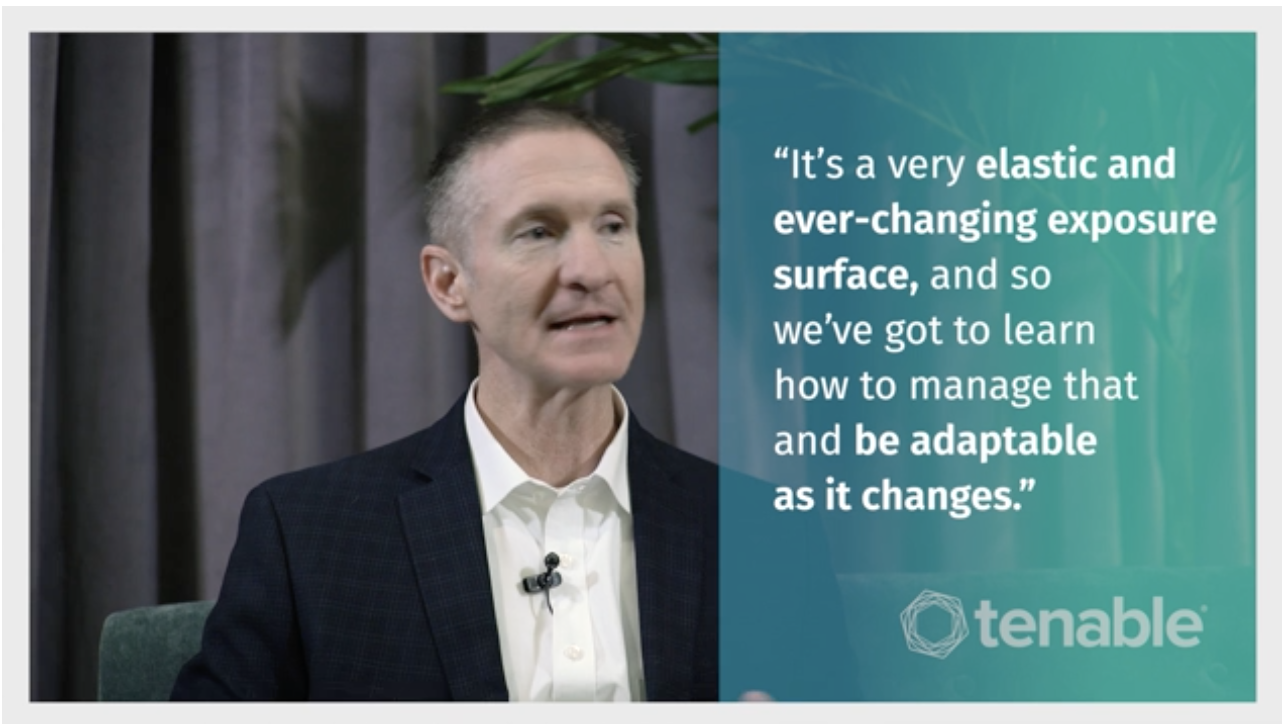
Protecting air-gapped networks from insider threat is a priority for the Lockheed Martin Aeronautics information systems security risk team. Here’s how they’re using Tenable.sc to keep the F-35 fighter jet secure.
Headquartered in Bethesda, MD, Lockheed Martin is a global security and aerospace company employing approximately 105,000 people worldwide. The organization is principally engaged in the research, design, development, manufacture, integration and sustainment of advanced technology systems, products and services.
Stephen Nevil, Senior Information Systems Security Risk Analyst with Lockheed Martin Aeronautics in Fort Worth, TX, performs compliance and vulnerability management for the company’s F-35 aircraft program. According to Lockheed Martin, the F-35 is the most lethal, survivable and connected fighter aircraft ever built. More than a fighter jet, the F-35’s ability to collect, analyze and share data enhances all airborne, surface and ground-based assets in the battlespace, enabling men and women in uniform to execute their mission and come home safe.
Nevil’s biggest challenge is securing six air-gapped networks, many of which are classified. “With...air-gapped networks, really, what are we concerned about?,” said Nevil in an interview with Tenable during the Edge 2019 user conference. “We're concerned about insider threats. And we're concerned about people taking data off our networks unauthorized, either bringing it on or taking it off. And so, you need to be able to identify that efficiently.”
Visit https://www.tenable.com/edge to watch keynotes and breakout sessions from the Tenable Edge 2019 user conference.
