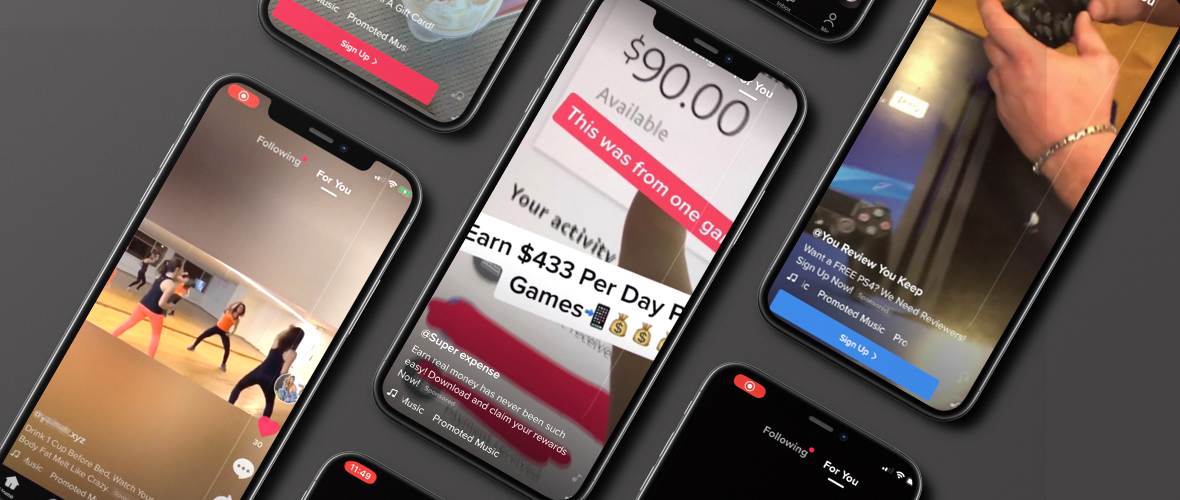
TikTok’s popular “#ForYou” page has become a habitat for scammers peddling fake mobile applications, diet pills, drop-shipped goods, fake gift cards and more.
The fate of TikTok’s operations in the U.S., Australia and New Zealand has been a topic of international interest for the past several weeks. Tech giant Microsoft and retail giant Walmart are weighing a joint bid to acquire the businesses and Oracle is also reportedly considering throwing its hat in the ring. However, legal and regulatory challenges are making an already complex negotiation process even more challenging. Even if these considerable hurdles are surmounted, my research over the past seven months reveals some additional challenges a new owner might face in moderating activity on the popular video sharing app. What I found confirms my suspicions that TikTok truly is the Wild West of social media.
The platform raises myriad concerns for a prospective U.S. owner. With a third of its users aged 14 and younger, it’s ripe for exploitation of minors. In addition, we’re already seeing attempts to use the platform to spread misinformation and disinformation related to the U.S. presidential election in November. For the scope of my research, however, I’ve chosen to focus on a plethora of advertising-related scams. Combating these will require any new owner to make a significant investment in beefing up the site’s moderators and implementing new standards and practices to avoid damage to the brand.
TikTok, which is currently owned by Chinese firm ByteDance, has had a monster 2020 so far, setting a record for the most downloads in a single quarter. Children aged four to 14 in the United States, United Kingdom and Spain now spend an average of 80 minutes per day using the app, putting it on par with YouTube. An April report from SensorTower, a mobile app market intelligence firm, found that TikTok has surpassed two billion downloads globally this year.![]()
Source:SensorTower
In 2019, my research into TikTok revealed how popular apps and services have become havens for scammers and how the pursuit of social currency on the network helps fuel an economy for impersonation accounts and services promoting free followers and likes.
Four Types of TikTok Ad Scams
Since early 2020, I’ve been observing how scammers are stepping up their game by pivoting from simply creating accounts on TikTok to exploiting its advertising channels. My research has identified four primary types of TikTok advertisements that are scamming users out of time, money and personally identifiable information:
- Easy money offers. These offers claim to help users earn money by downloading applications that are either deceitful or questionable in nature, including a series of iMoney applications. These advertisements are problematic because they promote fake apps, lure users into potential pyramid schemes, request personally identifiable information such as driver’s licenses and, in extreme cases, encourage users to install mobile device management (MDM) tools which could potentially compromise their devices.
