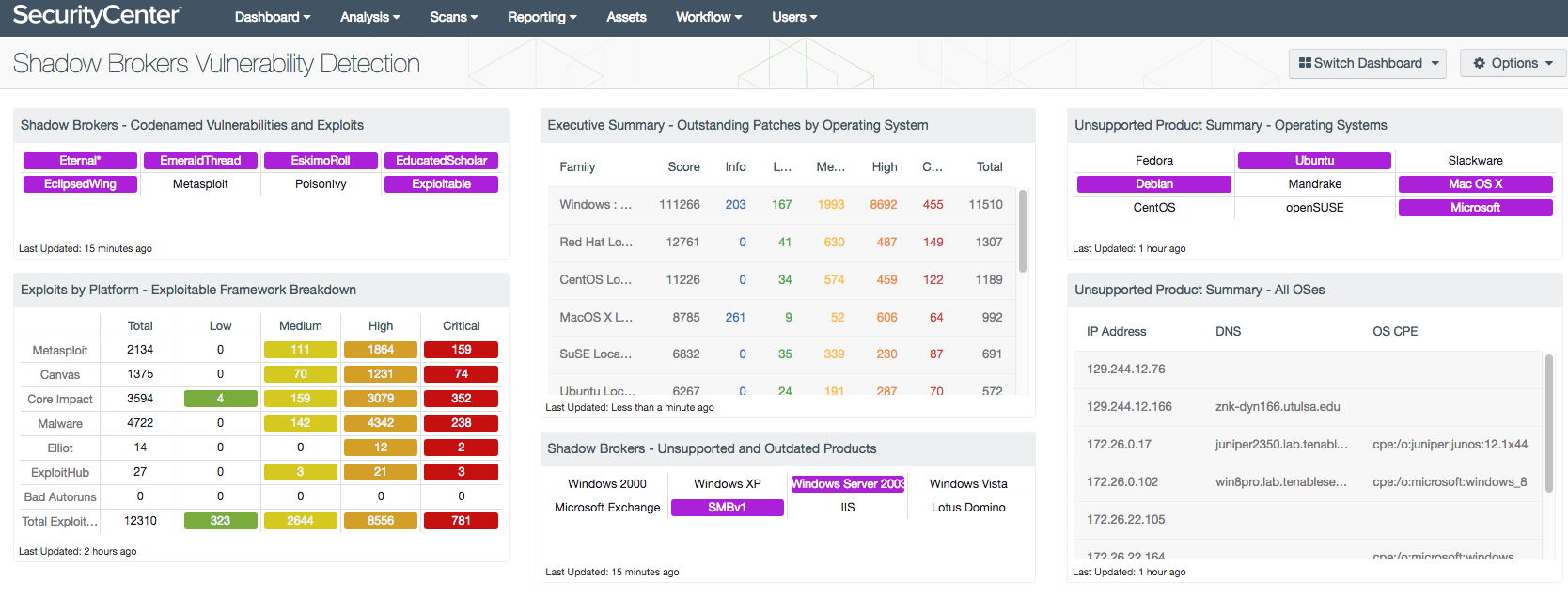
The current IT landscape has fundamentally changed the way that organizations view their security and assess their overall risk posture. Technologies like cloud, DevOps deployments and containers behave in a radically different way than traditional assets. For example, they are often shorter lived or they often have owners outside of the IT department. If threats and vulnerabilities aren’t detected on these assets, these differences can lead to security gaps, and these gaps can provide bad actors with a host of new opportunities. With that in mind, Tenable recently commissioned a report from IDC to examine how leveraging the cloud could help with modern security challenges.
Technology Spotlight
This IDC Technology Spotlight, Leveraging the Cloud to Achieve Comprehensive Asset Visibility, Tracking and Security, examines how the evolution of vulnerability management has left organizations with an even greater need for visibility into their assets and vulnerabilities, especially in new asset types like containers. Ayoub also delves into the advantages that can be experienced by organizations that use a cloud-based approach to vulnerability management.
According to IDC, the cloud-hosted security services market is growing rapidly, with vulnerability management being the fastest growing sub-segment. This rise in adoption of cloud-hosted security services is due to several benefits organizations can expect, including:
- Broad asset coverage, which delivers comprehensive visibility into all assets
- Integrated user experience, helping to improve productivity
- Simplified integrations to improve visibility and efficiency
- Elasticity, allowing organizations to scale as required
The cloud-hosted security services market is growing rapidly
Although cloud solutions can offer significant price and performance advantages, real or perceived data security concerns have deterred organizations from shifting their resources to the cloud in the past. However, those concerns seem to have dissipated somewhat; IDC projected 17.2 percent growth for the cloud-hosted Security and Vulnerability Management (SVM) market from 2014 to 2019.
One of the reasons for this change is the projected cybersecurity workforce shortage
One of the reasons for this change is the projected cybersecurity workforce shortage. Small, medium and large sized organizations alike, may look to shift their resources to the cloud to benefit not just from cost-savings, but for greater productivity achieved by security professionals who no longer have to manage the application itself when they move to a SaaS option. Rather than hiring the workforce to maintain on-premises security products, those resources can focus on actually using applications to address security challenges.
There’s also an increasing need to protect resources across all form factors, including physical, virtual, public cloud, containers, etc.
Tenable.io
Tenable has been working with many customers who are encountering similar challenges as reported by IDC, including how to account for modern assets like cloud, containers and mobile in their vulnerability management programs.
Tenable.io is a modern vulnerability management platform that provides the visibility and insight to protect what matters most
To address these challenges, Tenable recently announced the debut of Tenable.io. Tenable.io™ is a modern vulnerability management platform that provides the visibility and insight to protect what matters most to an organization. It delivers a fresh, asset-based approach that accurately tracks resources while accommodating dynamic assets like cloud and containers. Its streamlined and intuitive user experience, including pre-built templates and a consistent user interface, delivers value quickly and helps teams accomplish more.
With Tenable.io, customers benefit from an elastic licensing approach based on assets instead of IP addresses, making it easier to custom fit a vulnerability management solution to each unique environment. This approach makes it easy to accurately identify, track and license all of the assets in a given environment, without double counting, and eliminates the challenges associated with licensing mobile devices, public cloud instances, and short-lived virtual machines.
A fully documented API and integrated SDK help automate the sharing of Tenable.io capabilities and vulnerability data, and allow organizations to build on the Tenable.io platform. Pre-built integrations for patch management, credential management, mobile device management and other solutions make it easy for admins to leverage their existing investments.
For additional information, please download the full Technology Spotlight from the Tenable website.
Sources
IDC Technology Spotlight: Leveraging the Cloud to Achieve Comprehensive Asset Visibility, Tracking, and Security