Microsoft addresses 117 CVEs in its April 2022 Patch Tuesday release, including two zero-day vulnerabilities, one of which was exploited in the wild and reported to Microsoft by the National Security Agency.
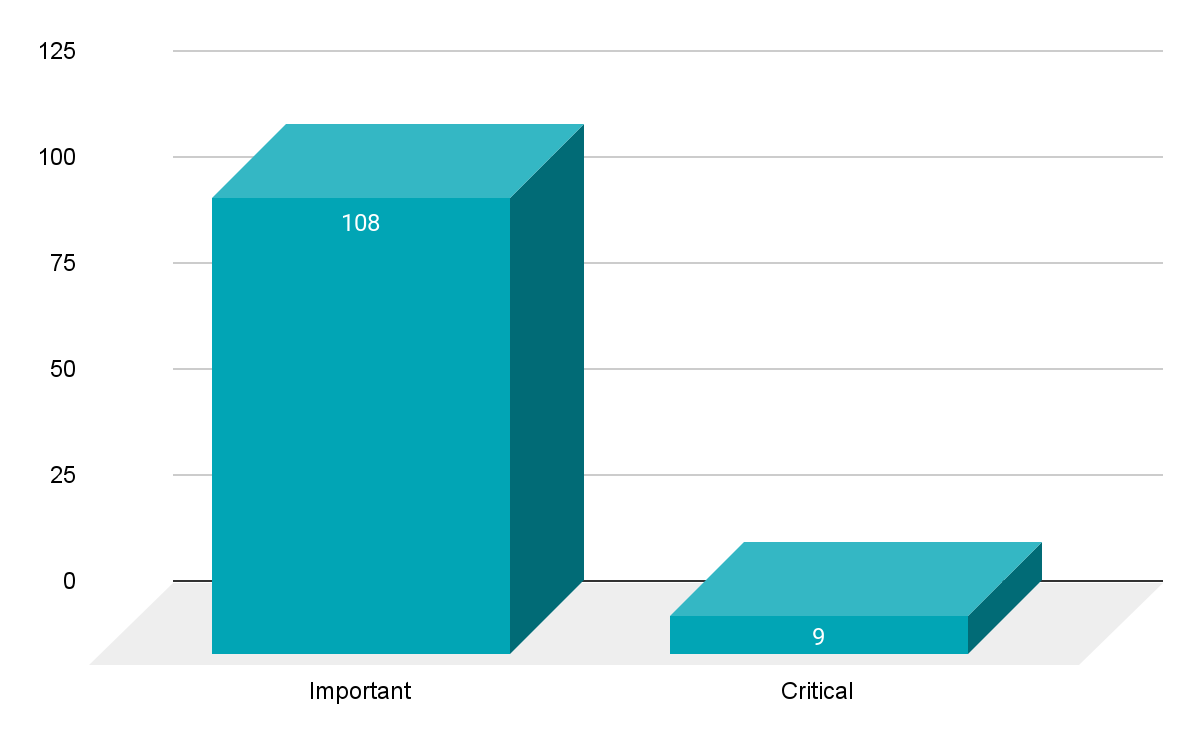
- 9Critical
- 108Important
- 0Moderate
- 0Low
Microsoft patched 117 CVEs in its April 2022 Patch Tuesday release, with 9 rated as critical and 108 rated as important.
This month’s update includes patches for:
- .NET Framework
- Active Directory Domain Services
- Azure SDK
- Azure Site Recovery
- LDAP - Lightweight Directory Access Protocol
- Microsoft Bluetooth Driver
- Microsoft Dynamics
- Microsoft Edge (Chromium-based)
- Microsoft Graphics Component
- Microsoft Local Security Authority Server (lsasrv)
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft Windows ALPC
- Microsoft Windows Codecs Library
- Microsoft Windows Media Foundation
- Power BI
- Role: DNS Server
- Role: Windows Hyper-V
- Skype for Business
- Visual Studio
- Visual Studio Code
- Windows Ancillary Function Driver for WinSock
- Windows App Store
- Windows AppX Package Manager
- Windows Cluster Client Failover
- Windows Cluster Shared Volume (CSV)
- Windows Common Log File System Driver
- Windows Defender
- Windows DWM Core Library
- Windows Endpoint Configuration Manager
- Windows Fax Compose Form
- Windows Feedback Hub
- Windows File Explorer
- Windows File Server
- Windows Installer
- Windows iSCSI Target Service
- Windows Kerberos
- Windows Kernel
- Windows Local Security Authority Subsystem Service
- Windows Media
- Windows Network File System
- Windows PowerShell
- Windows Print Spooler Components
- Windows RDP
- Windows Remote Procedure Call Runtime
- Windows schannel
- Windows SMB
- Windows Telephony Server
- Windows Upgrade Assistant
- Windows User Profile Service
- Windows Win32K
- Windows Work Folder Service
- YARP reverse proxy
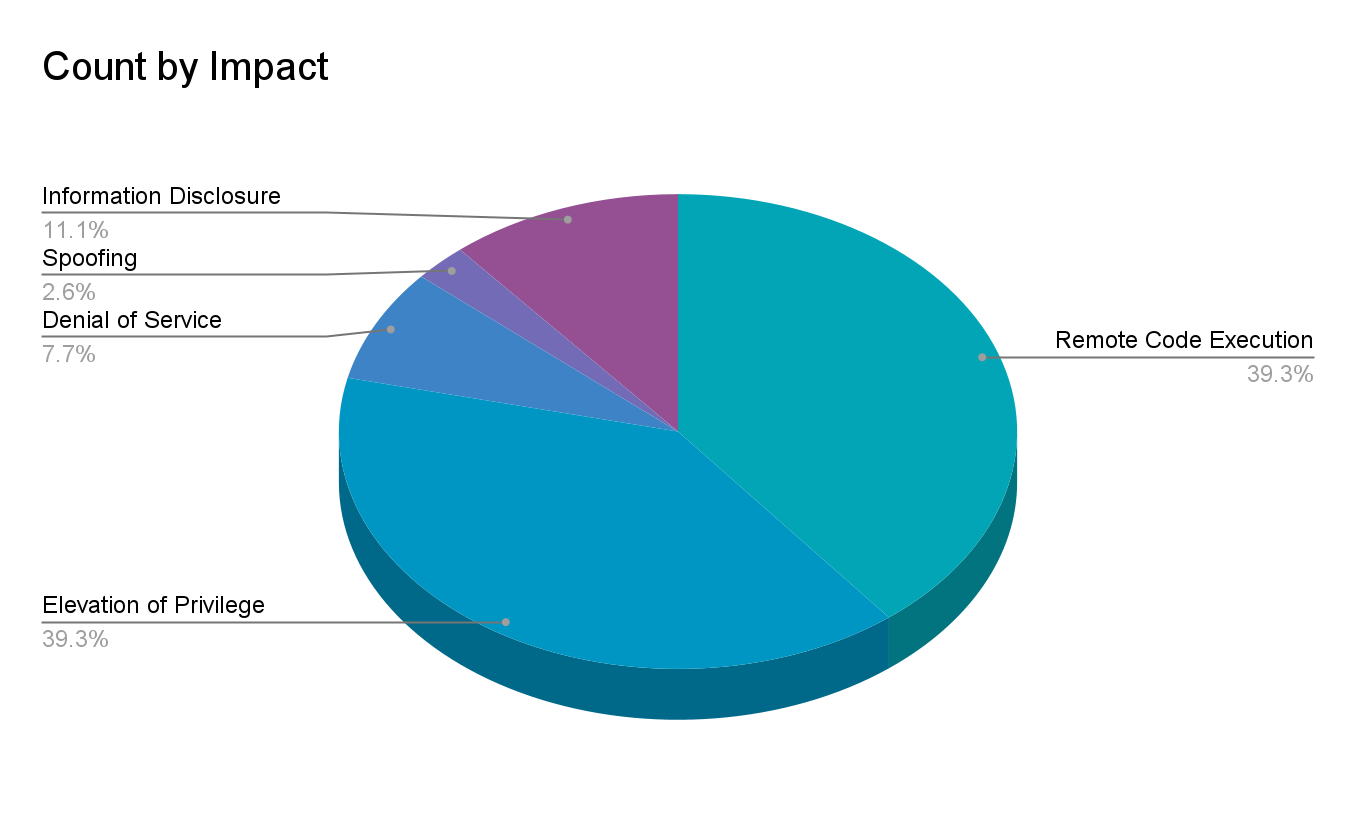
Elevation of privilege (EoP) vulnerabilities accounted for 39.3% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 39.3%.
CVE-2022-24521 and CVE-2022-24481 | Windows Common Log File System Driver Elevation of Privilege Vulnerabilities
CVE-2022-24521 is an EoP vulnerability in the Windows Common Log File System (CLFS) driver for Microsoft Windows. EoP flaws like this one are leveraged post-authentication, after an attacker has successfully accessed a vulnerable system, to gain higher permissions. According to Microsoft, this flaw has been exploited in the wild as a zero-day, though we do not have any additional details about its exploitation. We do know that it was reported to Microsoft by the National Security Agency along with researchers at CrowdStrike. Organizations should ensure they apply the available patches as soon as possible. CVE-2022-24481 is another EoP in the CLFS driver that received the same CVSSv3 score of 7.8 and was rated “Exploitation More Likely” according to Microsoft’s Exploitability Index. However, it is not a zero-day.
CVE-2022-26904 | Windows User Profile Service Elevation of Privilege Vulnerability
CVE-2022-26904 is an EoP vulnerability in the Windows User Profile service. It received a CVSSv3 score of 7.0, which rates its severity as important. The attack complexity for this flaw is considered high because it “requires an attacker to win a race condition.” Despite the higher complexity, it is still considered as “Exploitation More Likely.” This is the second of two zero-days addressed this month, as details about this vulnerability were publicly disclosed prior to a patch being made available.
CVE-2022-24491 | Windows Network File System Remote Code Execution Vulnerability
CVE-2022-24491 is a critical RCE vulnerability in the Windows Network File System (NFS) that received a CVSSv3 score of 9.8 and a rating of “Exploitation More Likely.” An unauthenticated, remote attacker could exploit this vulnerability by sending specially crafted NFS protocol network messages to a vulnerable system. Only systems with the NFS role enabled are at risk for exploitation; however, organizations should still apply the patch to all systems to ensure they are protected.
CVE-2022-26809 | Remote Procedure Call Runtime Remote Code Execution Vulnerability
CVE-2022-26809 is a critical RCE vulnerability in the Remote Procedure Call (RPC) runtime. It received a CVSSv3 score of 9.8. An unauthenticated, remote attacker could exploit this vulnerability by sending “a specially crafted RPC call to an RPC host.” Patching is the best approach to fully address this vulnerability; however, if patching is not feasible, Microsoft recommends blocking TCP port 445 on the perimeter firewall to mitigate attempts to exploit this flaw. Despite applying this mitigation, systems could “still be vulnerable to attacks from within their enterprise perimeter.”
CVE-2022-26817 and CVE-2022-26814 | Windows DNS Server Remote Code Execution Vulnerabilities
CVE-2022-26817 and CVE-2022-26814 are RCE vulnerabilities in Windows DNS Server affecting Active Directory Domain Services that both received a CVSSv3 score of 6.6 and were discovered by Yuki Chen with Cyber KunLun. Exploitation of this vulnerability is rated “Less Likely” which may be tied to the higher attack complexity and required permissions. To successfully exploit this flaw, an attacker on the target network with permissions to query the domain name service must win a race condition. Only if they perfectly time exploitation of this vulnerability, can they achieve RCE. Patches have been released for supported versions for Windows Server and Windows Server Core installations.
15 Elevation of Privilege Vulnerabilities in Windows Print Spooler
This month, Microsoft patched 15 EoP vulnerabilities in Print Spooler components all of which received CVSSv3 scores of 7.8. Three of the vulnerabilities were disclosed by George Hughey of Microsoft Security Response Center Vulnerabilities and Mitigations and the other 12 were disclosed by Microsoft Offensive Research and Security Engineering. While Microsoft rates these vulnerabilities as “Exploitation Less Likely,” attackers have exploited EoP flaws in Print Spooler in the past.
Upcoming end of support
In the coming weeks, versions of the.NET Framework and Windows 10 will stop receiving updates and support. On April 26, .NET Framework 4.5.2, 4.6, or 4.6.1 will reach end of support due to their use of the less secure Secure Hash Algorithm 1 (SHA-1). On May 10, Windows 10 version 20H2 will reach end of servicing. Users are urged to update to more recent versions to ensure they continue receiving important security updates.
Tenable Solutions
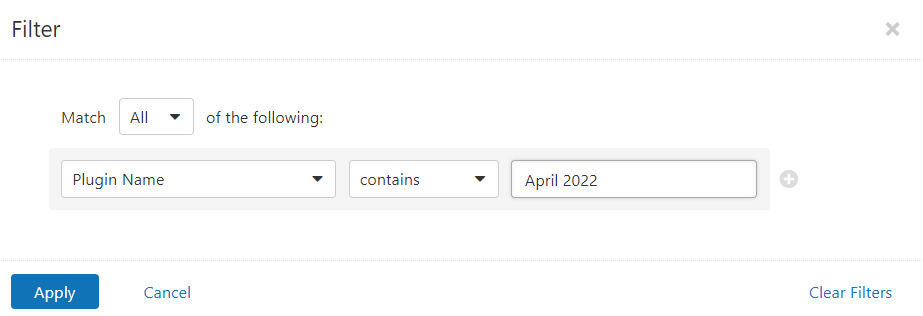
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains April 2022.
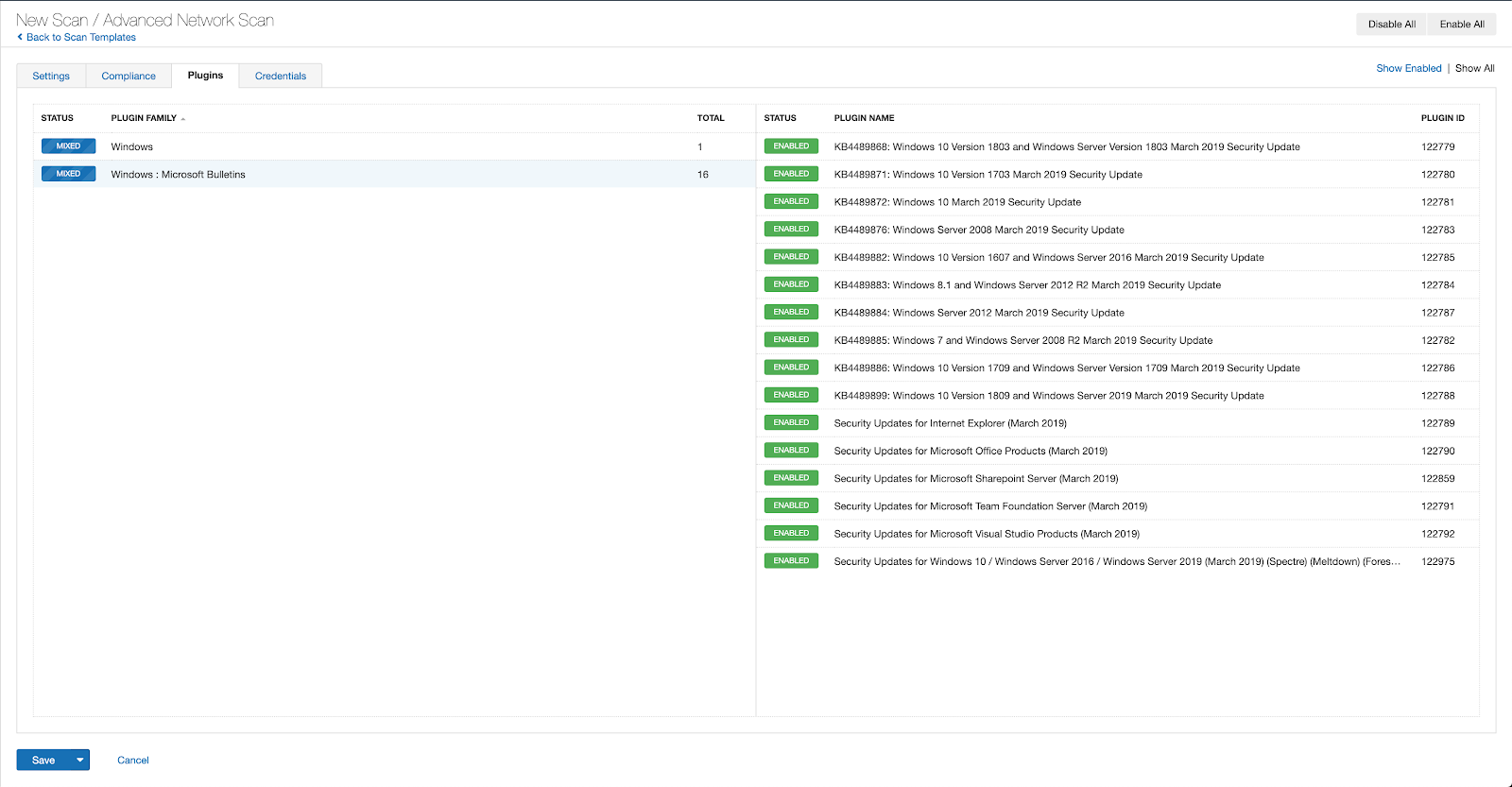
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
A list of all the plugins released for Tenable’s April 2022 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's April 2022 Security Updates
- Tenable plugins for Microsoft April 2022 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.