- "Free” offers that come with a price. These scams offer everything from free diet pills and “performance enhancers” to video games, headsets and gift cards. They are problematic because they use fake celebrity endorsements and fake news articles to dupe users into providing credit card details in exchange for “free” goods, subjecting unsuspecting users to recurring subscription fees or other types of unreimbursed charges.
- Dropshipping schemes involving price gouging and questionable goods. These ad scams typically are used to promote questionable or extremely overpriced goods offered by dropshipping. While dropshipping itself isn’t necessarily a scam, these offers are problematic when they involve price gouging, counterfeit or questionable goods, or duping buyers into paying for goods they never receive.
- Dodgy credit repair and tuition assistance offers. These ad scams prey on those who may be in dire financial straits by promising to repair credit card history or by promoting online classes as a way to access financial aid that they could apply for directly on their own. In many cases, these ads are merely a ruse to entice users to pay for bogus services or share their personally identifiable information.
Just as advertising on Facebook, Instagram and Twitter has created a niche for digital marketing, so, too, has TikTok’s advertising platform enabled advertisers to target its 800 million monthly active users — and scammers are rushing to take advantage of the platform’s scope and reach.
![]()
Source:We Are Social
The two types of TikTok feeds
Understanding the significance of the advertising scam trend requires a basic grasp of the TikTok user experience. There are two areas of the application to which I’d like to draw your attention: the Following page and the For You page.
As its name implies, the Following page contains a feed of videos from the TikTokers a user is currently following.
![]()
Example of Following page, featuring TikTok creators Addison Rae and The Cheeky Boyos
The For You page is populated with videos curated for each user based on TikTok’s algorithm. The algorithm takes into consideration several factors, such as how users interact with TikTok, including videos they’ve liked in the past or creators they follow. Because it’s algorithmically generated, the For You page presents a greater opportunity than the Following page for advertisers to break through to users based on their interests.
![]()
Example of the For You page, featuring recommended videos from the TikTok algorithm
Everyone wants a piece of the For You page
TikTok creators hoping to grow their audience try to find ways to organically appear on the For You page but cracking this code has been difficult over the last year. One of the earliest attempts to make it on this page was to include the hashtags “#foryou” and “#fyp” as part of a video’s captions.
Naturally, scammers have also been trying to crack the same code. Some have had relative success, as I outlined in my first blog on TikTok scams in August 2019.
TikTok ads can only be seen on the For You page
One key part of the TikTok experience is that, when users browse their Following page, they won’t see any advertisements. However, when they browse their For You page, they will see an assortment of advertisements. TikTok provides some examples of successful ad campaigns that have launched on the platform.
![]()
Example of legitimate advertisements that appear on TikTok’s “For You” page
The above examples show standard in-app advertisements promoting the Apple TV+ service and Experian’s mobile application. Advertisers can also leverage branded hashtags to further promote their goods and services.
TikTok ads: gateway to the For You page
Brands and scammers alike have the option of purchasing advertising space that will appear on users’ For You pages. While ad rates may vary, TikTok promotions include a one-time $300 ad credit along with a matching top-up credit of up to $2,000, meaning if you purchase $2,000 worth of advertising, TikTok will match it by giving you an additional $2,000 for a total of $4,000 in ad credits.
![]()
Details from the TikTok For Business page about a promotional ad credit given to advertisers
We have no way to identify whether the scammers are taking advantage of this credit, but it definitely incentivizes them to utilize TikTok’s ad platform for their own benefit.
A closer look at the four ways scammers are exploiting the TikTok ad network
As noted earlier, my research reveals four primary ways scammers are taking advantage of advertising on For You pages.
1. Easy money offers using questionable and deceitful applications
One of the shadiest tactics I’ve encountered is the use of TikTok ads claiming to offer users money in exchange for “completing tasks” such as downloading a variety of real applications from the App Store and running them for three minutes. Considering TikTok’s popularity among children and teenagers, who typically have little to no disposable income, these advertisements are the perfect disguise for scammers to exploit TikTok’s young user base.
