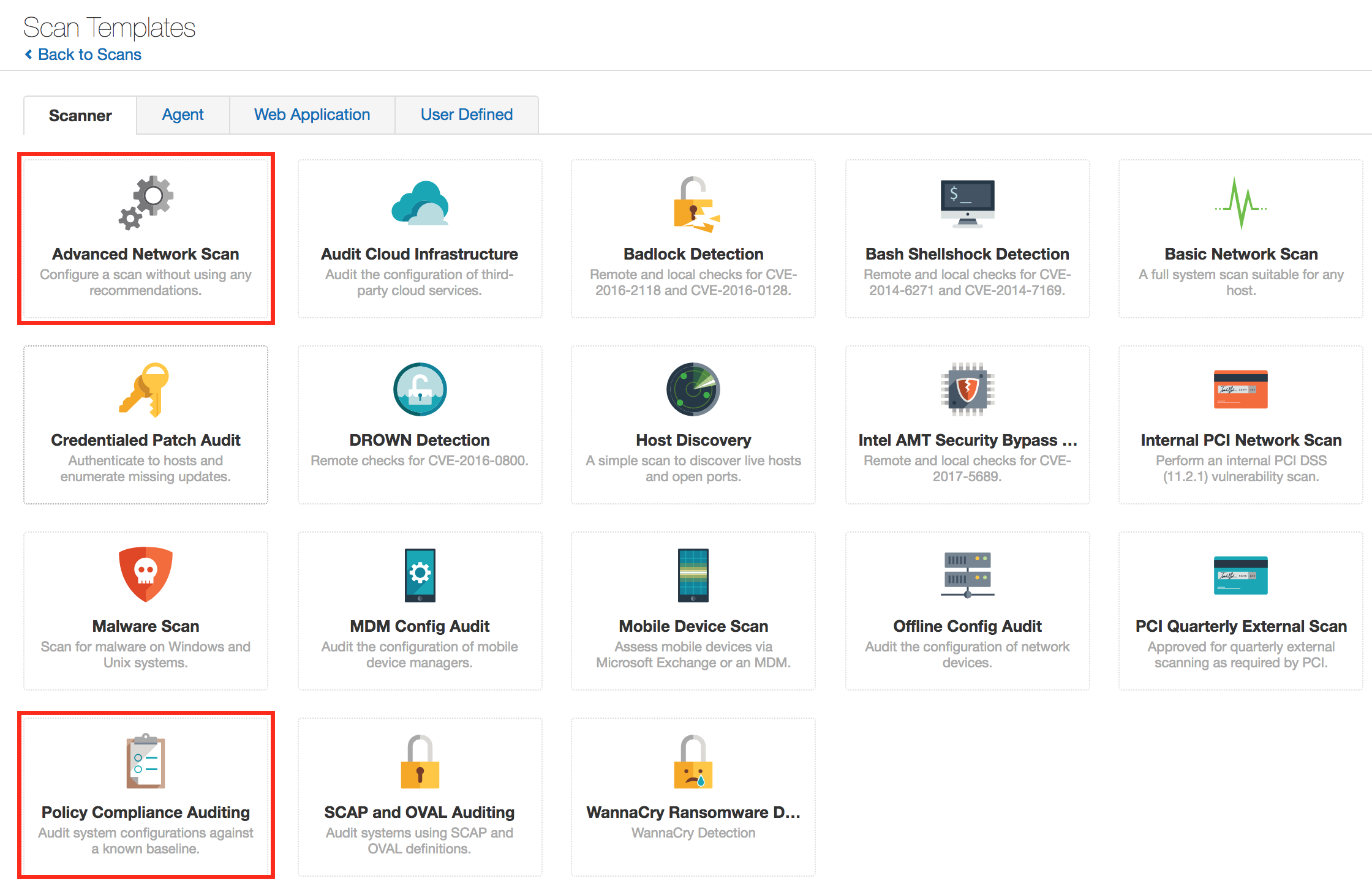
Performing configuration and vulnerability scans is key to detecting insufficient passwords, misassigned user groups, and dormant user accounts. Luckily, setting up a compliance scan in Tenable.io is simple. Log into Tenable.io and navigate to Scans > My Scans. Click New Scan for a variety of scan templates to choose from. There are multiple templates that involve compliance auditing, but we are going to focus on the Policy Compliance Auditing and Advanced Network Scan templates.
