Most of us are likely very familiar with vulnerability management. Unfortunately, familiarity with vulnerability management doesn’t necessarily equate to mastery. According to a survey sponsored by Tenable and the Center for Internet Security (CIS) in late 2016, about half of the surveyed organizations need to significantly improve their vulnerability management practice. The following data tell the story:
- Only 56% use automated tools to perform any type of vulnerability scanning.
- Only 51% use automated tools to scan all network systems for vulnerabilities on at least a weekly basis.
- Only 36% verify that important vulnerabilities with available patches were addressed within two weeks.
Note: The CIS Controls were formerly known as the Center for Internet Security Critical Security Controls (CSC).
The fourth of the five CIS Controls (CSC), Continuous Vulnerability Assessment and Remediation, is described as:
continuously acquiring, assessing and taking action on new information in order to identify vulnerabilities, remediate and minimize the window of opportunity for hackers.
CSC 4 includes eight sub-controls that will help you improve your vulnerability management program. Here is an overview of several sub-controls.
Run automated vulnerability scans against all systems at least weekly and deliver a prioritized vulnerability list to system administrators (see CIS Control 4.1). As the above survey data shows, only about half of organizations scan all systems weekly. If yours is not yet scanning weekly, it may be relatively easy for your security team to begin scanning more frequently. However, if you don’t significantly pare down your list of vulnerabilities to those that are most important, you can easily bury your IT operations colleagues and deter them from taking action on your vulnerability reports. As an example, you can pare down your list by including only critical and high vulnerabilities that have an exploit available.
Perform vulnerability scanning in authenticated mode or with agents (see CIS Control 4.3). External, non-authenticated scanning only provides a surface picture. You need to assess your systems from the inside out to identify OS and application/service vulnerabilities.
Subscribe to vulnerability intelligence services (see CIS Control 4.4). First, you need to ensure that your vulnerability scanning tool is regularly updated with all relevant important vulnerabilities. Second, if one is available, you should join an industry-specific threat intelligence service to identify the threats that target organizations like yours. This intelligence should help you identify vulnerabilities that require prompt remediation.