Tricking users into downloading mobile applications is an old tactic used by scammers as part of the “human verification” process, which I’ve written about in my Cash App research. What makes this tactic on TikTok different is that the scammers aren’t taking the “human verification” approach. Instead, they’re using TikTok to promote a series of applications called “iMoney” by using false advertising in two different ways. First, they claim users can earn a high dollar amount for simply downloading mobile applications. Second,they mask the actual application contents by uploading them to the App Store under false pretenses.
![]()
Example of a deceptive TikTok ad promoting one of the iMoney applications
These iMoney applications are advertised to TikTok users as ways to earn “$433 Per Day Playing Games,” alongside a screenshot of a PayPal balance screen as “proof.” Other advertisements detail the step-by-step process of how users can “Make Money” easily. The high dollar amount isn’t a true representation of what users can expect to earn just by “playing games,” as my research into these applications will show. While users have the potential to earn money, it’s not a straightforward process, as there are a series of questionable roadblocks before users can allegedly cash in.
When users click on one of these advertisements, they are redirected to Apple’s App Store. There, they are presented with an application masquerading as a completely different app, as shown in the example below. In this case, the TikTok ad references an application called “Super Expense” and its description says it is an app to handle “Simple daily billing expenses, plan your expenses and income” that is designed to help you “understand your financial situation.”
![]()
Super Expense is one of several iMoney applications that were masquerading as other apps in Apple’s App Store
Once a user downloads the application on their iOS device, they are initially prompted with a page that looks just like the one in the App Store. However, after a moment, the screen goes blank and another page appears that asks the user a question: “How To Earn Money?” It then details the instructions: Download an app, open the app, play for three minutes, get money.
![]()
The first few screens that appear when launching the Super Expense app for the first time
Once the user clicks “Start” the true interface is revealed for an application called iMoney.
![]()
iMoney: The hidden interface behind several apps, including Super Expense
There are multiple sections of the application, three of which are highlighted in the images above.
Current Tasks: Earn money for downloading and opening applications
The “Current Tasks” section in the app features a list of 24 applications the user can download to begin earning money. If the user leaves the application open for three minutes, the task is marked complete, which earns the user between $0.18 and $0.23. In total, a user can earn up to $5.02 for completing all 24 tasks.
However, it is unclear when the tasks are refreshed and if a user is only able to complete a certain number of tasks per day. Ironically, one of the tasks includes downloading TikTok. We speculate that when users perform these tasks, they are lining the pockets of the iMoney developers, who are using what’s called an offerwall to promote various apps and pocket an undisclosed sum of money in exchange for getting users to install these apps.
In a private group for the iMoney application, some users have voiced complaints about the inability to cash out their funds. One user noted they have been waiting for “over two months” and now the developers aren’t answering their messages.
![]()
Comment from user in the iMoney Facebook Group about not being able to cash out
Amazon Tasks: Get paid to buy Amazon goods and leave positive reviews
There is also a section of the iMoney application for Amazon Tasks. This section incentivizes users to purchase products from Amazon using their own money. Users are promised a refund of the full value of the goods so long as they keep the product and write a positive review for it.
![]()
Example of the Amazon Tasks section in the iMoney application
The iMoney application gives detailed instructions on how to find these particular products on Amazon, including the search term to use as well as the position of the item on the search page.
![]()
Instructions found in the iMoney app on how to get a refund of the purchased product and the task completion bonus reward
The Amazon Tasks section in iMoney instructs the user to pay for the product and states that the people behind iMoney will “cover the paypal fee and taxes” but that shipping fees are not covered. They ask users to upload a screenshot of their order three hours after it has been placed. They also ask users not to return the goods because Amazon will then “deduct illegal proceeds and blacklist” their account. In the third step, users are instructed to leave a “five star prise [sic]” in the comments section of the product they purchased. In other words, they’re asking for a five-star review. They caution that this review should be left “3 days later after receiving your products” and include an example review.