Policy Compliance Auditing template
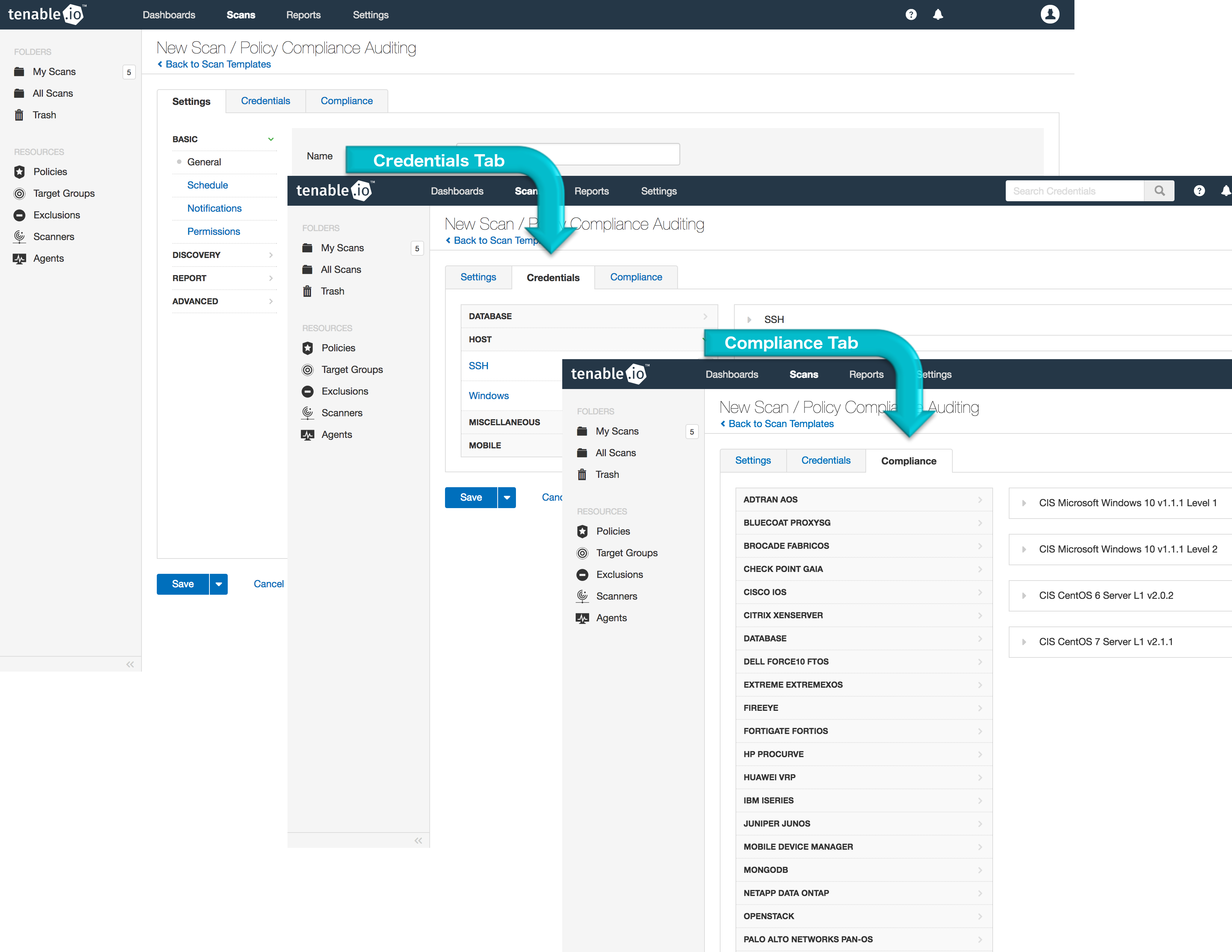
Once you create a new scan and choose the Policy Compliance Auditing template, you can configure the rest of the scan settings. In the first tab, fill in the settings you want to use and the targets you wish to scan. Use the second tab to enable credentialed scanning, which is required for compliance checks. On the last tab, choose Tenable audit files to use as baselines against the target hosts. Use the search field at the top of the page to filter the audit files by keyword, or simply browse through them manually. Once all the settings are chosen, save and run the scan to gather policy compliance data from hosts in your organization.
Advanced Network Scan template
If you want more control over the settings used in your policy compliance scan or want to merge a vulnerability and compliance scan, you can also use the Advanced Network Scan template. Customizing an advanced scan can be especially useful because many vulnerability plugins can aid in identifying privilege misuse or unusual user behavior. Simply configure the settings in each tab, then save and run your custom scan.
