Clik here to view.
With the adoption of more cloud, mobile, IoT, and SaaS solutions, organizations need an effective way to understand, manage and reduce their cyber risk. Many organizations rely on patch management systems to automate the installation of patches across the network. When configuring these systems, many employ the "set it and forget it" method and assume all of their systems are being patched. This method often results in the patch management system reporting inaccurate information. Using Tenable.io, you can quickly audit patch management solutions and gain complete visibility into your Cyber Exposure at any given time.
Issues such as missing systems, patch installation failures, communication issues with managed host agents, and hosts needing to be rebooted can all increase your organization’s overall cyber risk. One of these supported solutions, IBM BigFix (formerly IBM Endpoint Manager), is a management platform designed to manage and patch large groups of systems and devices within organizations.
Setting up Scans
Before running any scan, you will need to add a custom analysis file on your BigFix server. Tenable.io uses this file to retrieve detailed package information by leveraging the BigFix Server API. For more information on how to set up the file, please visit IBM Tivoli Endpoint Manager (TEM) section within the Tenable.io Patch Management page.
Once your custom analysis file has been created and added to your BigFix server, you can create your scan by selecting the Advanced Scan template within Tenable.io. Under the Credentials tab, click on Patch Management, then select the IBM Tivoli Endpoint Manager (BigFix) option. Enter the IP address of your server along with an administrative account that has access to your BigFix server.
Image may be NSFW.Clik here to view.

When creating your scan, Tenable.io only requires credentials from your patch management server, eliminating the need to add local credentials for your managed hosts. This option is useful for larger organizations where credentials for managed hosts may not be available. Vulnerability data is collected from the selected patch management solution, and will return a list of outstanding patches that you need to install.
To get a complete look at your patch management solution, we recommend adding credentials for your managed hosts. Nessus will scan each individual host and compare the information being reported by your patch management solution.
Image may be NSFW.Clik here to view.

To audit your BigFix server, there are several plugins that need to be enabled within your scan to obtain results. Additionally, you will also need to enable the Windows : Microsoft Bulletins Plugin family.
Required IBM BigFix Plugins
- Patch Management: Tivoli Endpoint Manager Computer Info Initialization (Plugin ID 62559)
- Patch Management: Missing updates from Tivoli Endpoint Manager (Plugin ID 62560)
- Patch Management: IBM Tivoli Endpoint Manager Server Settings (Plugin ID 62558)
- Patch Management: Tivoli Endpoint Manager Report (Plugin ID 62561)
- Patch Management: Tivoli Endpoint Manager Get Installed Packages (Plugin ID 65703)
- Windows : Microsoft Bulletins Plugin family
If you have added credentials for your managed hosts into your scan, using the Patch Management Windows Auditing Conflicts plugin will help you quickly detect any patch conflicts being reported. The Patch Report plugin will report on vulnerabilities from third-party software that may not be covered by your existing patch management solution. Enabling the optional plugins will provide valuable information on client versions deployed within your network.
Recommended Plugins
- Patch Management Windows Auditing Conflicts (Plugin ID 64294)
- Patch Management Auditing Satisfied (Plugin ID 64295)
- Patch Report (Plugin ID 66334)
Once you have selected the appropriate plugins, your output should look similar to the screenshot below.
Image may be NSFW.Clik here to view.

Results
The patch management feature within Tenable.io enables you to collect information on missing patches reported by patch management solutions. Scan results will include a summary of Windows Bulletins collected from your patch management solution, along with any additional plugins selected.
Image may be NSFW.Clik here to view.

Vulnerabilities detected by your patch management solution include a report on the affected hosts and whether the system is vulnerable. Using this information will help to ensure that your BigFix server is configured properly and providing accurate information.
Image may be NSFW.Clik here to view.