This tactic appears to skirt Amazon’s requirements that users disclose whether or not a product review was paid for. In addition to receiving reimbursement for the goods purchased, the iMoney application will pay users a small “reward” for completing this task.
Referral section: The real source of income for iMoney users
Finally, the other section worth highlighting is Referrals, where users have the potential to make the most money. This section reveals that iMoney promotes a pyramid or multi-level marketing scheme. For each person you refer to iMoney, you have the potential to earn up to 50% of the reward for the tasks they complete.
![]()
Referral bonus table for the iMoney application
A leaderboard in the app shows how much users have earned from referrals. At the time this research was conducted, the leaderboard showed one user had made $772 from referrals alone in a single month.
![]()
The iMoney Referral leaderboard showing the top earning referrers for the month
While the app promotes itself as a place where users can earn money in exchange for completing simple tasks, in reality the amount that can be earned this way is negligible. The real driving force is the multi-level-marketing type scheme which incentivizes users to invite a faithful group of “downline” and unsuspecting recruits to download the apps and perform tasks, earning the inviter up to a 50% “commission” on the tasks completed by their downline participants. . While it’s not impossible to make some money through these applications, the promises are misleading; it requires a lot of work and the ability to amass a large group of people to join the service, putting into question the time/value investment of these applications.
A thread from the private iMoney Facebook group showed an exchange between a user who claimed to have seen great success in securing referrals and another lamenting that they’ve not had quite the same luck, noting that they’ve snagged only four referrals with only one referral resulting in task completion. The latter portion of that thread is shown below.
![]()
Comment from user in the iMoney Facebook group about not being able to convert referrals
Additional areas of concern in the iMoney application
There are two other areas of concern with the iMoney app. The first is that, after completing a few tasks, the application won’t allow a user to complete any more tasks until they provide some sort of verification.
![]()
The iMoney application asks users to provide proof of verification before they can complete more tasks
The app makers are asking users to take photographs of their driver’s license or “other identity info” and upload them through the iMoney app. They say it’s just used for “identity verification” and that they “promise not to disclose your information.”
![]()
Comment from a user in the iMoney Facebook group about having to share their driver’s license information with the app
When one user on the private iMoney Facebook group tried to cash out, they were asked for their license. This user questioned the requirement as well as the suggestion that users can “watermark” the photo or cover their name and private information. The user shared a screenshot in which the iMoney developers insisted on a “clear photo” in order to “better pass the audit.”
![]()
Message thread between iMoney Support and one of their users about ensuring their driver’s license information isn’t “blocked”
Additionally, the application asks users to install a mobile device management (MDM) profile on their devices.
![]()
The iMoney applications ask users to install a mobile device management certificate on their device
Pop-up banners claim this is an “Official Certification from Apple” to “prevent account loss, secure iMoney balance, and get more tasks.” They say this certificate “has been officially certified by Apple and is only used for the legality checking of Apple devices.” This claim is false. MDM is an approved mechanism that Apple provides, but that does not mean this particular certificate has been “certified” by Apple.
![]()
Details of the fake Apple mobile device management certificate required to continue using the iMoney application
MDM profiles are typically used by businesses to manage and monitor devices. The fact that iMoney app makers are asking users to install an MDM profile in order for “legality checking” is a highly dangerous prospect and should sound alarm bells for users. There are reports of other applications abusing this business solution to trick users into installing pirated games.
A perusal of social media sites reveals that the iMoney developers largely distributed their application via MDM profiles in the past to skirt App Store guidelines. However, since that cumbersome process hinders their ability to rope in new users, they have since begun distributing their application to a wider audience by creating and uploading fake applications to the Apple App Store.
Several iMoney applications masquerading in the App Store
The Super Expense app isn’t the only fake application that iMoney is hidden behind on the App Store. I found at least five applications, some of which were promoted through TikTok ads or attributed to the same developer on the App Store. These include:
- DaysTaker
- CanEnrich
- OlMoneing
- Minimalist part-time
TikTok ads for these apps also used false advertising, claiming users could earn $10 for completing a task. As we outlined earlier, this isn’t the case, as the most basic task of downloading an app could earn a user a mere 23 cents.
