An expanding attack surface demands a robust cybersecurity strategy. Here’s what you need to know.
The shift to remote work over the past two years would not have been possible without cloud computing, which enables employees to access data and services from anywhere at any time. Yet, many organizations still face challenges in deploying and managing their cloud infrastructures in a security-conscious way.
A study commissioned by Tenable and conducted by Forrester Consulting found that, prior to the pandemic, 31% of business and security leaders had moved business-critical functions to the cloud and 48% had moved non-critical functions. The pandemic accelerated this move and over the next two years, 20% of respondents say they will make the switch to cloud for business-critical assets.
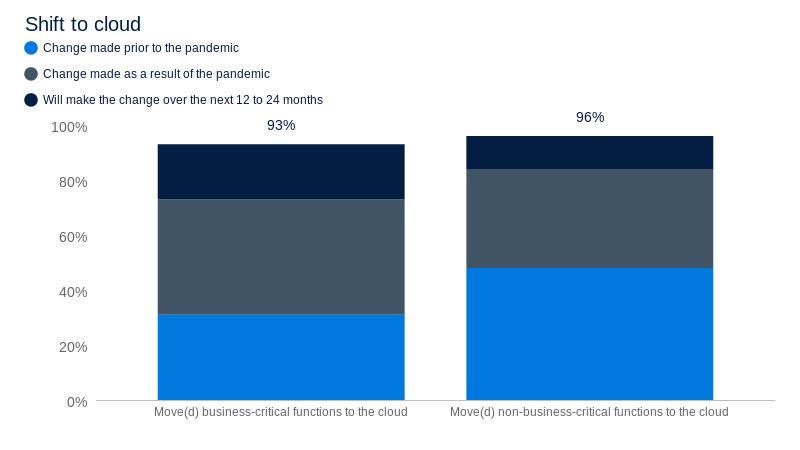
Source: A commissioned study conducted by Forrester Consulting on behalf of Tenable, April 2021.
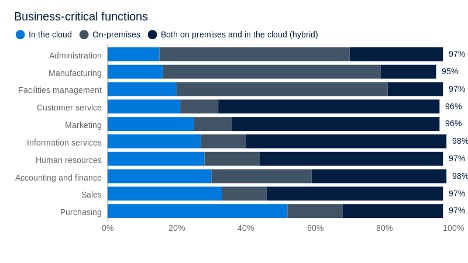
Source: A commissioned study conducted by Forrester Consulting on behalf of Tenable, April 2021.
Several core challenges further emphasize the need for a security-first strategy in the cloud:
- The dissolving perimeters introduced by cloud solutions. Heavily dynamic by design, cloud solutions break down typical security perimeters, which are sustainable only when IT systems are run entirely on-premises.
- The critical nature of cloud assets. The cloud is becoming an integral component of supply chain technologies, internet of things (IoT), artificial intelligence (AI), and infrastructure as code (IaC) as the world rapidly shifts towards “everything-as-a-service”
- The rapidly evolving threat landscape. The ease of interconnecting devices, flows and data that cloud technologies offer comes with the burden of increasing the attack surface. As a consequence, the security posture of any company cannot be reactive any longer. The lack of visibility introduced by cloud technologies, combined with the need for privacy compliance, requires companies migrating to the cloud to shift their mindset from a perimeter-based security approach to a data-driven one, while ensuring a proactive, holistic, end-to-end yet dynamic security program.
- The potential for cloud vendor lock-in. Choose your cloud vendors wisely. It can be difficult to switch cloud providers once you’ve established; doing so can introduce performance, compatibility and security complications.
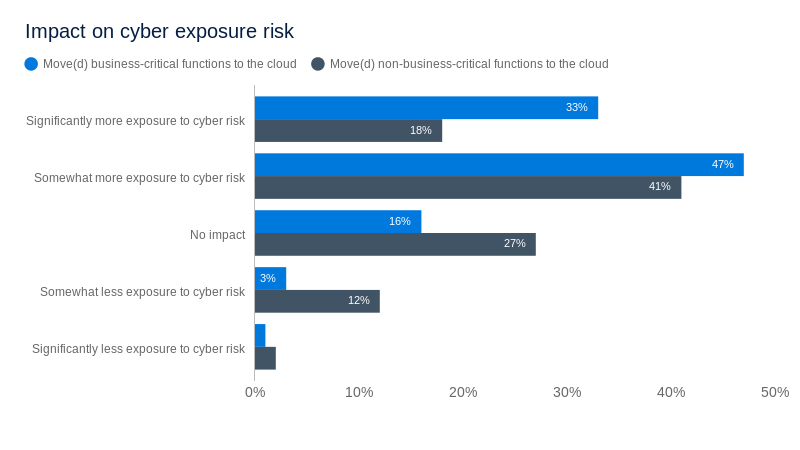
Source: A commissioned study conducted by Forrester Consulting on behalf of Tenable, April 2021.
The image below shows the complexities of cloud migration. Broadly speaking, a successful cloud migration involves a breadth and depth of dimensions, including consideration of policies, compliance requirements and overarching risks to processes and operations. Each of hese elements needs to be considered in order to effectively manage data, operations and resources while enabling the business to operate in a cost-aware manner.
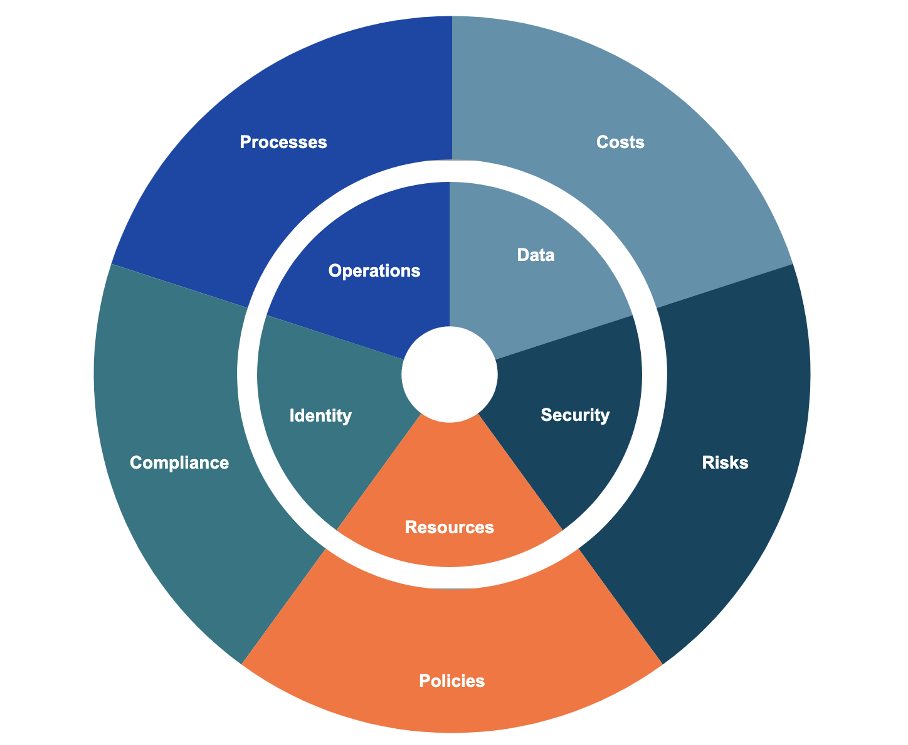
Source: Tenable, April 2022
Below, we highlight three key areas of focus that can be taken into account to mitigate the cybersecurity blind spots that arise from migration to the cloud.
1. Perform a risk assessment
When shifting to the cloud, businesses enter into a shared responsibility model, in which cloud provider and cloud user are both accountable for security obligations to the degree dictated by the distribution model (i.e., IaaS, PaaS or SaaS).
Cloud risk assessment helps in evaluating and avoiding unidentified or new risks introduced by migrating systems and data. Nothing is ever completely risk-free. The goal with a risk assessment is to identify all potential risk areas and weigh them against business need to arrive at an acceptable level of risk tolerance for each area.
Risk analysis needs to span multiple areas, including:
- assessing cloud providers’ risk and potential vendor lock-in;
- risks introduced by loss of governance; and
- compliance needs.
These areas are critical in the cloud environment and each carries its own sub-list of related risks that need to be accounted for, such as technical, costs, resource allocation, operational processes and procedures, security and legal constraints.
2. Factor in cloud security governance
Cloud security governance entails building models for effective security operations in the cloud, assisting leaders in better understanding security risks and how to progressively reduce them in pursuit of strategic alignment and value delivery — all while fostering a security-aware culture.
Cloud security governance aims at:
- Strategic alignment between business goals and mandated security investments.
- Progressive risk reduction due to implemented and monitored security initiatives, with an eye towards sustainable performance.
- Proper role management and resource allocation to security initiatives.
The route to proper cloud security governance depends on a company’s relative maturity. It should, at minimum:
- Consider security investments as part of the overarching business goals and strategic alignment.
- Set forth measurable security initiatives in pursuit of risk reduction, value delivery and performance.
- Ensure appropriate staffing and know how to perform security initiatives and operations.
3. Conduct a data protection impact assessment
Performing Data Protection Impact Assessment (DPIA) can help mitigate risks identifying and addressing high-risk scenarios before any data processing takes place. While required by law under certain conditions, a data protection impact assessment is worth performing regardless of legal requirements; the effort can help to maximize adherence to security and privacy best practices, hence minimizing potential liabilities.
When handling data, best practices include:
- Removal of personally identifiable factors from your information as much as is feasible.
- Having a strategy in place to identify and manage critical vulnerabilities to reduce the risk of data breaches.
- Working with cloud vendors to clarify the incident response support they’ll provide so that the organization is well-prepared to handle cybersecurity events that might occur.
In addition to the above, logging and monitoring are critical components of effective cloud security. The practice becomes even more crucial in the event of an incident. Cloud vendors should be assessed on the terms they offer for access and management of log trails. In addition, security operation teams need a continuous monitoring strategy to proactively assess the environment and provide a rapid response in cases of anomalous behavior.
Conclusion
The areas of focus discussed above barely scratch the surface of the myriad security implications of cloud migration and adoption. While organizations have found a lift-and-shift strategy to be an effective way to migrate applications, services and data to the cloud, it’s not an approach that works for cloud security. Instead, organizations need to have an overarching and proactive strategy for securing cloud applications and services that starts well before any migrations get underway.
Effective cloud security requires a holistic approach that includes performing due diligence on all third parties, dis-identifying data and creating sensible SLAs. All leaders — not just security professionals but also IT and business leaders — must proactively embrace cybersecurity as a fundamental condition to ensure longevity of their businesses. Last, but not least, remediate, remediate, remediate: your business depends on it. Regular vulnerability assessment and automated remediation are key to a successful security strategy for the cloud.
Learn more
- Read the study, Beyond Boundaries: The Future of Cybersecurity in the New World of Work
- Read the blogs
- Visit the Tenable.cs product page to learn more about our capabilities: https://www.tenable.com/products/tenable-cs