Sifting through results
Once scans have been run and data has been gathered, you can start reviewing the results to understand potential weaknesses in your network. Analyzing the results from the vulnerability and compliance scans can easily be done using the scan results page.
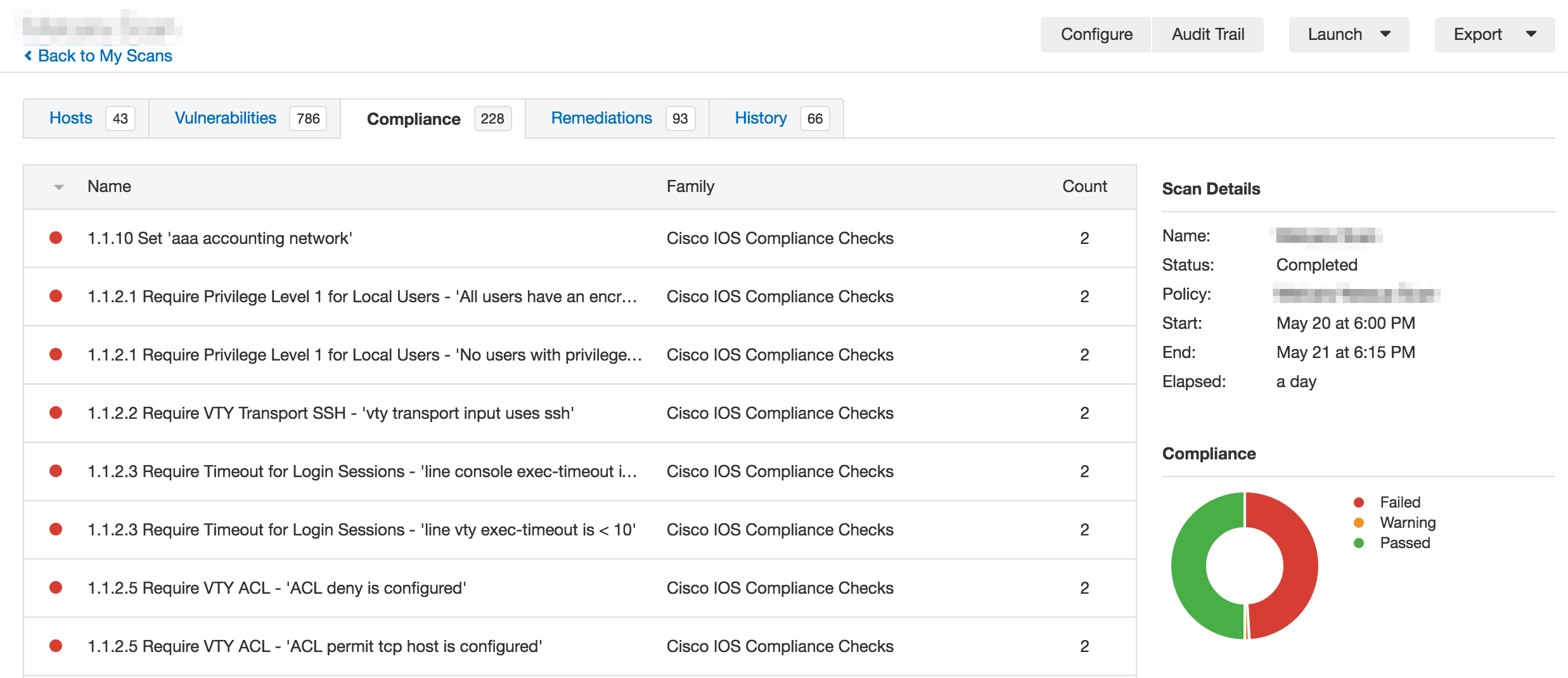
Scan results
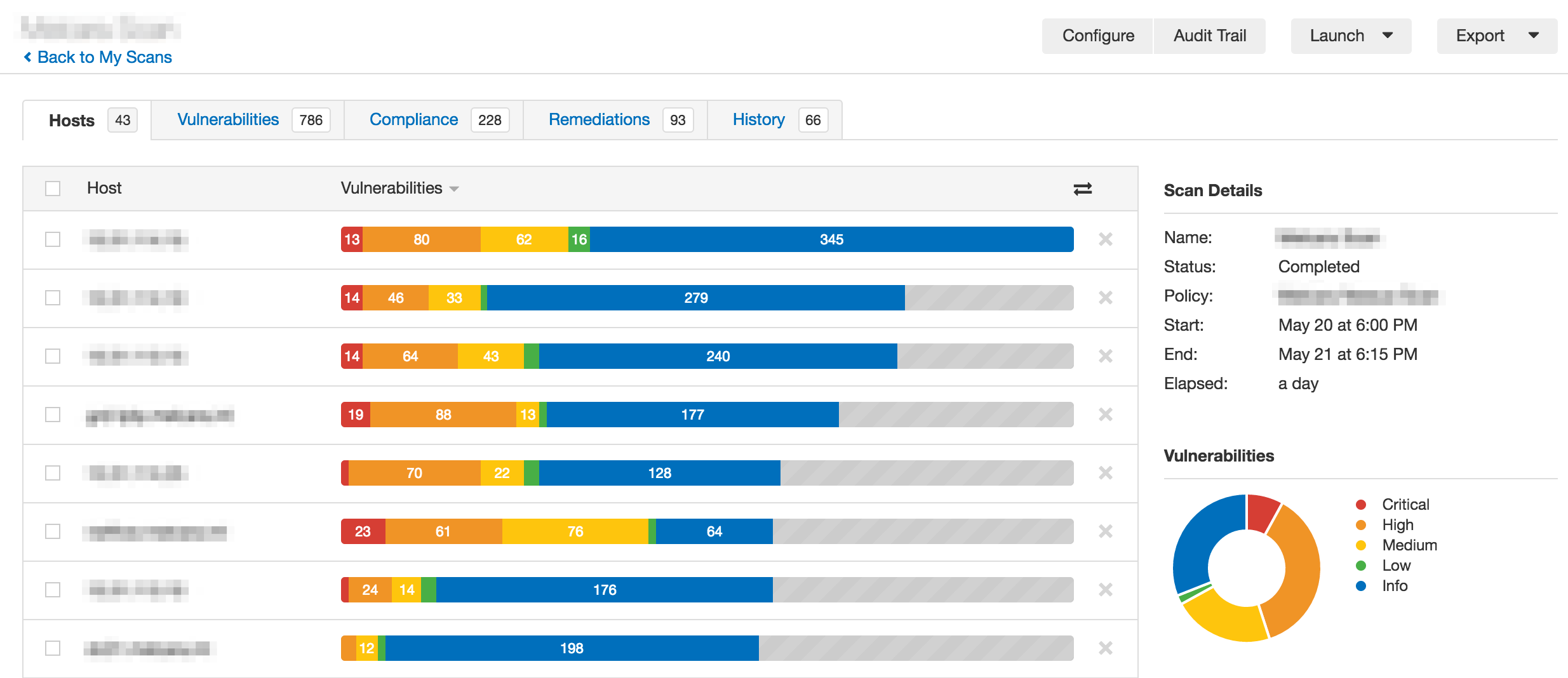
Click on a scan in the My Scans list to view a page of details. If the scan is currently running, the History tab will be the first displayed. Once a scan has been run multiple times, use the Diff feature to compare the results of two runs. Note that choosing the more recent scan as the primary result will give you everything that disappeared between scans, and choosing the earlier scan as the primary result will give you everything new. The Hosts tab lists all the hosts scanned, the Vulnerabilities tab lists any vulnerabilities that were detected, and the Compliance tab lists the results of the policy compliance audit. Drill into the results in all three tabs for more detailed information. Advanced filters will apply to all tabs and be sustained until cleared. Filters will not apply if the scan being viewed is still running.
Compliance results
Results under the Compliance tab of a scan are related to the audit file(s) you chose during the scan configuration. Compliance results use three severity levels to indicate the outcome of that particular check:
- Failed severity checks are indicated in red.
- Warning severity uses orange and indicates that manual verification is needed to determine whether the check passed or failed.
- Passed severity results are in green, indicating that the check passed.
Clicking on any of the results will provide you with detailed information about that check, including a description, solution, and output that includes a list of impacted hosts.