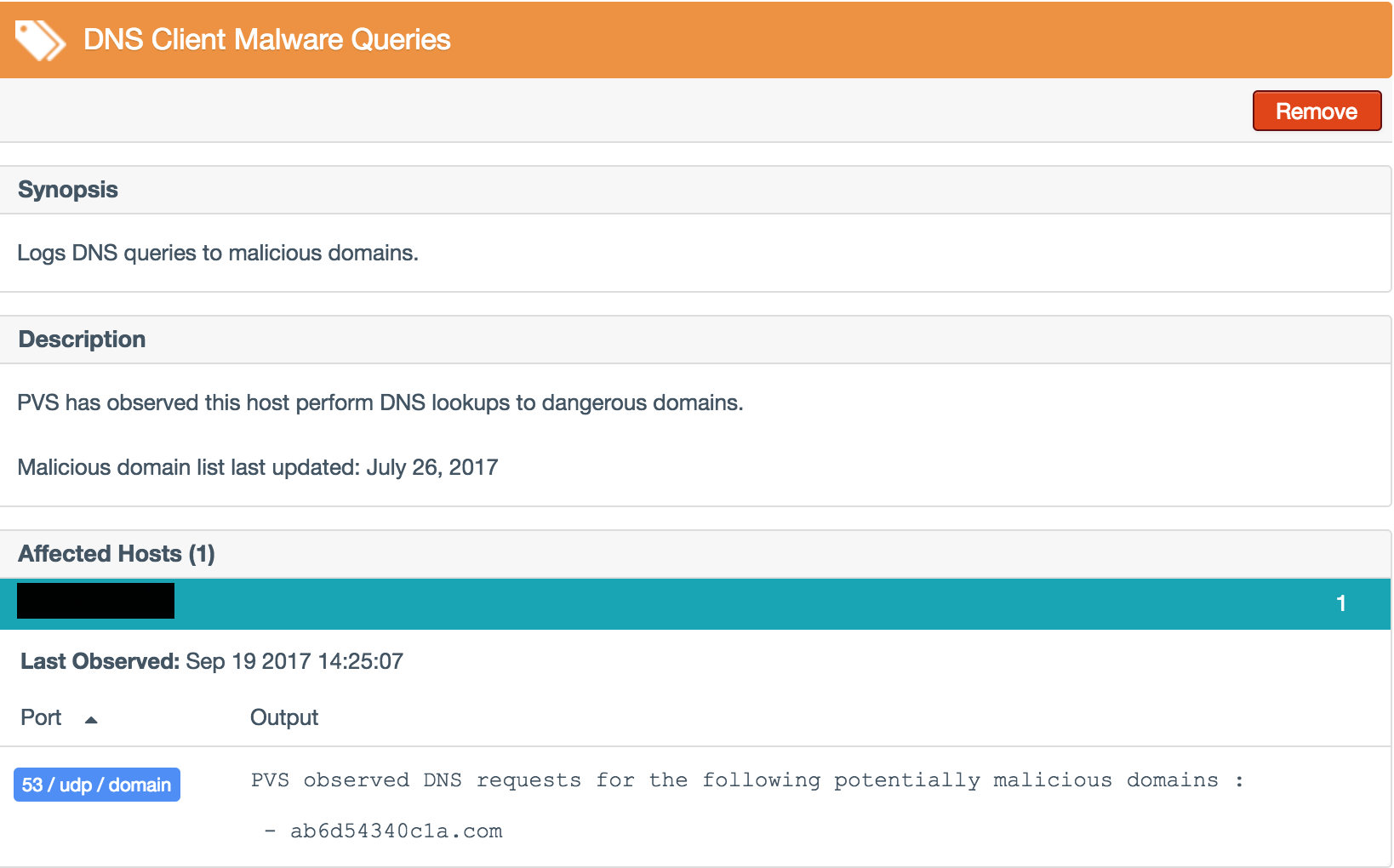
Results from the Patch Management: Tivoli Endpoint Manager Report (Plugin ID 62561) plugin will include a report on the status of managed hosts, last check-in timestamp, operating system version, missing patches reported and any hosts that are up to date. Because IBM BigFix supported multiple platforms, results using this plugin will include missing patch information supported platforms such as Windows, Linux, Solaris, AIX, and Mac OS.
Image may be NSFW.Clik here to view.

This information will help you detect potential communication issues between the client and server, as well as any systems that may have fallen out of scope.
Conflicts
Using credentialed scans along with the Patch Management Windows Auditing Conflicts (Plugin ID 64294) plugin will report on any conflicts between Nessus and your patch management solution. If any conflicts are discovered, the plugin will use a “High” severity rating, and include a summary of the Microsoft Bulletins found.
Nessus uses the credentials provided within your scan to login to each managed host and compare the current patch level status. These results are compared to patch levels collected from BigFix by Nessus as indicated by “IBM TEM” conflicts.
Image may be NSFW.Clik here to view.

The report for each patch and the discrepancies are displayed in the plugin output. Conflicts like this may indicate that the host was not targeted for deployment of a particular patch, so the BigFix server does not detect it as missing.
The below example shows that BigFix is reporting the MS15-060 patch missing, however Nessus is reporting the system as not vulnerable. In this instance, BigFix may be reporting outdated or inaccurate data that should be addressed immediately by your security team.
Image may be NSFW.Clik here to view.

Using this data helps to underscore the importance of cross-referencing patches between what is on the system and what the BigFix server thinks is on the system.
Wrap Up
Using patch management integrations within Tenable.io helps you monitor patch cycles, improve remediation efforts and strengthen your overall security posture. This Cyber Exposure data can be used by security teams to effectively identify and resolve issues. CISOs can also use this information to better articulate the organization’s level of exposure and risk to C-level executives and the board.
Built on industry-leading Nessus technology from Tenable, Tenable.io delivers a modern approach that manages, measures and reduces the modern attack surface to accurately understand and reduce cyber risk. Start with your free 60-day trial of Tenable.io Vulnerability Management to measure your Cyber Exposure.
Want to learn more?
- Check out the IBM Patch Management Overview dashboard.
- Continue the patch management conversation in the Tenable Community.
Clik here to view.