The organization has been using Tenable.sc (formerly SecurityCenter) for about two-and-a-half-years. “It's fantastic seeing those tools develop and help us see what's happening on our networks,” said Nevil. “[It’s] been pretty incredible.”
The organization uses the data provided in Tenable.sc in a variety of ways to communicate with key stakeholders, including the Information Security Officers who manage the six air-gapped networks, the admins who are responsible for patch management and the senior executives who oversee cybersecurity spending decisions.
“There is a mountain of data you can get,” said Nevil. “You can get anything you want. I see about 826 different types of normalized logs every day, and what we had to do was focus on what is important, what's going to make us reach our goal of making sure we don't have insider threats, we don't have data coming on or coming off our network and that we're meeting the government standards.”
Sharing Data with Information Security Officers
Each of the six networks Nevil oversees has its own Information Security Officer with whom he is able to share data via Tenable.sc. “With [Tenable.sc], we have a single pane of glass where I can have my vulnerability data on there, I can have my compliance data and I can have my audit data and we review [it] all there, with just several dashboards. It's made the efficiency just skyrocket.”
When efficiencies skyrocket, the natural next question is: what are you doing with all the newfound time? The efficiencies made possible through Tenable.sc are enabling Nevil and his team to devote more time to analyzing the networks. “Previously, we couldn't do it effectively,” said Nevil. “This tool has just made it a leap for us to actually spend the time and dedicate it to actually understanding what's happening, what vulnerabilities we need to attack, what compliances we need to meet and what's happening on our network.”
The ability to understand what’s happening on the network “opened our eyes to all the stuff that we could be doing better,” said Nevil. Oftentimes, the data revealed that simple processes weren’t being followed or could be improved. For example, if someone generated a local user account to do testing and then forgot to delete it, “it's right there in your vulnerability scans,” said Nevil. “And you're like, ‘hey, you forgot to delete this test account that you made,’ and you can tell the admin to go fix it. So, it's fantastic.”
Helping Patch Admins to Prioritize
Tenable.sc has also helped Nevil and his team identify their priorities. “How do you eat an elephant?,” said Nevil. “One bite at a time. So, that's what we did. We took chunks of data and made it usable and attacked it.”
To help patch management admins, for example, Nevil’s team uses Tenable.sc to do automated scans and produce reports. “It runs a scan and on Monday morning, my admins have a report in their inbox that says, ‘hey, here's the top 10 vulnerabilities that I want you attack. Here's the top 10 dirtiest machines. Here's the top 10 oldest vulnerabilities I want you to attack and here are machines that aren't meeting compliance.’ So, they have just a couple things to hit, but if they hit those top 10 things, you know, that week, it's going to lower our vulnerabilities quite a bit.”
Tenable’s new Vulnerability Priority Rating (VPR) is designed to further refine the risk assessment and remediation processes. VPR, a new capability introduced this year in Tenable.sc and Tenable.io, is the output of Tenable’s new Predictive Prioritization offering. Introduced in February 2019, Predictive Prioritization combines Tenable-collected vulnerability data with third-party vulnerability and threat intelligence and analyzes them together using an advanced data science algorithm developed by Tenable Research. The data analysis is used to develop a VPR for each vulnerability.
“Anything that Security Center can do to help us prioritize more effectively is going to be incredibly useful,” said Nevil. “You don't have enough time to hit everything. It's just impossible. And we want to do better because we have the F-35 aircraft in our inventory. Our goal is to make it as secure as possible because the value of that aircraft drops dramatically if it's compromised. And we're not going to let that happen.”
Showing Executives the Value of Cybersecurity
Tenable.sc has also been valuable in giving Nevil’s senior managers data they can use to communicate with the organization’s executives about the value of cybersecurity spending. The tool makes it easy to build dynamic executive dashboards, which provide valuable context for decision-makers.
“[In cybersecurity] we consume resources, versus generating profit margin for Lockheed Martin.” said Nevil. “That's why it's so important that we can use this technology and we can have a secure network. We can show our management...even though we don't generate money, we're saving you tons of money in the end because if you lose all your profit margins because someone compromised us, you're starting over again.”
Watch Now:
Tenable interviews Stephen Nevil, Senior Information Systems Security Risk Analyst with Lockheed Martin Aeronautics, at our Edge 2019 user conference:
![]()
Learn More:
- Visit our Predictive Prioritization webpage here.
- Learn more about Tenable.sc here.