![]()
TikTok advertisements with misleading promotions of $10 rewards for completing tasks, or ways to “get fast free money online”
All of these applications masqueraded as something completely different in the Apple App store.
![]()
Four applications masquerading in the App Store that are shells for the iMoney application
According to rankings obtained from SensorTower, the CanEnrich app appears to have had the most success, reaching a ranking of #111 on Apple’s Lifestyle category on the App Store in March 2020. DaysTaker reached #151 in January 2020, while Super Expense reached #167 in April 2020.
2. “Free” offers that come with a price: diet pills and other suspect products and services
![]()
Example comment from TikTok user on an advertisement
Another area that I encountered during my research involved advertisements for products and services that were suspect in nature. The most egregious of these has been a steady stream of diet pill spam.
Diet pill spam has been on social media for over a decade now. I’ve researched similar campaigns on Twitter, Pinterest and Tumblr, so it’s not surprising to see them surface on TikTok — spammers tend to follow the users, after all. The diet pill advertisements I’ve encountered on TikTok have evolved over time. They initially used weight loss testimonials from YouTube influencers like VitalyzdTv and some other unidentified influencers.
![]()
TikTok advertisement features a YouTube influencer’s body transformation to promote a diet pill
The scammers took one of Vitaly’s popular videos with over four million views and repurposed part of it into an advertisement to promote a “Legal Steroid” that is “Turning Men Into Beasts Without Exercise.”
I also observed more comprehensive diet pill ads that included doctored video footage of celebrities like Oprah Winfrey, Blake Shelton and Kelly Clarkson appearing to endorse the products. The videos also featured a montage from the reality TV show “Shark Tank,” featuring footage of Mark Cuban, among others, consuming an undisclosed beverage.
![]()
Video stills from TikTok advertisements using fake celebrity endorsements including Oprah Winfrey, Dr. Oz, Blake Shelton, Kelly Clarkson and Mark Cuban
![]()
Fake articles promoting diet pills using the Fox News logo and false claims from notable figures
When users click on the advertiser’s name or the link to “Learn More,” they are redirected to a website that features fake articles purporting to be from popular news outlets like Fox News and CNN.
![]()
Fake articles promoting diet pills using the CNN News logo and false claims from notable figures
These websites continue to use the existing false celebrity endorsements or they add in new ones, particularly Dwayne “The Rock” Johnson and Kathy Bates. In the case of Kathy Bates, scammers used a pre-existing clip from Dr. Oz’s show and photoshopped an image of a bottle of weight loss pills into her hand.
![]()
Actual source of Kathy Bates clip used in the fake CNN article, which added a photoshopped image of a bottle of diet pills
Diving further into these fake news websites, if users click through to get their “free bottle” of pills, they’re met with a similar template.
![]()
Diet pill spam on TikTok uses the same template to promote three different pills
Above, you’ll see ads for three different “performance enhancer” pills that use the same basic template of a muscular guy, boilerplate text and a button that says “Rush My Bottle” at the bottom.
These aren’t the only pills I’ve seen promoted. I’ve also encountered ads promoting products using the term “Keto” to take advantage of the popular diet fad.
![]()
Diet pill spam capitalizing on interest in the keto diet, while using similar templates to promote different “Keto” pills
Once again, the scammers are utilizing templates for the keto pills, which include KetoFast and Rapid Keto Burn.
![]()
The purchase flow for these diet pills shows that if users don’t cancel before their trial period is over, they will be charged nearly $90
Once the scammers convince their victims to accept their “free bottle” of diet pills, the users will be asked to provide their address and payment information. They’ll be told they only have to pay for shipping and handling at a 50% discount. However, if users read the fine print, they’ll see that they’ve enrolled in a trial program that will charge them $90 if they don’t cancel after 14 days. They’re also enrolled in a recurring shipping program, so they’ll continue to receive these pills while also being charged each month until they’ve canceled.
![]()
Affiliate offer websites show that the Keto Fast diet pill offer could net a scammer over $100 for a conversion
So, what’s in it for the scammers? Well these websites are part of a cost-per-action (CPA) affiliate program. These programs require the scammers to convince their victims to complete an action in order to meet the CPA criteria. In this case, if the victim submits their credit card information and orders the pills, the scammers can earn close to $111 for each sale.
