
Over the past several years, Tenable has discussed the growing concerns around Internet of Things (IoT) security. With the static nature of IoT devices such as cameras, door sensors, and many more, the ability to correct flaws in third-party libraries becomes increasingly difficult. Yesterday, the researchers at Senrio discovered a serious flaw in the gSOAP library found in many IoT devices, such as the AXIS M3004. Tenable.io and SecurityCenter use active and passive detection methods to identify these vulnerable systems by enumerating the operating systems and detecting versions of vulnerable third-party libraries.
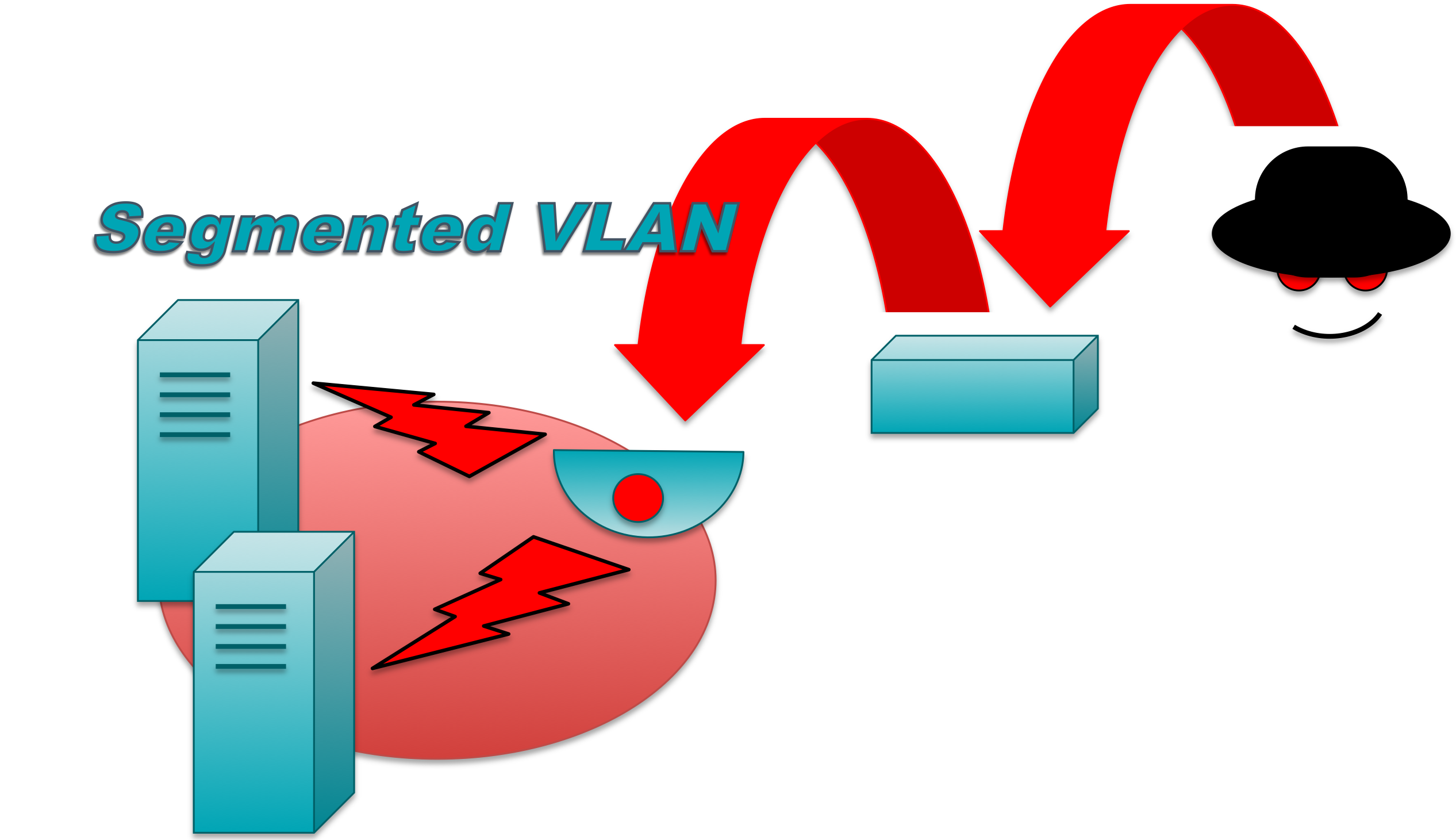
Many manufacturers recommend customers or installers use segmentation strategies when deploying IoT devices to address potential security vulnerabilities. While segmentation is a good plan when deployed correctly, often the installer and IT organizations do not fully test access control methods. For example, the IoT device might be placed in separate Virtual Local Area Networks (VLAN), but the Access Control Lists (ACL) are not fully implemented and tested. I often ran into these issues when performing security assessments and pen-tests. I would go into a network as a normal user and use Nessus to discover all of the live devices on the network. After stumbling onto Industrial Controls Systems (ICS), IP phones, and other devices that are not heavily monitored, I would then clone a MAC address or use some other method to change VLANs and begin to attack the network as if I were an IP Camera. If ACLs were properly implemented, I would quickly find I had no access, but that was seldom the case. Instead, I often found I had more access from the “Segmented VLAN”. This example illustrates why the Devil’s Ivy vulnerability is so dangerous.