Deploy automated patch management tools (see CIS Control 4.5). Realistically, automation is the only way to remediate the majority of high-priority vulnerabilities. This certainly applies to servers and desktops running popular operating systems and popular applications. You may need to apply manual patches or implement compensating controls for some systems, but this should be the exception.
Verify that vulnerabilities were addressed (see CIS Control 4.7). It is not enough to throw a prioritized vulnerability list over the wall to your operations colleagues. You need to work with them to measure the results using a closed-loop vulnerability management process. Jointly develop reasonable goals to establish some quick wins and measure progress over time as you continuously improve.
Establish a process to risk-rate vulnerabilities (see CIS Control 4.8). This sub-control is an expansion of CSC 4.1, which includes basic prioritization. Here, the recommendation is to incorporate risk-based prioritization with the addition of knowledge about the assets you need to protect. Identify the assets with the lowest risk tolerance and remediate those first. You may also want to scan these assets more frequently.
Familiarity with vulnerability management doesn’t necessarily equate to mastery
Tenable can help
It should not be surprising that Tenable knows vulnerability management. However, you may not know that we have tailored a SecurityCenter Continuous View® dashboard and an Assurance Report Card® specifically for CIS Control 4. Both are templates that you can readily adapt to your specific requirements.
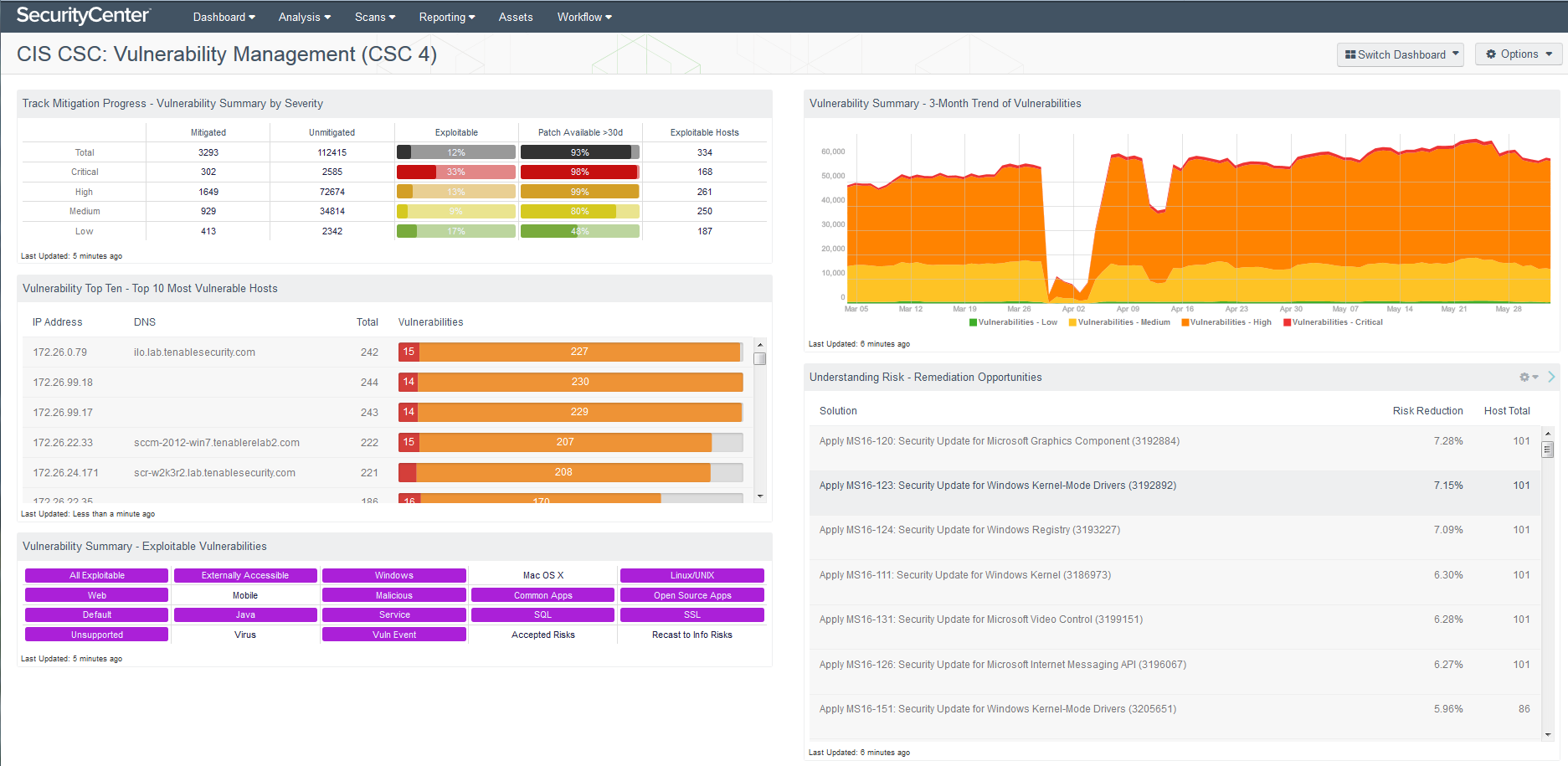
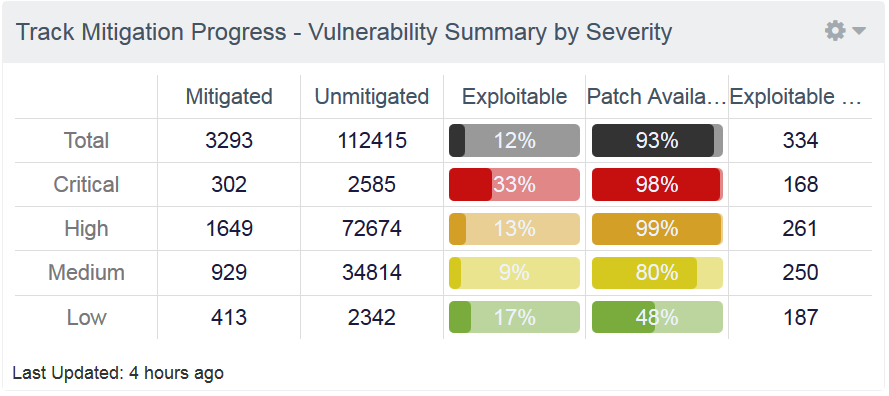
The CIS Vulnerability Management dashboard provides a clear picture of your vulnerability management status
The Track Mitigation Progress component in the upper left of the CIS CSC: Vulnerability Management (CSC 4) dashboard is especially useful. You can scope it to specific assets to track the mitigation status of the top exploitable hosts based on vulnerability criticality, exploitability and how long a patch has been available.
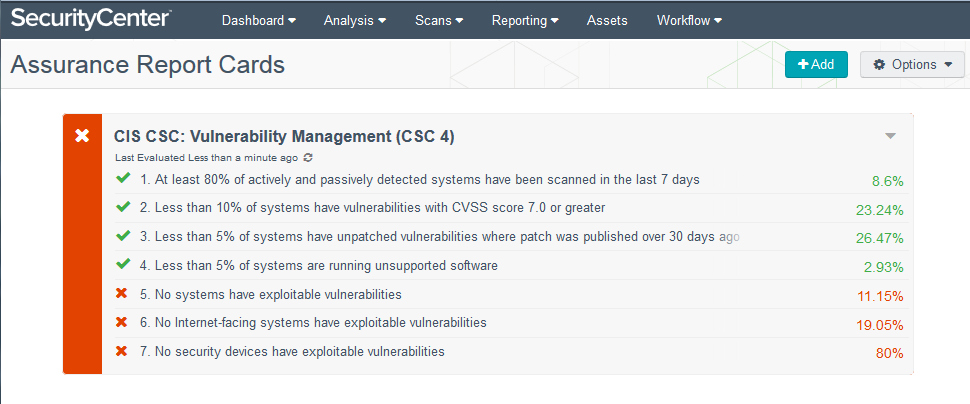
You can use the CIS CSC Vulnerability Management Assurance Report Card during monthly meetings with IT operations staff to jointly manage a closed-loop vulnerability management process. As your program matures, you can increase the thresholds to drive additional improvement.
The CIS CSC: Vulnerability Management ARC helps you communicate status to IT leadership
Learn more
During an upcoming Tenable webinar on June 28, Brian Ventura, a SANS Community Instructor, will dive into the details of each of the sub-controls and show you how Tenable supports CIS Control 4. We will also reserve time for questions and answers.
Even if you can’t attend, please register so we can send you a link to the recorded webinar to watch at your convenience.
Watch for my final blog in this series on Foundational Cyber Hygiene controls; CIS Control 5 is all about controlled use of administrative privileges.