One way for a savvy user to circumvent dodgy ads would be to go directly to the domain without clicking through the ad. This is difficult for most TikTok ads, which typically use obscure advertiser names that conceal where they are hosted. However, in the case of diet pill spam on TikTok, several examples I encountered used the destination URL as the advertiser name. Many of these diet pill websites are hosted on alternative top level domains like .xyz, .shop and .club. When scammers use the domain name as part of the advertiser name, it saves the step of having to use a tool like Burp Suite to man-in-the-middle your mobile device and identify the destination URL. But if you try to examine one of these websites on a computer, you’re redirected to a different website, meaning the scammers have configured their sites to only accept traffic from mobile devices through the TikTok application.
Additionally, I’ve encountered a trend in which ads feature some fitness-oriented and diet-oriented pre-roll content at the beginning, such as Zumba, exercise machines, recipes or some type of floor workout. There are two possible reasons for this. Perhaps the pre-roll footage is designed to dupe the moderators who are responsible for vetting the advertisements, or perhaps it’s meant to capture the attention of those watching the ads, who may otherwise continue to scroll through the For You page.
![]()
Diet pill spam ads on TikTok feature some pre-roll footage to bypass content moderation or to capture the attention of users viewing the ads
Exploiting users through promises of free products
![]()
Example of a TikTok advertisement promoting free stuff, in this case showing the ways users can earn free money
There also have been a slew of TikTok advertisements promoting the promise of free goods and gift cards.
Free products and gift card scams aren’t really a new phenomenon, as I wrote about these almost a decade ago. However, they’re certainly new to TikTok. I encountered an advertisement promoting a platform called “You Review, You Keep.”
![]()
Example TikTok ad for the You Review, You Keep platform, claiming to offer a free PS4
The advertisement features a montage of people saying they received a free Playstation 4 (PS4) console just for reviewing the product (see example below). Some of the comments on the ad noted that similar actors featured in this advertisement were also used in a free Xbox promotion.
![]()
If users click on the link in the advertisement, they’re directed to a website that explicitly states that in order to get your “free” PS4, you have to “Complete ten deals.”
![]()
Website for the You Review, You Keep survey that requires users to complete “ten deals” before they can receive their PS4
Once the user completes the initial survey, they’re asked to provide an email address. It also states that by clicking “Continue,” the user agrees to the terms and conditions as well as “mandatory arbitration” with respect to You Review, You Keep. It’s worth noting that Consumer Reports has written about mandatory arbitration, saying it “deprives consumers of important options if a product is faulty or harmful.” This is important when you consider that consumers hoping to get their “free PS4” learn that it’s not free because it requires the completion of “ten deals” via affiliate offers that cost them money.
I also encountered a similar advertisement for free Apple AirPods. The website looks eerily similar to the one from You Review, You Keep. It instructs the user to “Complete ten deals” to get their AirPods. However, in none of the website images are they ever told that the AirPods will be free. In fact, when clicking on the “About our program” section at the bottom of the website, users are told that they have to “Complete your favorite ten deals (purchase required)” in order to get the AirPods.
![]()
A TikTok advertisement for free Apple AirPods that links to a similar looking survey website as You Review, You Keep
I also came across advertisements promoting $75 gift cards for popular brands like Chick-fil-A and Starbucks.
![]()
TikTok advertisements offering users a $75 gift card to Chick-fil-A and Starbucks
Once again, the sites for these gift cards look identical to the ones I’ve shared above for the PS4 and AirPods.
![]()
The website for the Chick-fil-A and Starbucks gift cards looks identical to the ones shared previously for You Review, You Keep and the Apple Airpods
Digging deeper into these sites, we can see that the program requirements are different for these gift cards because their dollar value is less than $100. Instead of having to complete 10 deals, users only have to complete four deals.
![]()
The fine print from the Chick-fil-A and Starbucks survey website shows that users need to complete four deals in order to get their gift card
However, users are still required to “complete” deals to get their Chick-fil-A or Starbucks gift card, which just underscores how deceptive these advertisements are. They make bold claims about free stuff, but in reality they string consumers along into signing up for trial offers or purchasing other products in order to get their so-called free products.
3. Promoting the sale of questionable dropshipped products
Considering the popularity of TikTok, it makes sense that scammers would try to leverage the fast-growing platform to promote dropshipped goods. Earlier this year, I observed dropshipping scams on Instagram that circumvented Facebook’s advertising ban on masks. Dropshipping is a big business opportunity, so much so that popular e-commerce solution Shopify provides a guide on how to dropship.
![]()
An infographic that explains how dropshipping works (Source: Shopify)
The problem isn’t with dropshipping itself — rather, it’s the scammers taking advantage of unsuspecting customers who are unaware of the true source of the products they’re purchasing and the actual cost of those products. Customers may end up getting the wrong product or may never receive the product at all.
![]()
Examples of TikTok advertisements promoting a variety of knock-off massage guns
One of the first batches of dropshipped goods I encountered were massage guns. Several different sellers were promoting them, including one named Hypervolt. This is interesting when you consider that Hyperice is a company that produces a product called the Hypervolt. However, a quick visit to hyperice.com shows a clear discrepancy in the prices between the product being promoted through TikTok and what’s actually offered by Hyperice.
![]()
Examples of TikTok advertisements promoting dropshipped goods
Besides the knock-off massage guns, the types of dropshipped goods being promoted vary, including electronics, hardware, kitchen tools, clothing and accessories.
![]()
Examples of TikTok advertisements promoting dropshipped goods
All of these advertisements lead users to Shopify-hosted websites promoting these goods.
![]()
TikTok ads for dropshipped goods lead to Shopify-hosted websites where purchases are made
These sites promote the goods through their own branded Shopify websites and sell them at a markup. However, they don’t keep the inventory themselves. They source their orders through a website like AliExpress, where these goods can be obtained for a steep discount.
![]()
Examples of goods sold on AliExpress for lower cost than advertised in TikTok ads
While all dropshippers will mark up prices to some extent, the ads we’re highlighting veer into the territory of price gouging, with prices for these goods ranging from 60% to 100% above typical retail. They have the goods delivered directly to their customers from the actual suppliers in other countries, including China, Russia, Spain and France. Because the items are shipped from overseas, they can take quite some time to arrive in the U.S. It’s the nature of dropshipping that this also leads to the questionable quality of the goods, since they cannot be verified by the seller.
![]()
Comment from a Reddit user about their experience ordering an item from a TikTok ad
For example, I found a thread on Reddit about a fake TikTok advertisement promoting a gaming chair. A user commented on this post saying that when they tried to purchase one of these chairs, they received a $3 phone stand instead. They also placed an order for a second chair before receiving the first one. Unsurprisingly, the second item was another phone stand. They concluded their comment with this warning: “NEVER ORDER FROM TIKTOK ADS THEY CLEARLY DONT SCREEN!”
While legitimate advertisers are certainly present on TikTok, the sheer number of scams I’ve observed compels me to advise users to be cautious about making purchases without first attempting to verify the source and to see if the item they’re about to purchase can’t be obtained directly from AliExpress at a deeper discount.
4. Dodgy credit repair and tuition assistance offers
Finally, I encountered a group of TikTok advertisements targeting users with credit repair and tuition assistance services.
When it comes to credit repair, the primary types of ads I encountered on TikTok included “celebrity endorsements” in the form of rapper and media personality Snoop Dogg, businesswoman Tina Lawson (who is Beyonce’s mother) and musician and TV personality Randy Jackson.
![]()
TikTok advertisements promoting credit repair using videos of notable celebrities and figures
The ads begin with these so-called “endorsements” but continue on with paid actors promoting a website for the Finance Council, a company that promises to help lower your credit score with just a 15-minute phone call. (See example below.)
![]()
These endorsements appear to be recycled from previous so-called debt relief and credit repair companies. Snoop Dogg was seen promoting such programs in advertisements on Facebook in 2019. In February, an article was published discussing Beyonce’s mom promoting the Finance Council through Snapchat advertisements. That article also points to a story in the New York Times cautioning against debt relief or credit repair companies. It’s likely that sites like the Finance Council capture personally identifiable information from those seeking to improve their credit scores, and may try to sell the users some type of service to improve their credit score. However, what that service entails is unclear.
![]()
The website for one of these credit repair programs features an image of Snoop Dogg, but the fine print mentions that the figures shown “may not be associated with the product or service advertised.”
Despite utilizing these celebrity endorsements, the website notes at the very bottom of the page in fine print that these figures “may not be associated with the product or service advertised.” In the case of the Snoop Dogg advertisements that were found on Facebook, VICE News notified Facebook, who found that these ads violated their advertising policies. If they’re in violation on Facebook, they should certainly be in violation on TikTok.
In addition to Lawson’s likeness being used in ads, another group, called Health Insurance Hero, used a pre-recorded video to promote “lower health insurance plans,” once again through a 15-minute phone call.
![]()
In addition to using her likeness to promote the Finance Council, a group called Health Insurance Hero features Ms. Lawson in a TikTok advertisement as well as her daughter Beyonce on their website
The website for Health Insurance Hero looks similar to the one for Finance Council, which leads me to believe that the operators of both sites are either the same or using the same template.
Degree Explore claims to offer users $6,000 for “financial aid”
I’ve also encountered ads from Degree Explore promoting sites offering users “financial aid” for college, sometimes specifically referencing online classes. They claim users could get paid over $6,000 to take classes online.
![]()
TikTok advertisements promoting ways users can receive “Financial Aid” or get paid to take “Online Classes”
Based on details from the Degree Explore websites, it appears that these offers simply facilitate the application for Federal Pell Grants. These websites are largely designed to collect personally identifiable information from users, which the site owners can then sell. They share this information with partner schools, who give them a kickback for the referrals.
What they don’t tell these students upfront is that several factors come into play when it comes to the grant amount. The Federal Student Aid website says that the exact amount one can expect to receive “Depends on your financial need, the cost of attendance at your school, and more.” Therefore, the claim that all users could earn $6,000 for classes is misleading.
![]()
One of the websites from the TikTok advertisements for financial aid details in fine print that these websites receive “revenue from some of the schools that we review” and provides more details about the $6,000 figure
The Federal Student Aid website has a dedicated section on student aid scams. They caution users that they should “never have to pay for help” with their “federal financial aid or student loans,” and advise prospective students to “understand which companies and claims are legitimate.”
TikTok ad scams: Lessons to be learned
As I’ve outlined throughout this blog and my past research into TikTok, a surge in popularity inevitably brings challenges when it comes to moderating content and combating abuse. Over the course of the past decade, I’ve documented these challenges on Facebook, Twitter, Instagram, Snapchat and others as each of these platforms began to emerge as popular destinations for users.
TikTok is no different, which is why it is important for ByteDance — and any new U.S. owner — to prioritize upleveling the app’s content moderation and abuse team in order to curtail these types of questionable ad practices.
There’s ample room for improvement. For example, TikTok’s current functionality for reporting suspicious ads requires the user to provide additional information, including screenshots. This time consuming requirement might deter users from filling out these reports, which would give scammers additional time to run their advertisements.
For users of TikTok, it’s important to recognize that scammers are opportunistic individuals. Scammers see users as a means to an end – the goal is to prey on consumer insecurities and desires to earn fast money, get a good deal on a hot product, lose weight without working out or relieve credit card debt. While we all wish it weren’t so, the reality is there’s no easy way to accomplish these things. TikTok users would do well to be skeptical of many of the advertisements on the platform, because at the end of the day, they’re not always what they appear to be.
Tenable shared our findings with Amazon, Apple, Facebook and TikTok. Amazon confirmed it is “reviewing the report.” Apple removed the iMoney applications from the App Store. TikTok confirmed receipt and responded that it will “direct this to the right person on our team to review.”
Learn More:
- See more from this author here
- Learn more about Tenable Research here
- Read our previous blogs about TikTok social media scams:
- TikTok Scams: How Popular Apps and Services Become New Havens for Scammers
- TikTok Scams: How Social Currency Fuels the Economy for Impersonation Accounts and Free-Followers-and-Likes Services