Vulnerability Detection
The vulnerability discovered within the gSOAP library is a classic buffer overflow, which allows the attacker to execute arbitrary code. Tenable’s research team developed a new Nessus plugin to detect the affected devices by extracting the banners from services such as FTP and SNMP. The Nessus Network Monitor uses plugins to detect AXIS using FTP and SMTP traffic traversing the network.
- AXIS Camera Detection via FTP (9681)
- AXIS Camera Detection via SNMP (9683)
Tenable.io Vulnerability Management and Nessus will use Plugin 101810 “AXIS Camera gSOAP Message Handling RCE (ACV-116267) (Devil's Ivy)” to identify the vulnerable AXIS systems. The plugin relies banners from FTP and SNMP services running on the Axis cameras. In certain cases the plugin can also extract the version based by querying ‘param.cgi’ file device on the system. Tenable.io Container Security also detects vulnerable third-party libraries, such as gSOAP, embedded within containerized application workloads.
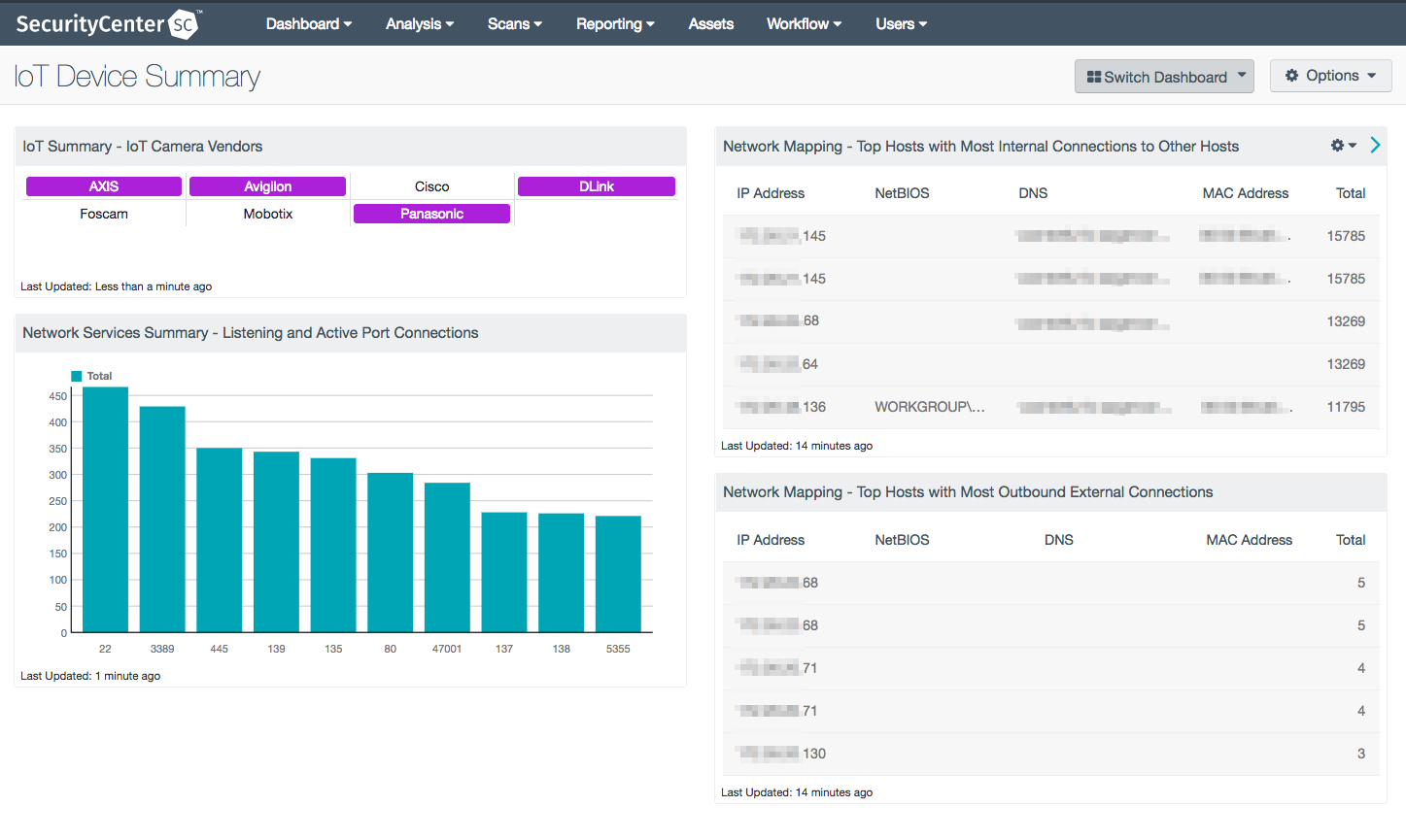
IoT & AXIS Dashboard
The IoT Device Summary dashboard, available via the SecurityCenter Feed, leverages data from the Tenable sensors to offer insight into IoT-related activity on your network. By adding a subnet, IP address, or asset filter to the components in this dashboard, you can tailor the results to focus on your IoT devices. The dashboard allows you to track IoT device network connections as well as detect IoT cameras by ONVIF-compliant vendor.
Attack Vector
Do not underestimate the seriousness of this vulnerability.
Physical security companies that install and rely on these vulnerable cameras are at potential risk. If the installers fail to apply this patch or fail to secure the VLANs, cyber criminals can use the camera systems to assist in physical compromises. Once the camera systems are compromised, adversaries can reset all of the cameras or load their own version of the operating system. At that point, they have full control over the cameras, which can have serious consequences, including disabling the camera or deleting any captured evidence.
Wrap-Up
Many vulnerabilities can cause a loss to business processes or cause employees to recreate data; however, this vulnerability is the type that often gets easily (mistakenly) dismissed. Vendors often say, “We have a firewall,” and ignore the risks. Devil’s Ivy will be with us for some time as IoT systems are not easily patched.
To prevent this vulnerability from causing damage or revenue loss, Tenable recommends you properly segment your IoT networks using tightly controlled ACLs and to quickly deploy any patches related to Devil’s Ivy vulnerabilities.
For more information
- Learn more about Tenable.io, the first cloud-based vulnerability management platform built for today’s modern assets
- Start a free 60-day trial of Tenable.io
Many thanks to the Tenable research team for their contributions to this blog