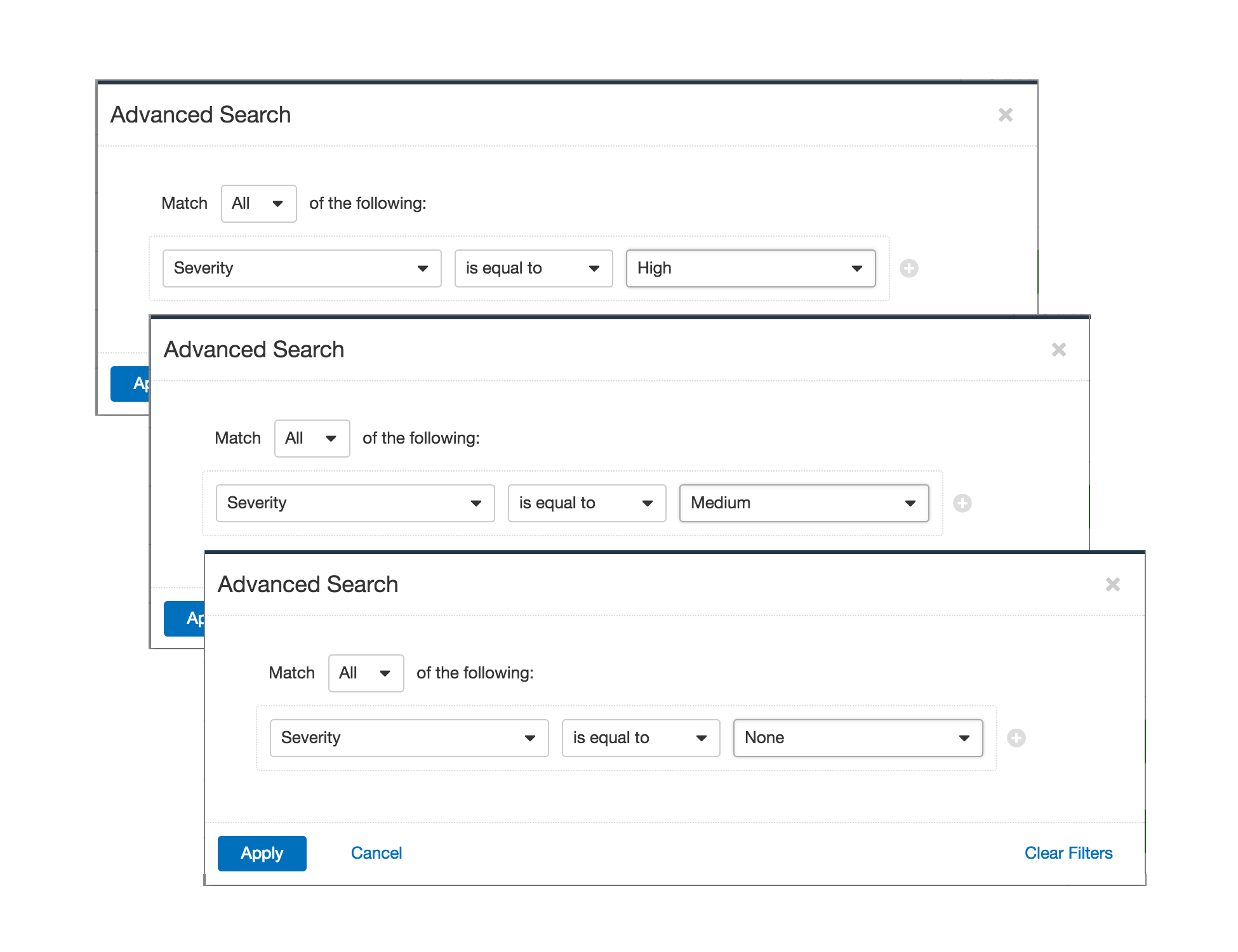
Advanced filters
In the scan results, advanced filters identify results of particular concern. To focus on failed compliance checks, apply an advanced filter using Severity is equal to High. To filter for compliance checks requiring manual verification, set the severity filter to Medium. Set the severity filter to None to filter for passed compliance checks.
Scoring a win
The 2017 Verizon Data Breach Investigations Report details how privilege misuse and unauthorized access is a growing problem for all organizations, and such compromises can lay dormant for months. In order to dominate the line of scrimmage and not be blind-sided, defending your network is the name of the game. Hardening your access and authorization policies and systems can help block rogue insiders and protect your most valuable data. With Tenable.io on your team, you can carry the ball and defend your endzone.
For more information
Interesting in learning more about Tenable.io?
- Visit the Tenable.io area of our website
- Start a free Tenable.io Vulnerability Management trial
More about the 2017 Verizon DBIR: